About the connector
FortiEDR protects endpoints pre- and post-infection, stops data breaches in real time, and automatically orchestrates incident investigation and response.
This document provides information about the Fortinet FortiEDR Connector, which facilitates automated interactions, with your Fortinet FortiEDR server using FortiSOAR™ playbooks. Add the Fortinet FortiEDR Connector, as a step in FortiSOAR™ playbooks and perform automated operations such as retrieving events from Fortinet FortiEDR, searching for a file hash among the current events, threat hunting repository, and communicating applications that exist in the Fortinet FortiEDR system, and isolating a collector from the Fortinet FortiEDR network
Use the Data Ingestion Wizard to ingest data into FortiSOAR™ by pulling events from Fortinet FortiEDR. Currently, "events" in Fortinet FortiEDR are mapped to "alerts" in FortiSOAR™. For more information, see the Data Ingestion Support section.
Version information
Connector Version: 1.3.1
FortiSOAR™ Version Tested on: 7.3.1-2105
Fortinet FortiEDR Version Tested on: 4.1.1.95
Authored By: Fortinet
Certified: Yes
Release Notes for version 1.3.1
The following enhancements have been made in the Fortinet FortiEDR connector in version 1.3.1:
- Added the 'Timezone' parameter to the 'Fetch Data' screen of the Data Ingestion Wizard.
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the following yum command as a root user to install connectors from an SSH session:
yum install cyops-connector-fortinet-fortiedr
Prerequisites to configuring the connector
- You must have the URL of the Fortinet FortiEDR server to which you will connect and perform automated operations and credentials (username-password pair) to access that server.
- Users who have to use the Fortinet FortiEDR must be assigned a role with "REST API Access".
- To access the FortiSOAR™ UI, ensure that port 443 is open through the firewall for the FortiSOAR™ instance.
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here.
Configuration parameters
In FortiSOAR™, on the Content Hub (or Connector Store) page, click the Manage tab, and then click the Fortinet FortiEDR connector card. On the connector popup, click the Configurations tab to enter the required configuration details.
| Parameter |
Description |
| Server URL |
URL of the Fortinet FortiEDR server to which you will connect and perform the automated operations. |
| Username |
Username that contains a Rest API role and using which you will access the Fortinet FortiEDR server to which you will connect and perform the automated operations.
Note: The username must contain the FortiEDR TenantID in the following format: <TenantID>\username |
| Password |
Password used to access the FortiEDR server to which you will connect and perform the automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not.
By default, this option is set as True. |
Actions supported by the connector
The following automated operations can be included in playbooks, and you can also use the annotations to access operations from version 4.10.0 onwards:
| Function |
Description |
Annotation and Category |
| Get Event by ID |
Retrieves a specific event from Fortinet FortiEDR based on the event ID you have specified. |
get_event_list
Investigation |
| Get Events |
Retrieves all the events from Fortinet FortiEDR that match the condition(s) you have specified.
Note: If none of the input parameters that you specify match the events in Fortinet FortiEDR, then an empty result set is returned. |
get_event
Investigation |
| Update Events |
Updates events in Fortinet FortiEDR that match the condition(s) you have specified.
Note: If none of the input parameters that you specify match the events in Fortinet FortiEDR, then an empty result set is returned. |
update_event
Investigation |
| Get Raw Data Items |
Retrieves the raw data items from Fortinet FortiEDR based on the event ID and other input parameters you have specified. |
get_raw_data_items
Investigation |
| Get Event Count |
Retrieves the event count from Fortinet FortiEDR based on the filter parameters you have specified. |
get_event_count
Investigation |
| Get Event List Extended |
Retrieves archived/unarchived events together from Fortinet FortiEDR based on the filter parameters you have specified.
Note: If none of the input parameters that you specify match the events in Fortinet FortiEDR, then an empty result set is returned. |
get_event_list
Investigation |
| Search Filehash |
Searches a file hash among the current events, threat hunting repository, and communicating applications that exist in the Fortinet FortiEDR system. |
search_filehash
Investigation |
| Get File |
Retrieves a specific file from the specified device from Fortinet FortiEDR, based on the device type, device name/ID, and file paths you have specified, and adds it as an attachment in the "Attachments" module |
get_file
Investigation |
| Retrieve File or Memory |
Retrieves a file or memory related to a specific event from Fortinet FortiEDR based on the raw event ID and other input parameters you have specified and adds it as an attachment in the "Attachments" module. |
get_event_file
Investigation |
| Remediate Device |
Takes remedial actions on Fortinet FortiEDR such as killing a process, deleting a file and/or cleaning persistent data on which malware was detected based on the device type, device name/ID, and other input parameters you have specified. |
remediate_device
Remediation |
| Get Collector List |
Retrieves the list of the collectors from Fortinet FortiEDR based on the device names or IDs, and other input parameters you have specified. |
get_collector_list
Investigation |
| Isolate Collector |
Isolates a collector from the Fortinet FortiEDR network based on the list of device IDs or names, and other input parameters you have specified. |
isolate_collector
Investigation |
| Unisolate Collector |
Unisolates a collector from the Fortinet FortiEDR network based on the device ID and other input parameters you have specified. |
isolate_collector
Investigation |
| Create Exception |
Creates a new exception in Fortinet FortiEDR based on the event ID and other input parameters you have specified. |
create_exception
Investigation |
| Get Exception List |
Retrieves the list of all exceptions or specific exceptions from Fortinet FortiEDR based on the input parameters you have specified. |
list_exception
Investigation |
| Update Exception |
Updates a specific exception in Fortinet FortiEDR based on the event ID, exception ID, and other input parameters you have specified. |
update_exception
Investigation |
| Get Event Exceptions |
Retrieves the list of event exceptions from Fortinet FortiEDR based on the event ID and other input parameters you have specified. |
get_event_exceptions
Investigation |
| Get Raw JSON Event Data |
Retrieve the raw data of specific events from Fortinet FortiEDR based on the event ID and other input parameters you have specified. |
get_raw_json_event_data
Investigation |
| Create IPSet |
Creates an IPSet in Fortinet FortiEDR using the set of IP addresses and other parameters you have specified. |
create_ipset
Investigation |
| Get IPSet List |
Retrieves a list of IPSets from Fortinet FortiEDR based on the IP address and other input parameters you have specified. |
get_ipset_list
Investigation |
| Update IPSet |
Updates IP addresses in the specific IPSet in Fortinet FortiEDR using the set of IP addresses, the IPSet name, and other parameters you have specified. |
update_ipset
Investigation |
| Delete IPSet |
Deletes specific IPSets from Fortinet FortiEDR based on the IPSet names and other input parameters you have specified. |
delete_ipset
Investigation |
| Get Agent Groups |
Retrieves a list of all agent group lists from Fortinet FortiEDR. |
get_agent_group
Investigation |
| Get System Summary |
Retrieves a summary of the environment from Fortinet FortiEDR. |
get_system_summary
Investigation |
operation: Get Event by ID
Input parameters
| Parameter |
Description |
| Event ID |
ID of the event that you want to retrieve from Fortinet FortiEDR.
Note: You can get event IDs using the "Get Events" action. |
Output
The output contains the following populated JSON schema:
{
"eventId": "",
"certified": "",
"archived": "",
"lastSeen": "",
"collectors": [
{
"operatingSystem": "",
"lastSeen": "",
"collectorGroup": "",
"ip": "",
"device": "",
"macAddresses": [],
"id": ""
}
],
"destinations": [],
"handled": "",
"processType": "",
"muted": "",
"muteEndTime": "",
"seen": "",
"comment": "",
"firstSeen": "",
"classification": "",
"loggedUsers": [],
"organization": "",
"rules": [],
"process": "",
"severity": "",
"processPath": "",
"action": ""
}
operation: Get Events
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Event IDs |
List of event IDs based on which you want to retrieve events from Fortinet FortiEDR. |
| Device Name |
Name of the device on which the events occurred that you want to retrieve from Fortinet FortiEDR. |
| Collector Groups |
List of collector groups whose collector had reported the events that you want to retrieve from Fortinet FortiEDR. |
| Operating System |
Name of the operating system of the devices on which the events occurred that you want to retrieve from Fortinet FortiEDR. |
| Device IPs |
List of IP addresses of the devices on which the events occurred that you want to retrieve from Fortinet FortiEDR. |
| MAC Addresses |
MAC addresses where the events occurred that you want to retrieve from Fortinet FortiEDR. |
| Filehash |
Hash signature of the main process of the event that you want to retrieve from Fortinet FortiEDR. |
| Process |
Name of the main process of the event that you want to retrieve from Fortinet FortiEDR. |
| Process Path |
Path of the processes related to the event that you want to retrieve from Fortinet FortiEDR. |
| First Seen From |
"From" date when the event that you want to retrieve from Fortinet FortiEDR, was seen for the first time. Use this parameter together with the "First Seen To" parameter to specify a date range. |
| First Seen To |
"To" date when the event that you want to retrieve from Fortinet FortiEDR, was seen for the first time. Use this parameter together with the "First Seen From" parameter to specify a date range. |
| Last Seen From |
"From" date when the event that you want to retrieve from Fortinet FortiEDR, was seen for the last time. Use this parameter together with the "Last Seen To" parameter to specify a date range. |
| Last Seen To |
"To" date when the event that you want to retrieve from Fortinet FortiEDR, was seen for the last time. Use this parameter together with the "Last Seen From" parameter to specify a date range. |
| Classification |
Classification of the events that you want to retrieve from Fortinet FortiEDR. Classification is a list of strings that contain one or more of the following values: Malicious, Suspicious, Inconclusive, Likely Safe, PUP, or Safe. |
| Actions |
Actions that were enforced on the events that you want to retrieve from Fortinet FortiEDR. You can choose from the following options: Block, Simulation Block, or Log. |
| Destinations |
Connection destination(s) of the events that you want to retrieve from Fortinet FortiEDR. |
| Rule |
Short rule name of the rule that triggered the events that you want to retrieve from Fortinet FortiEDR. |
| Logged in User |
Logged-in user associated with the events that you want to retrieve from Fortinet FortiEDR. |
| Seen |
True/False parameter indicating whether events that you want to retrieve from Fortinet FortiEDR were read/unread by the user operating the API. |
| Handled |
True/False parameter indicating whether events that you want to retrieve from Fortinet FortiEDR were handled/unhandled. |
| Signed |
True/False parameter indicating whether the event that you want to retrieve from Fortinet FortiEDR is signed/unsigned. |
| Muted |
True/False parameter indicating whether the event that you want to retrieve from Fortinet FortiEDR is muted/unmuted. |
| Organization |
Name of the organization whose associated events you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated events you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then this operation will retrieve data that is shared by all organizations.
|
| Archived |
True/False parameter indicating whether to include only archived events while retrieving events from Fortinet FortiEDR. By default, this is set as false. |
| Strict Mode |
True/False parameter indicating whether or not to perform strict matching on the search parameters while retrieving events from Fortinet FortiEDR. By default, this is set as false. |
| Page Number |
Page number from which you want to retrieve records. |
| Items Per Page |
Maximum number of events that this operation should return for the current page. Values supported are: Default "100" and Maximum "2000". |
| Sorting |
Name of the fields by which you want to sort the results retrieved by this operation. You can enter the fields in the following format: {"column1":true, "column2":false}. True indicates sorting in descending order. Results are sorted by the first field, then by the second field, and so on. |
Output
The output contains the following populated JSON schema:
{
"eventId": "",
"certified": "",
"archived": "",
"lastSeen": "",
"collectors": [
{
"operatingSystem": "",
"lastSeen": "",
"collectorGroup": "",
"ip": "",
"device": "",
"macAddresses": [],
"id": ""
}
],
"destinations": [],
"handled": "",
"processType": "",
"muted": "",
"muteEndTime": "",
"seen": "",
"comment": "",
"firstSeen": "",
"classification": "",
"loggedUsers": [],
"organization": "",
"rules": [],
"process": "",
"severity": "",
"processPath": "",
"action": ""
}
operation: Update Events
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Field to Update on Event |
Specify the one field to update as multiple updates are not allowed. You can select from the following values: Read, Handle, Archive, Classification, Mute, or Force Unmute.
- If you choose Read, then select True in the Mark as Read parameter to mark the event as read or unread in Fortinet FortiEDR.
- If you choose Handle, then you can specify the following parameters:
- Mark as Handled: Select True in the Mark as Handled parameter to mark the event as handled or unhandled in Fortinet FortiEDR.
- Add Comment: Free text to be added as a comment to the event that you are handling or unhandling in Fortinet FortiEDR. The event must be handled in order to accept comments (supported for version 2.6.4 and above).
- If you choose Archive, then specify True in the Archive Event parameter to mark the event as hidden or unhidden in Fortinet FortiEDR.
- If you choose Classification, then you can specify the following parameters:
- Classify Event: Classify the event by selecting one of the following values: Malicious, PUP, or Safe (supported in V2.7.3 and above).
- Add Comment: Free text to be added as a comment to the event that you are classifying in Fortinet FortiEDR. The event must be handled in order to accept comments (supported for version 2.6.4 and above).
- If you choose Mute, then you can specify the following parameters:
- Mute Event: Select True in the Mute Event parameter to mute or unmute the event in Fortinet FortiEDR.
- Mute Duration: Select the duration for which you want to mute or unmute the event in Fortinet FortiEDR. You can choose from the following values: Week, Month, Year, or Permanently.
- If you choose Force Unmute, then select the Forced to Unmute an Event parameter to force an event to be archived even when the event is muted in Fortinet FortiEDR.
|
| Event IDs |
List of event IDs based on which you want to update events in Fortinet FortiEDR. |
| Device Name |
Name of the device on which the events occurred that you want to update in Fortinet FortiEDR. |
| Collector Groups |
List of collector groups whose collector had reported the events that you want to update in Fortinet FortiEDR. |
| Operating System |
Name of the operating system of the devices on which the events occurred that you want to update in Fortinet FortiEDR. |
| Device IPs |
List of IP addresses of the devices on which the events occurred that you want to update in Fortinet FortiEDR. |
| Filehash |
Hash signature of the main process of the event that you want to update in Fortinet FortiEDR. |
| Process |
Name of the main process of the event that you want to update in Fortinet FortiEDR. |
| Process Path |
Path of the processes related to the event that you want to update in Fortinet FortiEDR. |
| First Seen From |
"From" date when the event that you want to update in Fortinet FortiEDR, was seen for the first time. Use this parameter together with the "First Seen To" parameter to specify a date range. |
| First Seen To |
"To" date when the event that you want to update in Fortinet FortiEDR, was seen for the first time. Use this parameter together with the "First Seen From" parameter to specify a date range. |
| Last Seen From |
"From" date when the event that you want to update in Fortinet FortiEDR, was seen for the last time. Use this parameter together with the "Last Seen To" parameter to specify a date range. |
| Last Seen To |
"To" date when the event that you want to update in Fortinet FortiEDR, was seen for the last time. Use this parameter together with the "Last Seen From" parameter to specify a date range. |
| Seen |
True/False parameter indicating whether events that you want to update in Fortinet FortiEDR were read/unread by the user operating the API. |
| Handled |
True/False parameter indicating whether events that you want to update in Fortinet FortiEDR were handled/unhandled. |
| Severities |
A severity value for the filter to match. An option with one of the following values: Critical, High, or Medium. |
| Destinations |
Connection destination(s) of the events that you want to update in Fortinet FortiEDR. |
| Actions |
Actions that were enforced on the events that you want to update in Fortinet FortiEDR. You can choose from the following options: Block, Simulation Block, or Log. |
| Rule |
Short rule name of the rule that triggered the events that you want to update in Fortinet FortiEDR. |
| Strict Mode |
True/False parameter indicating whether or not to perform strict matching on the search parameters while retrieving events from Fortinet FortiEDR. By default, this is set as false. |
| Classification |
Classification of the events that you want to retrieve from Fortinet FortiEDR. Classification is a list of strings that contain one or more of the following values: Malicious, Suspicious, Inconclusive, Likely Safe, PUP, or Safe. |
| Organization |
Name of the organization whose associated events you want to update in Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated events you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then this operation will retrieve data that is shared by all organizations.
|
| Muted |
True/False parameter indicating whether the event that you want to update in Fortinet FortiEDR is muted/unmuted. |
Output
The output contains the following populated JSON schema:
{
"eventId": "",
"process": "",
"processPath": "",
"processType": "",
"firstSeen": "",
"lastSeen": "",
"seen": "",
"handled": "",
"comment": "",
"certified": "",
"archived": "",
"severity": "",
"classification": "",
"destinations": [],
"rules": [],
"loggedUsers": [],
"organization": "",
"muted": "",
"muteEndTime": "",
"collectors": [
{
"lastSeen": "",
"ip": "",
"collectorGroup": "",
"macAddresses": [],
"id": "",
"device": "",
"operatingSystem": ""
}
],
"action": ""
}
operation: Get Raw Data Items
Input parameters
| Parameter |
Description |
| Event ID |
ID of the event that holds the raw data items that you want to retrieve from Fortinet FortiEDR. |
| Device Name |
(Optional) Name of the device on which the raw event that you want to retrieve from Fortinet FortiEDR occurred. |
| Collector Groups |
(Optional) List of collector groups whose collector had reported the raw events that you want to retrieve from Fortinet FortiEDR. |
| Operating System |
(Optional) Name of the operating system of the devices on which the raw events that you want to retrieve from Fortinet FortiEDR occurred. |
| Device IPs |
(Optional) List of IP addresses of the devices on which the raw events that you want to retrieve from Fortinet FortiEDR occurred. |
| MAC Addresses |
(Optional) MAC addresses where the raw events that you want to retrieve from Fortinet FortiEDR occurred. |
| Filehash |
(Optional) Hash signature of the main process of the raw event that you want to retrieve from Fortinet FortiEDR. |
| Process |
(Optional) Name of the main process of the raw event that you want to retrieve from Fortinet FortiEDR. |
| Process Path |
(Optional) Path of the processes related to the raw event that you want to retrieve from Fortinet FortiEDR. |
| First Seen From |
(Optional) "From" date when the raw event that you want to retrieve from Fortinet FortiEDR, was seen for the first time. Use this parameter together with the "First Seen To" parameter to specify a date range. |
| First Seen To |
(Optional) "To" date when the raw event that you want to retrieve from Fortinet FortiEDR, was seen for the first time. Use this parameter together with the "First Seen From" parameter to specify a date range. |
| Last Seen From |
(Optional) "From" date when the raw event that you want to retrieve from Fortinet FortiEDR, was seen for the last time. Use this parameter together with the "Last Seen To" parameter to specify a date range. |
| Last Seen To |
(Optional) "To" date when the raw event that you want to retrieve from Fortinet FortiEDR, was seen for the last time. Use this parameter together with the "Last Seen From" parameter to specify a date range. |
| Strict Mode |
True/False parameter indicating whether or not to perform strict matching on the search parameters while retrieving events from Fortinet FortiEDR. By default, this is set as false. |
| Full Data Requested |
True/False parameter indicating whether to include the event internal information for the raw events that you want to retrieve from Fortinet FortiEDR. |
| Page Number |
(Optional) Page number from which you want to retrieve records. |
| Items Per Page |
(Optional) Maximum number of events that this operation should return for the current page. Values supported are: Default "100" and Maximum "2000". |
| Sorting |
(Optional) Name of the fields by which you want to sort the results retrieved by this operation. You can enter the fields in the following format: {"column1":true, "column2":false}. True indicates sorting in descending order. Results are sorted by the first field, then by the second field, and so on. |
Output
The output contains the following populated JSON schema:
{
"count": "",
"eventId": "",
"lastSeen": "",
"loggedUsers": [],
"rawEventId": "",
"destination": "",
"firstSeen": "",
"device": "",
"deviceIp": ""
}
operation: Get Event Count
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Event IDs |
List of comma-separated event IDs based on which you want to retrieve event counts from Fortinet FortiEDR. |
| Device Name |
(Optional) Name of the device on which the event whose counts you want to retrieve from Fortinet FortiEDR occurred. |
| Collector Groups |
(Optional) List of collector groups whose collector had reported the events whose counts you want to retrieve from Fortinet FortiEDR. |
| Operating System |
(Optional) Name of the operating system of the devices on which the events whose counts you want to retrieve from Fortinet FortiEDR occurred. |
| Device IPs |
(Optional) List of IP addresses of the devices on which the events whose counts you want to retrieve from Fortinet FortiEDR occurred. |
| MAC Addresses |
(Optional) MAC addresses where the events whose counts you want to retrieve from Fortinet FortiEDR occurred. |
| Filehash |
(Optional) Hash signature of the main process of the events whose counts you want to retrieve from Fortinet FortiEDR. |
| Process |
(Optional) Name of the main process of the events whose counts you want to retrieve from Fortinet FortiEDR. |
| Process Path |
(Optional) Path of the processes related to the events whose counts you want to retrieve from Fortinet FortiEDR. |
| First Seen From |
(Optional) "From" date when the events whose counts you want to retrieve from Fortinet FortiEDR, were seen for the first time. Use this parameter together with the "First Seen To" parameter to specify a date range. |
| First Seen To |
(Optional) "To" date when the events whose counts you want to retrieve from Fortinet FortiEDR, were seen for the first time. Use this parameter together with the "First Seen From" parameter to specify a date range. |
| Last Seen From |
(Optional) "From" date when the events whose counts you want to retrieve from Fortinet FortiEDR, were seen for the last time. Use this parameter together with the "Last Seen To" parameter to specify a date range. |
| Last Seen To |
(Optional) "To" date when the events whose counts you want to retrieve from Fortinet FortiEDR, were seen for the last time. Use this parameter together with the "Last Seen From" parameter to specify a date range. |
| Classification |
Classification of the events whose counts you want to retrieve from Fortinet FortiEDR. Classification is a list of strings that contain one or more of the following values: Malicious, Suspicious, Inconclusive, Likely Safe, PUP, or Safe. |
| Actions |
Actions that were enforced on the events whose counts you want to retrieve from Fortinet FortiEDR. You can choose from the following options: Block, Simulation Block, or Log. |
| Destinations |
Connection destination(s) of the events whose counts you want to retrieve from Fortinet FortiEDR. |
| Rule |
Short rule name of the rule that triggered the events whose counts you want to retrieve from Fortinet FortiEDR. |
| Seen |
True/False parameter indicating whether events whose counts you want to retrieve from Fortinet FortiEDR were read/unread by the user operating the API. |
| Handled |
True/False parameter indicating whether events whose counts you want to retrieve from Fortinet FortiEDR were handled/unhandled. |
| Signed |
True/False parameter indicating whether the events whose counts you want to retrieve from Fortinet FortiEDR are signed/unsigned. |
| Muted |
True/False parameter indicating whether the events whose counts you want to retrieve from Fortinet FortiEDR are muted/unmuted. |
| Logged in User |
Logged-in user associated with the events whose counts you want to retrieve from Fortinet FortiEDR. |
| Organization |
Name of the organization whose associated event counts you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated event counts you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then this operation will retrieve data that is shared by all organizations. |
| Archived |
True/False parameter indicating whether to include only archived events while retrieving event counts from Fortinet FortiEDR. By default, this is set as false. |
| Strict Mode |
True/False parameter indicating whether or not to perform strict matching on the search parameters while retrieving event counts from Fortinet FortiEDR. By default, this is set as false. |
| Page Number |
(Optional) Page number from which you want to retrieve records. |
| Items Per Page |
(Optional) Maximum number of events that this operation should return for the current page. Values supported are: Default "100" and Maximum "2000". |
| Sorting |
Name of the fields by which you want to sort the results retrieved by this operation. You can enter the fields in the following format: {"column1":true, "column2":false}. True indicates sorting in descending order. Results are sorted by the first field, then by the second field, and so on. |
Output
The output contains the following populated JSON schema:
{
"event_cout": ""
}
operation: Get Event List Extended
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Event IDs |
List of comma-separated event IDs based on which you want to retrieve archived/unarchived events from Fortinet FortiEDR. |
| Device Name |
Name of the device on which the events that you want to retrieve from Fortinet FortiEDR occurred. |
| Collector Groups |
List of collector groups whose collector had reported the events that you want to retrieve from Fortinet FortiEDR. |
| Operating System |
Name of the operating system of the devices on which the events that you want to retrieve from Fortinet FortiEDR occurred. |
| Device IPs |
List of IP addresses of the devices on which the events that you want to retrieve from Fortinet FortiEDR occurred. |
| MAC Addresses |
MAC addresses where the events that you want to retrieve from Fortinet FortiEDR occurred. |
| Filehash |
Hash signature of the main process of the events that you want to retrieve from Fortinet FortiEDR. |
| Process |
Name of the main process of the events that you want to retrieve from Fortinet FortiEDR. |
| Process Path |
Path of the processes related to the events that you want to retrieve from Fortinet FortiEDR. |
| First Seen From |
"From" date when the events that you want to retrieve from Fortinet FortiEDR, were seen for the first time. Use this parameter together with the "First Seen To" parameter to specify a date range. |
| First Seen To |
"To" date when the events that you want to retrieve from Fortinet FortiEDR, were seen for the first time. Use this parameter together with the "First Seen From" parameter to specify a date range. |
| Last Seen From |
"From" date when the events that you want to retrieve from Fortinet FortiEDR, were seen for the last time. Use this parameter together with the "Last Seen To" parameter to specify a date range. |
| Last Seen To |
"To" date when the events that you want to retrieve from Fortinet FortiEDR, were seen for the last time. Use this parameter together with the "Last Seen From" parameter to specify a date range. |
| Classification |
Classification of the events that you want to retrieve from Fortinet FortiEDR. Classification is a list of strings that contain one or more of the following values: Malicious, Suspicious, Inconclusive, Likely Safe, PUP, or Safe. |
| Actions |
Actions that were enforced on the events that you want to retrieve from Fortinet FortiEDR. You can choose from the following options: Block, Simulation Block, or Log. |
| Destinations |
Connection destination(s) of the events that you want to retrieve from Fortinet FortiEDR. |
| Rule |
Short rule name of the rule that triggered the events that you want to retrieve from Fortinet FortiEDR. |
| Logged in User |
Logged-in user associated with the events that you want to retrieve from Fortinet FortiEDR. |
| Seen |
True/False parameter indicating whether events that you want to retrieve from Fortinet FortiEDR were read/unread by the user operating the API. |
| Handled |
True/False parameter indicating whether events that you want to retrieve from Fortinet FortiEDR were handled/unhandled. |
| Signed |
True/False parameter indicating whether the event that you want to retrieve from Fortinet FortiEDR is signed/unsigned. |
| Muted |
True/False parameter indicating whether the event that you want to retrieve from Fortinet FortiEDR is muted/unmuted. |
| Organization |
Name of the organization whose associated event you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated event you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then this operation will retrieve data that is shared by all organizations. |
| Strict Mode |
True/False parameter indicating whether or not to perform strict matching on the search parameters while retrieving events from Fortinet FortiEDR. By default, this is set as false. |
| Page Number |
Page number from which you want to retrieve records. |
| Items Per Page |
Maximum number of events that this operation should return for the current page. Values supported are: Default "100" and Maximum "2000". |
| Sorting |
Name of the fields by which you want to sort the results retrieved by this operation. You can enter the fields in the following format: {"column1":true, "column2":false}. True indicates sorting in descending order. Results are sorted by the first field, then by the second field, and so on. |
Output
The output contains the following populated JSON schema:
{
"eventId": "",
"process": "",
"processPath": "",
"processType": "",
"firstSeen": "",
"lastSeen": "",
"seen": "",
"handled": "",
"comment": "",
"certified": "",
"archived": "",
"severity": "",
"classification": "",
"destinations": [],
"rules": [],
"loggedUsers": [],
"organization": "",
"muted": "",
"muteEndTime": "",
"collectors": [
{
"lastSeen": "",
"ip": "",
"collectorGroup": "",
"macAddresses": [],
"id": "",
"device": "",
"operatingSystem": ""
}
],
"action": ""
}
operation: Search Filehash
Input parameters
| Parameter |
Description |
| Filehash |
One or more comma-separated file hashes that you want to search for in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"threatsHunting": [
{
"fileName": "",
"deviceName": "",
"path": ""
}
],
"applications": [],
"filehash": "",
"eventIds": []
}
operation: Get File
Input parameters
| Parameter |
Description |
| Type |
Type of the device input parameter from which you want to get the file from Fortinet FortiEDR. You can choose between ID or NAME.
If you choose 'ID', then you must specify the following parameter:
- Device ID: ID of the device from which you want to retrieve the file.
If you choose 'NAME', then you must specify the following parameter:
- Device Name: Name of the device from which you want to retrieve the file.
|
| File Paths |
List of file paths from which you want to retrieve the file. For example, c:\temp\example.exe |
| Organization |
(Optional) Name of a specific organization whose associated files you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"@type": "",
"file": {
"@type": "",
"file": {
"@type": ""
},
"mimeType": "",
"@context": "",
"size": "",
"metadata": "",
"filename": "",
"owners": "",
"uploadDate": "",
"@id": ""
},
"createDate": "",
"description": "",
"modifyUser": {
"@type": "",
"modifyDate": "",
"createDate": "",
"@settings": "",
"modifyUser": "",
"id": "",
"userType": "",
"name": "",
"@id": "",
"userId": "",
"avatar": "",
"createUser": ""
},
"@id": "",
"name": "",
"modifyDate": "",
"@context": "",
"id": "",
"type": "",
"createUser": {
"@type": "",
"modifyDate": "",
"createDate": "",
"@settings": "",
"modifyUser": "",
"id": "",
"userType": "",
"name": "",
"@id": "",
"userId": "",
"avatar": "",
"createUser": ""
}
}
operation: Retrieve File or Memory
Input parameters
| Parameter |
Description |
| Raw Event ID |
ID of the raw event on which you want to perform the memory retrieval from Fortinet FortiEDR. |
| Retrieve From |
Method to be used to perform the memory retrieval from Fortinet FortiEDR. You can choose between Memory or Disk.
If you choose Memory, then you must specify the following parameters:
- Process ID: ID of the process from which you want to take a memory image.
- Memory Region Start Address: Memory start range, in Hexadecimal format from which you want to take a memory image.
- Memory Region End Address: Memory end range, in Hexadecimal format from which you want to take a memory image.
- Organization: (Optional) Name of a specific organization on which you want to perform the memory retrieval in Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose Disk, then you must specify the following parameters:
- File Paths: List of file paths from which you want to perform the memory retrieval in Fortinet FortiEDR.
- Organization: (Optional) Name of a specific organization on which you want to perform the memory retrieval in Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
|
| Process ID |
(Optional) ID of the process from which you want to take a memory image. |
| Memory Region Start Address |
(Optional) Start address of the memory region, in the Hexadecimal format, from which you want to take a memory image. |
| Memory Region End Address |
(Optional) Memory end range, in Hexadecimal format from which you want to take a memory image. |
| File Paths |
(Optional) List of file paths from which you want to perform the memory retrieval in Fortinet FortiEDR. |
| Retrieve From |
(Optional) Choose whether to retrieve the memory from Memory and/or Disk. |
| Organization |
(Optional) Name of a specific organization on which you want to perform the memory retrieval in Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"@type": "",
"file": {
"@type": "",
"file": {
"@type": ""
},
"mimeType": "",
"@context": "",
"size": "",
"metadata": "",
"filename": "",
"owners": "",
"uploadDate": "",
"@id": ""
},
"createDate": "",
"description": "",
"modifyUser": {
"@type": "",
"modifyDate": "",
"createDate": "",
"@settings": "",
"modifyUser": "",
"id": "",
"userType": "",
"name": "",
"@id": "",
"userId": "",
"avatar": "",
"createUser": ""
},
"@id": "",
"name": "",
"modifyDate": "",
"@context": "",
"id": "",
"type": "",
"createUser": {
"@type": "",
"modifyDate": "",
"createDate": "",
"@settings": "",
"modifyUser": "",
"id": "",
"userType": "",
"name": "",
"@id": "",
"userId": "",
"avatar": "",
"createUser": ""
}
}
operation: Remediate Device
Input parameters
| Parameter |
Description |
| Type |
Type of the device input parameter on which you want to perform the remediation action in Fortinet FortiEDR. You can choose between ID or NAME.
If you choose 'ID', then you must specify the following parameter:
- Device ID: ID of the device on which you want to take the remediation action.
If you choose 'NAME', then you must specify the following parameter:
- Device Name: Name of the device on which you want to take the remediation action.
|
| Organization |
(Optional) Name of a specific organization that contains the device on which you want to perform the remediation action.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
| Remediation Action |
Action that you want to perform on the specified device. You can choose from the following options: Kill Process, Delete File, Handle Persistent Data, or Remediate Thread.
If you choose 'Kill Process', then you must specify the following parameters:
- Process ID: ID of the process you want to terminate on the specified device.
- Process Name: (Optional) Name of the process you want to terminate on the specified device.
If you choose 'Delete File', then you must specify the following parameter:
- Delete File at Path: List containing the full path of executable files (*.exe) that you want to delete from the specified device.
If you choose 'Handle Persistent Data', then you must specify the following parameter:
- Persistence Data (Registry) Action: Action that should be taken for persistent data on the specified device. You can choose from the following options: Delete Key, Delete Value, or Update.
- If you choose 'Delete Key', then you must specify the following parameters:
- Persistence Data (Registry) Path: Path of the persistent data whose key you want to delete on the specified device.
- Persistence Data (Registry) Value Name: Name of the key value of the persistent data you want to delete on the specified device.
- If you choose 'Delete Value', then you must specify the following parameters:
- Persistence Data (Registry) Path: Path of the persistent data whose value you want to delete on the specified device.
- Persistence Data (Registry) Value Name: Name of the value of the persistent data that you want to delete on the specified device.
- If you choose 'Update', then you must specify the following parameters:
- Persistence Data (Registry) Path: Path of the persistent data that you want to update on the specified device.
- Persistence Data (Registry) Value Name: Name of the value of the persistent data you want to update on the specified device.
- Persistence Data (Registry) Value New Type: New data value type that should be applied to the persistent data on the specified device. You can choose from the following options: REG_SZ, REG_EXPAND_SZ, REG_BINARY, REG_DWORD, REG_DWORD_BIG_ENDIAN, REG_LINK, REG_MULTI_SZ, REG_RESOURCE_LIST, REG_FULL_RESOURCE_DESCRIPTOR, REG_RESOURCE_REQUIREMENTS_LIST, or REG_QWORD.threadId: (This specifies the thread ID)
- Persistence Data (Registry) New Content: New data content that should be applied to the persistent data on the specified device. The content format provided depends on the type used in persistenceDataValueNewType. The format should be provided as follows:
- String value for the following types: REG_SZ(1), REG_EXPAND_SZ(2), REG_DWORD(4), and REG_QWORD(11).
- Base64 for the following types: REG_BINARY(3), REG_DWORD_BIG_ENDIAN(5), REG_LINK(6), REG_MULTI_SZ(7), REG_RESOURCE_LIST(8), REG_FULL_RESOURCE_DESCRIPTOR(9), and REG_RESOURCE_REQUIREMENTS_LIST(10)
If you choose 'Remediate Thread', then you must specify the following parameter:
- Thread ID: ID of the thread on which you want to take the remediation action.
|
Output
The output contains the following populated JSON schema:
{
"result": ""
}
operation: Get Collector List
Input parameters
| Parameter |
Description |
| Type |
Type of the device whose associate collector list you want to retrieve from Fortinet FortiEDR. You can choose between ID or NAME.
If you choose 'ID', then you must specify the following parameter:
- Device IDs: List of device IDs whose associate collector list you want to retrieve from Fortinet FortiEDR.
If you choose 'NAME', then you must specify the following parameter:
- Device Name: List of device names whose associate collector list you want to retrieve from Fortinet FortiEDR.
|
| Collector Groups |
(Optional) List of collector group names whose associated collectors you want to retrieve from Fortinet FortiEDR. |
| IPs |
(Optional) List of IP addresses whose associated collectors you want to retrieve from Fortinet FortiEDR. |
| Operating Systems |
(Optional) List of operating systems whose associated collectors you want to retrieve from Fortinet FortiEDR. For example, Windows 7 Pro. |
| OS Families |
(Optional) List of OS Families whose associated collectors you want to retrieve from Fortinet FortiEDR. e.g Windows, Windows Server, OS X. |
| States |
(Optional) List of collector states based on which you want to retrieve from Fortinet FortiEDR. You can choose one or more of the following options: Running, Disconnected, Disabled, Degraded, Pending Reboot, Isolated, or Expired. |
| Last Seen Start |
(Optional) Retrieves collectors from Fortinet FortiEDR that was last seen after the value assigned to this date. |
| Last Seen End |
(Optional) Retrieve collectors from Fortinet FortiEDR that were last seen before the value assigned to this date. |
| Versions |
(Optional) List of collector versions that you want to retrieve from Fortinet FortiEDR. |
| Strict Mode |
(Optional) True/False parameter indicating whether or not to perform strict matching on the search parameters while retrieving event counts from Fortinet FortiEDR. By default, this is set as false. |
| Show Expired |
True/False parameter indicating whether to show an expired collector in the results retrieved from Fortinet FortiEDR. |
| Logged in User |
(Optional) Logged-in user associated with the collectors you want to retrieve from Fortinet FortiEDR. |
| Organization |
(Optional) Name of the organization whose associated collectors you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated collectors you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then this operation will retrieve data that is shared by all organizations.
|
| Page Number |
(Optional) Page number from which you want to retrieve records. |
| Items Per Page |
(Optional) Maximum number of events that this operation should return for the current page. Values supported are: Default "100" and Maximum "2000". |
| Sorting |
Name of the fields by which you want to sort the results retrieved by this operation. You can enter the fields in the following format: {"column1":true, "column2":false}. True indicates sorting in descending order. Results are sorted by the first field, then by the second field, and so on. |
Output
The output contains the following populated JSON schema:
{
"operatingSystem": "",
"accountName": "",
"version": "",
"osFamily": "",
"ipAddress": "",
"stateAdditionalInfo": "",
"state": "",
"id": "",
"collectorGroupName": "",
"name": "",
"loggedUsers": [],
"organization": "",
"lastSeenTime": "",
"macAddresses": []
}
operation: Isolate Collector
Input parameters
| Parameter |
Description |
| Type |
Type of the device whose associate collectors you want to isolate from the Fortinet FortiEDR network. You can choose between ID or Name.
If you choose 'ID', then you must specify the following parameter:
- Device IDs: List of device IDs whose associate collectors you want to isolate from the Fortinet FortiEDR network.
If you choose 'Name', then you must specify the following parameter:
- Device Names: List of device names whose associate collectors you want to isolate from the Fortinet FortiEDR network.
|
| Organization |
(Optional) Name of a specific organization whose associated collector you want to isolate from the Fortinet FortiEDR network.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"result": ""
}
operation: Unisolate Collector
Input parameters
| Parameter |
Description |
| Type |
Type of the device whose associate collectors you want to unisolate from the Fortinet FortiEDR network. You can choose between ID or Name.
If you choose 'ID', then you must specify the following parameter:
- Device IDs: List of device IDs whose associate collectors you want to unisolate from the Fortinet FortiEDR network.
If you choose 'Name', then you must specify the following parameter:
- Device Names: List of device names whose associate collectors you want to unisolate from the Fortinet FortiEDR network.
|
| Organization |
(Optional) Name of a specific organization whose associated collector you want to unisolate from the Fortinet FortiEDR network.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"result": ""
}
operation: Create Exception
Input parameters
| Parameter |
Description |
| Event ID |
ID of the event that needs to be added as an exception in Fortinet FortiEDR. |
| Collector Groups |
Specify the list of all the collector groups to which the exception should be applied. If you do not specify any collector groups, then, all collector groups are selected. |
| All Collector Groups |
Select True for this parameter to apply the exception to all collector groups. When this parameter is not used, then all collector groups are selected. |
| Organization |
Name of a specific organization to which the exception should be applied.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
| All Organizations |
Select True for this parameter to apply the exception to all organizations. When this parameter is not used, then all organizations are selected. |
| Destinations |
List of IP addresses to which the exception applies and/or the value of the internal destinations. |
| All Destinations |
Select True for this parameter to apply the exception to all destinations. When this parameter is not used, then all destinations are selected. |
| Comment |
User-defined string that you want to attach to the exception in Fortinet FortiEDR. |
| Force Create |
Select True for this parameter to apply to create the exception, even if there are already exceptions that cover the specified event. |
| Exception JSON Values |
In order to set the advanced settings of an exception, the user must know which processes exist in the event and which rules were triggered. Use the following JSON format to insert the correct details:
{
"useInException": {
"process_name_1": {
"rule_name1": true,
"rule_name2": true
},
"process_name_2": {
"rule_name_1": false
}
},
"useAnyPath": {
"process_name_1": {
"rule_name": true
},
"process_name_2": {
"rule_name": true
}
}
}
For example:
{
"useInException": {
" dynamicCode.exe ": {
"Unmapped Executable": true,
"Executable Format": true,
"Dynamic Code": false,
"Writeable Code": false
},
" dynamic.dll": {}
},
"Unmapped Executable": false,
"useAnyPath": {
" dynamicCode.exe ": {
"Dynamic Code": true,
"Executable Format": false,
"Unmapped Executable": true,
"Writeable Code": true
},
" dynamic.dll": {
"Unmapped Executable": true
}
}
}
|
Output
The output contains the following populated JSON schema:
{
"result": ""
}
operation: Get Exception List
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list is returned.
| Parameter |
Description |
| Created Before |
DateTime before which the exceptions that you want to retrieve from Fortinet FortiEDR were created. |
| Created After |
DateTime after which the exceptions that you want to retrieve from Fortinet FortiEDR were created. |
| Updated Before |
DateTime before which the exceptions that you want to retrieve from Fortinet FortiEDR were updated. |
| Updated After |
DateTime after which the exceptions that you want to retrieve from Fortinet FortiEDR were updated. |
| Organization |
Name of the organization whose associated event exceptions you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated event exceptions you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then this operation will retrieve data that is shared by all organizations.
|
Output
The output contains the following populated JSON schema:
{
"exceptionId": "",
"originEventId": "",
"userName": "",
"updatedAt": "",
"createdAt": "",
"comment": "",
"organization": "",
"selectedDestinations": [],
"optionalDestinations": [],
"selectedCollectorGroups": [],
"optionalCollectorGroups": [],
"alerts": [
{
"ruleName": "",
"process": {
"name": "",
"path": "",
"usedInException": "",
"useAnyPath": "",
"signed": ""
}
}
]
}
operation: Update Exception
Input parameters
| Parameter |
Description |
| Event ID |
ID of the event whose associated exception you want to update in Fortinet FortiEDR. |
| Exception ID |
ID of the exception that you want to update in the Fortinet FortiEDR. |
| Organization |
Name of a specific organization that you want to update in the specific exception Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
| Add Destinations |
(Optional) Type of destination that you want to update in the specific exception Fortinet FortiEDR. You can choose between Exact Destination or All Destinations.
- If you choose 'Exact Destination', then in the Exact Destinations (IP Set Names) field, specify the destination names, in the CSV format that you want to add to the specified exception.
- If you choose 'All Destinations', then the Destination parameter will be set automatically to 'All Destinations'.
|
| Collector Group |
(Optional) Type of collector group that you want to update in the specific exception Fortinet FortiEDR. You can choose between Exact Collector Group or All Groups. or All Organizations.
- If you choose 'Exact Collector Group', then in the Exact Collector Group field, specify the collector groups, in the CSV format that you want to add to the specified exception.
- If you choose 'All Groups' or 'All Organizations', then the Collector Group parameter will be set automatically to 'All Groups' or 'All Organizations' respectively.
|
| Add Comment |
(Optional) Free text that you want to add as a comment to the exception that you want to update in Fortinet FortiEDR. |
Output
The output contains a non-dictionary value.
operation: Get Event Exceptions
Input parameters
| Parameter |
Description |
| Event ID |
ID of the event whose associated exceptions you want to retrieve from Fortinet FortiEDR. |
| Organization |
(Optional) Name of a specific organization whose associated event exceptions you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"exceptionId": "",
"originEventId": "",
"userName": "",
"updatedAt": "",
"createdAt": "",
"comment": "",
"organization": "",
"selectedDestinations": [],
"optionalDestinations": [],
"selectedCollectorGroups": [],
"optionalCollectorGroups": [],
"alerts": [
{
"ruleName": "",
"process": {
"name": "",
"path": "",
"usedInException": "",
"useAnyPath": "",
"signed": ""
}
}
]
}
operation: Get Raw JSON Event Data
Input parameters
| Parameter |
Description |
| Event ID |
ID of the event that holds the raw JSON data that you want to retrieve from Fortinet FortiEDR. |
| Organization |
(Optional) Name of a specific organization whose associated events hold the raw JSON data that you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"updateTime": "",
"sendToSupportOnly": "",
"LoggedUsers": [],
"EventType": "",
"Alerts": [
{
"updateTime": "",
"Rule": "",
"RuleContentId": "",
"Process": "",
"ProcessScriptModule": "",
"ProcessMountPoint": "",
"StackType": "",
"Severity": "",
"Action": "",
"KeyCrc": "",
"ProcessCrc": "",
"KeyPathCrc": "",
"ProcessPathCrc": "",
"KeyScriptCrc": "",
"ProcessScriptCrc": "",
"KeyShaCrc": "",
"ProcessShaCrc": "",
"IsKeyBinary": "",
"Key": "",
"KeyScriptModule": "",
"MountPoint": "",
"UseBoth": "",
"KeyVendor": "",
"ProcessVendor": "",
"OS": "",
"KeySha": "",
"ProcessSha": "",
"KeyAnalysisFlags": "",
"ProcessAnalysisFlags": "",
"Is64bit": "",
"Policy": "",
"Stacks": [
{
"StackNum": ""
}
],
"WhitelistingReputation": "",
"WhitelistingExpirationTime": "",
"Index": "",
"MainApp": {
"Executable": "",
"ScriptModule": "",
"Sha1Hash": "",
"Vendor": "",
"Flags": "",
"MalwareLikelihoodPercent": "",
"Src": "",
"ExtWhiteListing": {
"Hash": {
"Hash": "",
"HashType": ""
},
"ExtWhiteListing": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"CombinedReputation": "",
"RLDetails": {
"RLReputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": ""
}
}
},
"ClassificationRules": [
{
"ClassificationRuleId": "",
"Description": ""
}
],
"MatchedClassificationRules": [
{
"ClassificationRuleId": "",
"Description": ""
}
],
"Classification": "",
"ExtWhiteListing": {
"Hash": {
"Hash": "",
"HashType": ""
},
"ExtWhiteListing": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"CombinedReputation": "",
"RLDetails": {
"RLReputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": ""
}
},
"IsSuppressed": "",
"OriginalClassification": "",
"IsOriginallySuppressed": "",
"ClassifyCount": "",
"ClassificationChanges": [
{
"ClassificationChangedTo": ""
}
],
"ClassificationRulesMapSecurityLevel": "",
"ReputationSource": "",
"ShouldHaveBeenSuppressed": "",
"ReputationSourceExt": {
"ReputationSource": ""
},
"PolicyModeWhenAlertWasIssued": "",
"IsKeySigned": "",
"IsProcessSigned": ""
}
],
"EventId": "",
"Version": "",
"FirstSeen": "",
"LastSeen": "",
"HostName": "",
"Count": "",
"MainProcessId": "",
"OperatingSystem": "",
"OS": "",
"GlobalAggregationCrc": "",
"GlobalShaAggregationCrc": "",
"Application": "",
"MountPoint": "",
"AppScriptModule": "",
"Is64bit": "",
"IsSigned": "",
"AppSha": "",
"AppVendor": "",
"EventSource": "",
"EventCoreVersion": "",
"AggregationEventId": "",
"AgentVersion": "",
"ManagementServerVersion": "",
"WhitelistingExpired": "",
"MoreAddresses": "",
"EventClassification": "",
"EventClassificationSourceAlert": "",
"AppDetails": {
"Executable": "",
"ScriptModule": "",
"Sha1Hash": "",
"Vendor": "",
"Flags": "",
"MalwareLikelihoodPercent": "",
"Src": "",
"ExtWhiteListing": {
"Hash": {
"Hash": "",
"HashType": ""
},
"ExtWhiteListing": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"CombinedReputation": "",
"RLDetails": {
"RLReputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": ""
}
}
},
"AppSourceAlert": "",
"ClassifierModelVersion": "",
"SuppressedAlertCount": "",
"ContentVersion": "",
"EventRLStatuses": [
{
"Hash": "",
"RLResult": "",
"IsAlertGenerated": ""
}
],
"SecurityLevelWhenIssued": "",
"EventClassificationStage": "",
"EventRlMissing": [],
"RepPreResolveTimerCount": "",
"RepPreResWastedTimeMs": "",
"EventWorkerTimeMs": "",
"WasDeffered": "",
"LastSentToECS": "",
"WasChangedOnDeferrer": "",
"CoreHostName": "",
"DeferrerChanges": "",
"ConfigurationVersion": "",
"FlowInfoFlags": "",
"CustomerName": "",
"Exceptions": [
{
"updateTime": "",
"UpdatedBy": "",
"UpdatedAt": "",
"CreatedBy": "",
"CreatedAt": "",
"Alerts": [
{
"updateTime": "",
"Rule": "",
"RuleContentId": "",
"Process": "",
"ProcessScriptModule": "",
"ProcessMountPoint": "",
"StackType": "",
"Severity": "",
"Action": "",
"KeyCrc": "",
"ProcessCrc": "",
"KeyPathCrc": "",
"ProcessPathCrc": "",
"KeyScriptCrc": "",
"ProcessScriptCrc": "",
"KeyShaCrc": "",
"ProcessShaCrc": "",
"IsKeyBinary": "",
"Key": "",
"KeyScriptModule": "",
"MountPoint": "",
"UseBoth": "",
"UseProcess": "",
"UseAnyKeyPath": "",
"UseAnyProcessPath": "",
"UseProcessScript": "",
"UseKeyScript": "",
"KeyVendor": "",
"ProcessVendor": "",
"OS": "",
"KeySha": "",
"ProcessSha": "",
"KeyAnalysisFlags": "",
"ProcessAnalysisFlags": "",
"Is64bit": "",
"Policy": "",
"WcProcess": "",
"WcProcessScriptModule": "",
"WcKeyScriptModule": "",
"WcKey": "",
"WcMask": "",
"IsKeySigned": "",
"IsProcessSigned": ""
}
],
"EventId": "",
"OriginalEventJson": {
"updateTime": "",
"sendToSupportOnly": "",
"LoggedUsers": [],
"EventType": "",
"Alerts": [
{
"updateTime": "",
"Rule": "",
"RuleContentId": "",
"Process": "",
"ProcessScriptModule": "",
"ProcessMountPoint": "",
"StackType": "",
"Severity": "",
"Action": "",
"KeyCrc": "",
"ProcessCrc": "",
"KeyPathCrc": "",
"ProcessPathCrc": "",
"KeyScriptCrc": "",
"ProcessScriptCrc": "",
"KeyShaCrc": "",
"ProcessShaCrc": "",
"IsKeyBinary": "",
"Key": "",
"KeyScriptModule": "",
"MountPoint": "",
"UseBoth": "",
"UseProcess": "",
"UseAnyKeyPath": "",
"UseAnyProcessPath": "",
"UseProcessScript": "",
"UseKeyScript": "",
"KeyVendor": "",
"ProcessVendor": "",
"OS": "",
"KeySha": "",
"ProcessSha": "",
"KeyAnalysisFlags": "",
"ProcessAnalysisFlags": "",
"Is64bit": "",
"Policy": "",
"MitreTags": "",
"Stacks": [
{
"StackNum": ""
}
],
"WhitelistingReputation": "",
"WhitelistingExpirationTime": "",
"Index": "",
"MainApp": {
"Executable": "",
"ScriptModule": "",
"Sha1Hash": "",
"Vendor": "",
"Flags": "",
"MalwareLikelihoodPercent": "",
"Src": "",
"ExtWhiteListing": {
"Hash": {
"Hash": "",
"HashType": ""
},
"ExtWhiteListing": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"CombinedReputation": "",
"RLDetails": {
"RLReputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": ""
}
}
},
"ClassificationRules": [
{
"ClassificationRuleId": "",
"Description": ""
}
],
"MatchedClassificationRules": [
{
"ClassificationRuleId": "",
"Description": ""
}
],
"Classification": "",
"ExtWhiteListing": {
"Hash": {
"Hash": "",
"HashType": ""
},
"ExtWhiteListing": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"CombinedReputation": "",
"RLDetails": {
"RLReputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": ""
}
},
"IsSuppressed": "",
"OriginalClassification": "",
"IsOriginallySuppressed": "",
"ClassifyCount": "",
"ForcedClassification": "",
"ClassificationOriginStackData": "",
"OriginalClassificationOriginStackData": "",
"ClassificationChanges": [
{
"ClassificationChangedTo": ""
}
],
"ClassificationRulesMapSecurityLevel": "",
"ReputationSource": "",
"ShouldHaveBeenSuppressed": "",
"ReputationSourceExt": {
"ReputationSource": ""
},
"OriginalReputationSource": "",
"PolicyModeWhenAlertWasIssued": "",
"IsKeySigned": "",
"IsProcessSigned": ""
}
],
"EventId": "",
"Version": "",
"ApplicationOwner": "",
"FirstSeen": "",
"LastSeen": "",
"Protocol": "",
"LocalIp": "",
"HostName": "",
"LocalPort": "",
"RemoteIp": "",
"Country": "",
"Asn": "",
"RemotePort": "",
"Count": "",
"MainProcessId": "",
"OperatingSystem": "",
"OS": "",
"OsVersion": "",
"GlobalAggregationCrc": "",
"GlobalShaAggregationCrc": "",
"Application": "",
"MountPoint": "",
"AppScriptModule": "",
"Is64bit": "",
"IsSigned": "",
"AppSha": "",
"AppVendor": "",
"EventSource": "",
"EventCoreVersion": "",
"AggregationEventId": "",
"AgentVersion": "",
"ManagementServerVersion": "",
"WhitelistingExpired": "",
"MoreAddresses": "",
"EventClassification": "",
"EventClassificationSourceAlert": "",
"AppDetails": {
"Executable": "",
"ScriptModule": "",
"Sha1Hash": "",
"Vendor": "",
"Flags": "",
"MalwareLikelihoodPercent": "",
"Src": "",
"ExtWhiteListing": {
"Hash": {
"Hash": "",
"HashType": ""
},
"ExtWhiteListing": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"CombinedReputation": "",
"RLDetails": {
"RLReputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": ""
}
}
},
"AppSourceAlert": "",
"ClassifierModelVersion": "",
"SuppressedAlertCount": "",
"ContentVersion": "",
"EventClassificationOriginStackData": "",
"EventRLStatuses": [
{
"Hash": "",
"RLResult": "",
"IsAlertGenerated": ""
}
],
"SecurityLevelWhenIssued": "",
"EventClassificationStage": "",
"ReputationSource": "",
"ShouldHaveBeenSuppressed": "",
"EventRlMissing": [],
"RepPreResolveTimerCount": "",
"RepPreResWastedTimeMs": "",
"RepPreResAllowedDelayMs": "",
"EventWorkerTimeMs": "",
"WasDeffered": "",
"LastSentToECS": "",
"WasChangedOnDeferrer": "",
"EventDigest": "",
"CoreHostName": "",
"DeferrerChanges": "",
"ConfigurationVersion": "",
"FlowInfoFlags": "",
"CustomerName": "",
"Exceptions": "",
"MacAddresses": "",
"CollectorGroup": "",
"EventAggId": "",
"ForensicsChart": "",
"EventUniqueId": "",
"IsSuppressedEvent": "",
"IsEventReportedByDeviceNotSupportingWildcardsOrIpSets": "",
"Muted": "",
"MuteEndTime": "",
"DeviceMetadata": "",
"Action": "Block",
"ProcessAggregationCrc": "",
"DeviceAggregationCrc": "",
"ProcessShaAggregationCrc": "",
"DeviceShaAggregationCrc": "",
"IsRepPreResEnabled": "",
"IsRepPreResolveTimedOut": "",
"Organization": "",
"OrganizationId": "",
"AgentId": "",
"StackInfos": "",
"AggregationClassification": "",
"AggregationClassificationSource": "",
"ManagementDbId": ""
},
"OS": "",
"Destinations": [],
"IpGroups": [],
"AgentGroups": [],
"AllAccountsAgentGroups": "",
"AllAgentGroups": "",
"AllDestinations": "",
"Origin": "",
"ExceptionId": ""
}
],
"MacAddresses": [],
"CollectorGroup": "",
"EventAggId": "",
"EventUniqueId": "",
"IsSuppressedEvent": "",
"Muted": "",
"Action": "",
"StackInfos": [
{
"StackType": "",
"Timestamp": "",
"StackInfoFlags": "",
"ThreadId": "",
"ProcessId": "",
"Is64bit": "",
"ProcessName": "",
"ExecutableHash": "",
"ExecutableHashExtWhiteList": {
"Reputation": "",
"MalwareType": "",
"FamilyName": "",
"ThreatName": "",
"Expiration": ""
},
"ModuleFlags": "",
"PeErrorFlags": "",
"PeVerificationErrorFlags": "",
"ModuleType": "",
"CommonFlags": "",
"MalwareLikelihood": "",
"MalwareLikelihoodNorm": "",
"CommonAdditionalInfo": [
{
"Type": "",
"Privileges": "",
"NumOfPrivilegeChanges": "",
"ProcessOwner": "",
"ProcessEffectiveOwner": "",
"LoggedUsers": []
},
{
"Type": "",
"ObjVersion": "",
"FileOwner": "",
"LastModified": "",
"IsInternetBit": "",
"FileAttributes": ""
},
{
"Type": "",
"RootIssuer": "",
"RootCertThumbprint": "",
"SubjectOfLastCertificate": "",
"LastCertThumbprint": "",
"IsSignatureValid": "",
"IsUnsupportedDigestAlg": "",
"IsCertValid": "",
"IsUnsupportedCertDigestAlg": "",
"IsSelfSigned": "",
"IsCertTrusted": "",
"IsInvalidSigninigTime": "",
"HasExpired": ""
},
{
"Type": "",
"MountPoint": ""
},
{
"Type": "",
"Company": "",
"Description": "",
"Version": "",
"Product": ""
},
{
"Type": "",
"CommandLine": ""
}
],
"AuxPid": "",
"AuxProcessName": "",
"AuxIs64bit": "",
"AuxModuleFlags": "",
"AuxPeErrorFlags": "",
"AuxPeVerificationErrorFlags": "",
"AuxModuleType": "",
"AuxCommonFlags": "",
"AuxCommonAdditionalInfo": [],
"NumStackEntries": "",
"StackEntries": [
{
"StackEntryFlags": "",
"Count": "",
"ESP": "",
"StackValue": "",
"CallTarget": "",
"CommonFlags": "",
"ModuleBase": "",
"ModuleEnd": "",
"TotalRetCount": "",
"TotalNoRetCount": "",
"ModuleFlags": "",
"PeErrorFlags": "",
"PeVerificationErrorFlags": "",
"ModuleType": "",
"MalwareLikelihood": "",
"MalwareLikelihoodNorm": "",
"ModuleName": "",
"ModuleHash": "",
"AdditionalInfo": [],
"CommonAdditionalInfo": [
{
"Type": "",
"Company": ""
},
{
"Type": "",
"ObjVersion": "",
"FileOwner": "",
"LastModified": "",
"IsInternetBit": "",
"FileAttributes": ""
},
{
"Type": "",
"RootIssuer": "",
"RootCertThumbprint": "",
"SubjectOfLastCertificate": "",
"LastCertThumbprint": "",
"IsSignatureValid": "",
"IsUnsupportedDigestAlg": "",
"IsCertValid": "",
"IsUnsupportedCertDigestAlg": "",
"IsSelfSigned": "",
"IsCertTrusted": "",
"IsInvalidSigninigTime": "",
"HasExpired": ""
},
{
"Type": "",
"MountPoint": ""
}
]
}
]
}
],
"Organization": "",
"ProcessAggregationCrc": "",
"DeviceAggregationCrc": "",
"ProcessShaAggregationCrc": "",
"DeviceShaAggregationCrc": "",
"IsRepPreResEnabled": "",
"IsRepPreResolveTimedOut": "",
"AgentId": "",
"OrganizationId": "",
"AggregationClassification": "",
"AggregationClassificationSource": "",
"ManagementDbId": ""
}
operation: Create IPSet
Input parameters
| Parameter |
Description |
| Organization |
Name of the organization in which you want to create the IPSet in Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization in which you want to create the IPSet in Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then the Organization parameter will be set automatically to 'All Organizations'.
If you choose Each, then the value of the Organization parameter is independently applied to each organization by this operation.
For example, let's assume that the same user exists in multiple organizations and 'Each' is specified in the organization parameter, then each organization can update this user separately.
|
| IP Set Name |
Name of the IPSet you want to create in Fortinet FortiEDR. |
| Description |
Description of the IPSet you want to create in Fortinet FortiEDR. |
| IP Address to Include |
List of IP addresses to include in the IPSet you want to create in Fortinet FortiEDR. |
| IP Address to Exclude |
List of IP Addresses to exclude from the IPSet you want to create in Fortinet FortiEDR. |
Output
The output contains the following populated JSON schema:
{
"result": ""
}
operation: Get IPSet List
Input parameters
| Parameter |
Description |
| IP to Search |
IP address using which you want to search for IPSets in Fortinet FortiEDR. |
| Organization |
Name of the organization whose associated IPSets you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated IPSets you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All organizations, then this operation will retrieve data that is shared by all organizations.
|
Output
The output contains the following populated JSON schema:
{
"name": "",
"description": "",
"include": [],
"exclude": [],
"organization": ""
}
operation: Update IPSet
Input parameters
| Parameter |
Description |
| Organization |
Name of the organization in which you want to update the IPSet in Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization in which you want to update the IPSet in Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then the Organization parameter will be set automatically to 'All Organizations'.
If you choose Each, then the value of the Organization parameter is independently applied to each organization by this operation.
For example, let's assume that the same user exists in multiple organizations and 'Each' is specified in the organization parameter, then each organization can update this user separately.
|
| IP Set Name |
Name of the IPSet you want to update in Fortinet FortiEDR. |
| Description |
Description of the IPSet you want to update in Fortinet FortiEDR. |
| Add IP into Sets |
Select this checkbox to add the IP address to the IPSets Include/Exclude sections. Clear this checkbox to remove the IP address from the IPSets Include/Exclude sections |
| IP Address to Include |
List of IP Addresses to include from the IPSet you want to update in Fortinet FortiEDR. |
| IP Address to Exclude |
List of IP Addresses to exclude from the IPSet you want to update in Fortinet FortiEDR. |
Output
The output contains a non-dictionary value.
operation: Delete IPSet
Input parameters
| Parameter |
Description |
| IP Set Names |
List of the IPSet names that you want to delete from Fortinet FortiEDR. |
| Organization |
(Optional) Name of the organization from which you want to delete the IPSet in Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization from which you want to delete the IPSet in Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All Organizations, then the Organization parameter will be set automatically to 'All Organizations'.
|
Output
The output contains a non-dictionary value.
operation: Get Agent Groups
Input parameters
| Parameter |
Description |
| Organization |
Name of the organization whose associated agent groups you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated agent groups you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All organizations, then this operation will retrieve data that is shared by all organizations.
|
Output
The output contains the following populated JSON schema:
{
"id": "",
"name": "",
"organization": "",
"targetVersions": [
{
"osFamily": "",
"version": ""
}
]
}
operation: Get System Summary
Input parameters
| Parameter |
Description |
| Organization |
Name of the organization whose associated environment summary you want to retrieve from Fortinet FortiEDR.
The value that you specify for this parameter indicates how the operation applies to an organization(s). Some parts of the FortiEDR system have separate, non-shared data that is organization-specific. Other parts of the system have data that is shared by all organizations. The value that you specify for the organization parameter, determines the organization(s) to which this operation applies.
If you choose Exact Organization Name, then you must specify the following parameter:
- Organization Name: Name of a specific organization whose associated environment summary you want to retrieve from Fortinet FortiEDR.
Note: The value that you specify in this parameter must match exactly with the organization name specified in Fortinet FortiEDR.
If you choose All organizations, then this operation will retrieve data that is shared by all organizations.
|
| Add License Blob |
Select this option, i.e., set it to 'true' to the license blob to the response retrieved by this operation. By default, addLicenseBlob is set to 'false'. |
Output
The output contains the following populated JSON schema:
{
"workstationCollectorsLicenseCapacity": "",
"serverCollectorsLicenseCapacity": "",
"iotDevicesLicenseCapacity": "",
"registeredCollectors": "",
"workstationsCollectorsInUse": "",
"serverCollectorsInUse": "",
"iotDevicesInUse": "",
"collectorsState": {
"Degraded": "",
"Disabled": "",
"Disconnected": "",
"RebootPending": "",
"Running": "",
"Uninstalling": ""
},
"collectorsDegradedState": {
"ApproveKernelExtensions": "",
"ContentUpdateError": "",
"DriverLoadFailure": "",
"FailedConfigurationUpdate": "",
"GatewayUnreachable": "",
"LostConnection": "",
"MissingMiniFilterSupport": "",
"NoConfiguration": "",
"NoDiskSpace": "",
"OTIFailed": "",
"PAEDisabled": "",
"unsupportedOSVersion": ""
},
"collectorsRunningState": {
"autonomously": "",
"core": ""
},
"collectorsDisconnectedState": {
"disconnected": "",
"expired": "",
"migrated": "",
"pendingMigration": ""
},
"collectorsWithDumps": {
"LinuxKernelPanic": "",
"MacOSKernelPanic": "",
"NsloCollector": "",
"NsloCollectorService": "",
"WindowsKernelFull": "",
"WindowsKernelMini": ""
},
"licenseExpirationDate": "",
"managementVersion": "",
"managementHostname": "",
"managementExternalIP": "",
"managementInternalIP": "",
"collectorVersions": [],
"collectorVersionsV2": [
{
"count": "",
"version": ""
}
],
"cores": [
{
"name": "",
"address": "",
"version": "",
"status": "",
"statusV2": ""
}
],
"aggregators": [
{
"name": "",
"address": "",
"version": "",
"status": "",
"statusv2": ""
}
],
"repositories": [
{
"address": "",
"status": ""
}
],
"systemState": "",
"customerName": "",
"licenseFeatures": [],
"licenseType": "",
"installationId": "",
"time": "",
"timeZone": "",
"environmentUniqueId": "",
"licenseBlob": "",
"ecsStatus": "",
"ecsRegistrationURL": "",
"contentVersion": ""
}
Included playbooks
The Sample - Fortinet FortiEDR - 1.3.1 playbook collection comes bundled with the Fortinet FortiEDR connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the Fortinet FortiEDR connector.
- Create Exception
- Create IPSet
- Delete IPSet
- > FortiEDR > Create and Link Asset
- > FortiEDR > Fetch Events
- >> FortiEDR > Handle Macro
- FortiEDR > Ingest
- Get Agent Groups
- Get Collector List
- Get Event by ID
- Get Event Count
- Get Event Exceptions
- Get Event List Extended
- Get Events
- Get Exception List
- Get File
- Get IPSet List
- Get Raw Data Items
- Get Raw JSON Event Data
- Get System Summary
- Isolate Collector
- Remediate Device
- Retrieve File or Memory
- Search Filehash
- Unisolate Collector
- Update Events
- Update Exception
- Update IPSet
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during the connector upgrade and delete.
Data Ingestion Support
Use the Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling events from FortiEDR. Currently, "events" in FortiEDR are mapped to "alerts" in FortiSOAR™. For more information on the Data Ingestion Wizard, see the "Connectors Guide" in the FortiSOAR™ product documentation.
Configure Data Ingestion
You can configure data ingestion using the “Data Ingestion Wizard” to seamlessly map the incoming FortiEDR "Events" to FortiSOAR™ "Alerts".
The Data Ingestion Wizard enables you to configure the scheduled pulling of data from FortiEDR into FortiSOAR™. It also lets you pull some sample data from FortiEDR using which you can define the mapping of data between FortiEDR and FortiSOAR™. The mapping of common fields is generally already done by the Data Ingestion Wizard; users mostly require to only map any custom fields that are added to the FortiEDR event.
- To begin configuring data ingestion, click Configure Data Ingestion on the FortiEDR connector’s "Configurations" page.
Click Let’s Start by fetching some data, to open the “Fetch Sample Data” screen.
Sample data is required to create a field mapping between FortiEDR data and FortiSOAR™. The sample data is pulled from connector actions or ingestion playbooks.
- On the Fetch Data screen, provide the configurations required to fetch FortiEDR data.
Users can choose to pull data from FortiEDR by specifying the last X minutes based on which they want to pull events from FortiEDR, and you must specify the timezone such as UTC (default), Asia/Kolkata that you want to use to ingest data. You can also specify additional parameters such as event IDs, device names, collector groups, operating systems, device IPs, MAC addresses, classifications of events, etc., based on which events can be fetched from FortiEDR.
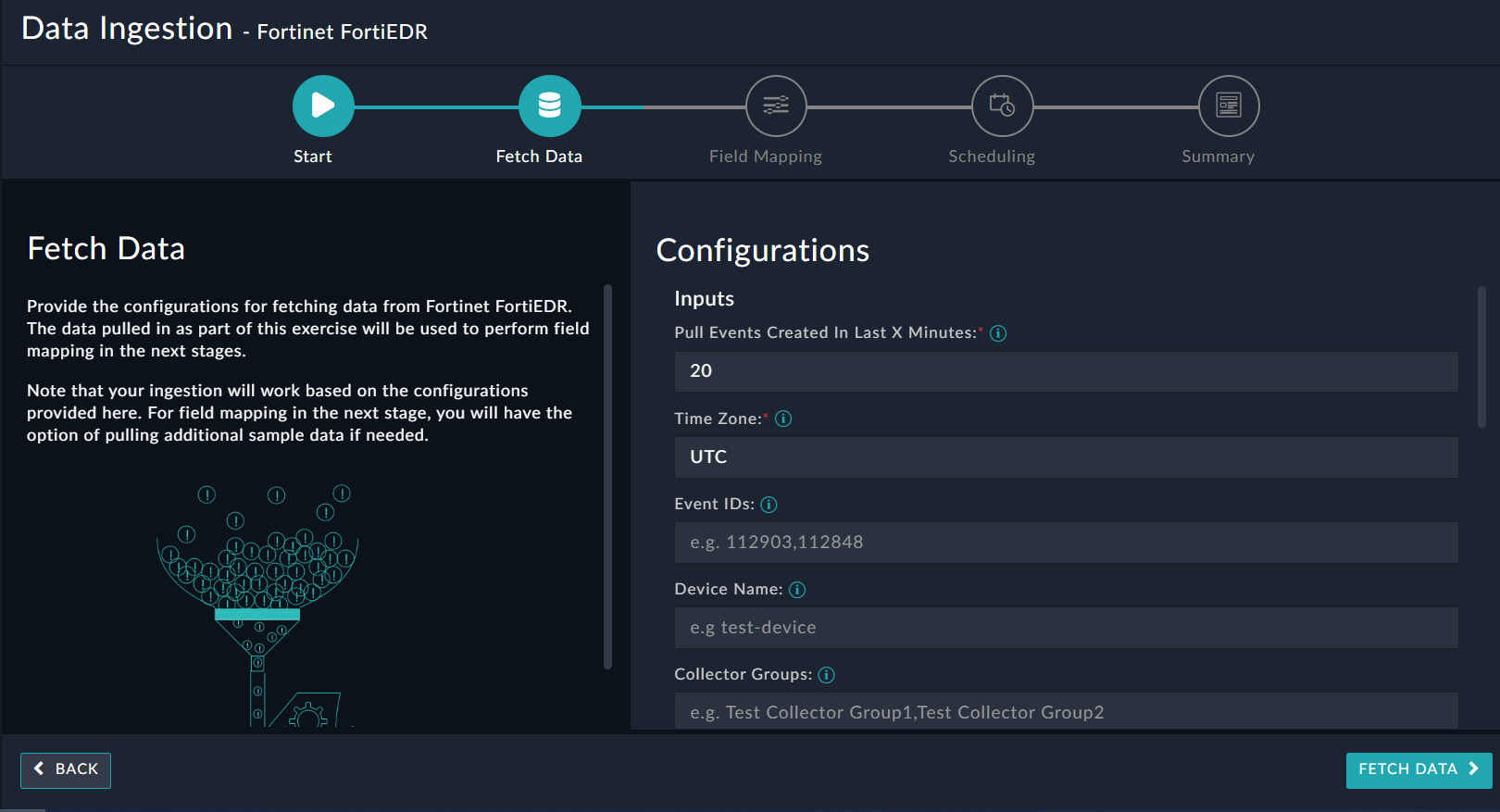
The fetched data is used to create a mapping between the FortiEDR data and FortiSOAR™ alerts. Once you have completed specifying the configurations, click Fetch Data.
-
On the Field Mapping screen, map the fields of a FortiEDR event to the fields of an alert present in FortiSOAR™.
To map a field, click the key in the sample data to add the “jinja” value of the field. For example, to map the device parameter of a FortiEDR event to the computer name parameter of a FortiSOAR™ alert, click the Computer Name field, and then click the device field to populate its keys:
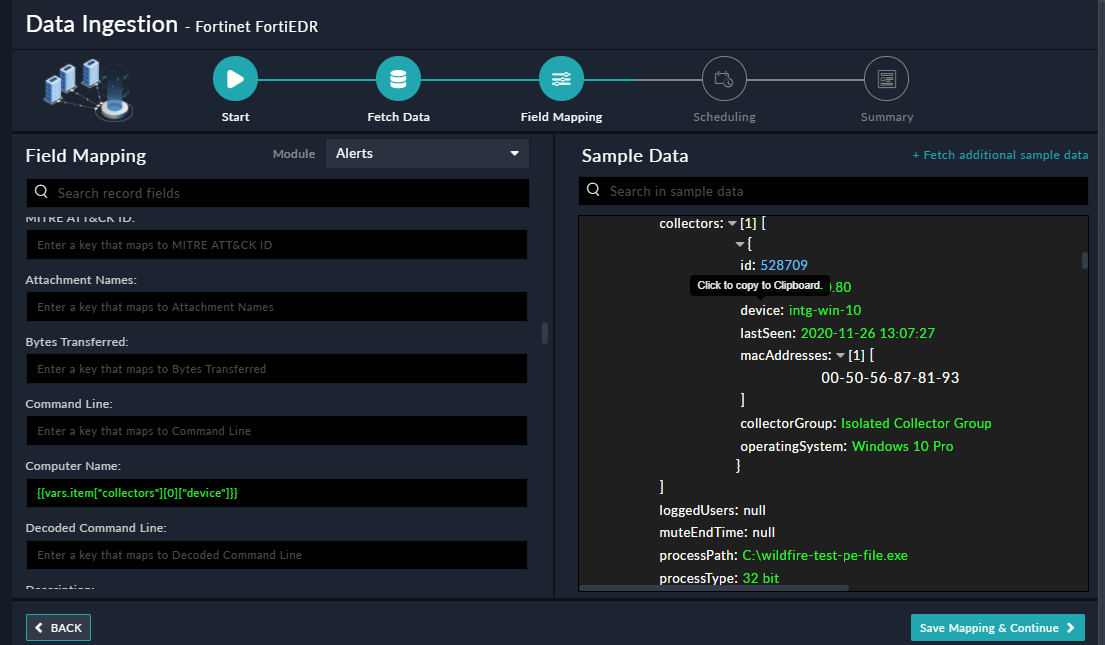
For more information on field mapping, see the Data Ingestion chapter in the "Connectors Guide" in the FortiSOAR™ product documentation. Once you have completed mapping fields, click Save Mapping & Continue.
-
Use the Scheduling screen to configure schedule-based ingestion, i.e., specify the polling frequency to FortiEDR, so that the content gets pulled from the FortiEDR integration into FortiSOAR™.
On the Scheduling screen, from the Do you want to schedule the ingestion? drop-down list, select Yes.
In the “Configure Schedule Settings” section, specify the Cron expression for the schedule. For example, if you want to pull data from FortiEDR every morning at 5 am, click Daily, and in the hour box enter 5 , and in the minute box enter 0:
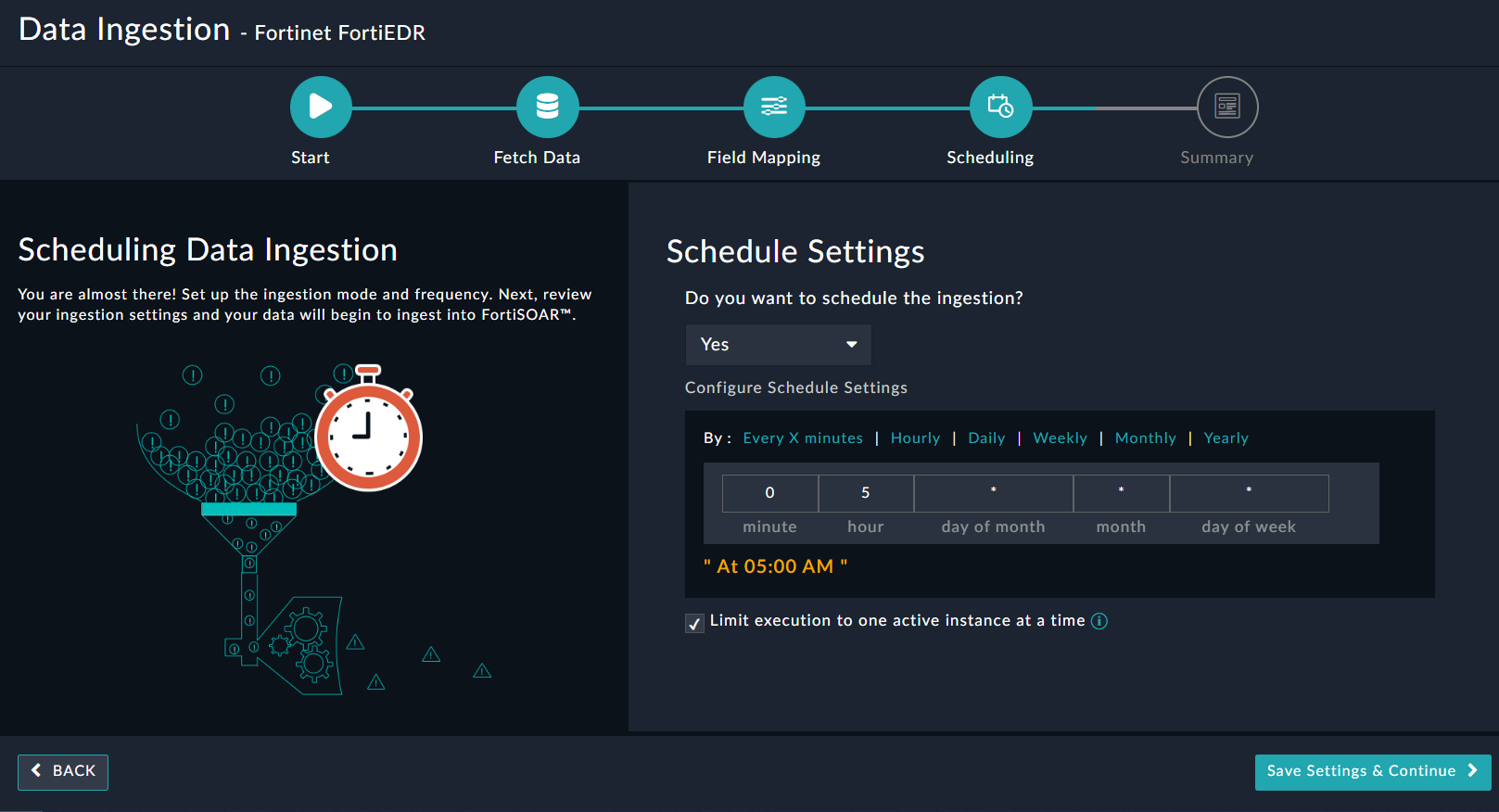
Once you have completed scheduling, click Save Settings & Continue.
-
The Summary screen displays a summary of the mapping done, and it also contains links to the Ingestion playbooks. Click Done to complete the data ingestion, and exit the Data Ingestion Wizard.









