About the connector
Cisco Stealthwatch uses NetFlow to provide visibility across the network, data center, branch offices, and the cloud. Its advanced security analytics uncover stealthy attacks on the extended network. Stealthwatch helps you use your existing network as a security sensor and enforcer to dramatically improve your threat defense.
This document provides information about the Stealthwatch connector, which facilitates automated interactions, with an Stealthwatch server using FortiSOAR™ playbooks. Add the Stealthwatch connector as a step in FortiSOAR™ playbooks and perform automated operations, such as retrieving details about domains and retrieving inbound and outbound traffic information for a specified datetime range, or for the last 24 hours.
Version information
Connector Version: 1.0.0
Compatibility with FortiSOAR™ Versions: 4.9.0.0-708 and later
Compatibility with Stealthwatch Versions: 6.9.1 and later
Installing the connector
For the procedure to install a connector, click here.
Prerequisites to configuring the connector
- You must have the URL of Stealthwatch server to which you will connect and perform the automated operations and the credentials to access that URL.
- To access the FortiSOAR™ UI, ensure that port 443 is open through the firewall for the FortiSOAR™ instance.
Configuring the connector
For the procedure to configure a connector, click here.
Configuration parameters
In FortiSOAR™, on the Connectors page, select the Stealthwatch connector and click Configure to configure the following parameters:
| Parameter |
Description |
| URL |
URL of the Stealthwatch server to which you will connect and perform the automated operations. |
| Username |
Username to access the Stealthwatch server. |
| Password |
Password to access the Stealthwatch server. |
| Verify SSL |
Verify SSL connection to the Stealthwatch server.
Defaults to True. |
Global Parameters
Calls from many Actions can require identifiers of various objects in the system. For example, Domain ID, Exporter IP, Host Group ID, Interface, and Flow Collector ID. You can obtain these identifiers by the following two methods:
Using the SMC Client
Use the Stealthwatch Management Console (SMC) client to obtain the identifiers as follows:
- In the SMC client interface, select your domain in the enterprise tree and then click Configuration > Properties.

This displays the Properties dialog:

- Select the Export All configuration option and click Export.
- Save the XML configuration file and after it is downloaded, open it with a text editor.
- Search for the identifiers in the configuration file by searching for "<name of the identifier. Some examples follow:
Locate the domainId by searching for “<domain id”.
Locate the hostGroupId by searching for “<host-group”.
Locate the interface if-index by searching for “<interface if-index=”.
Locate the exporterIp by searching for “<exporter ip=".
Using the Command Line Interface
You can also find parameter information from using a Command Line Interface (CLI). For example, type the following command to get a list of the host_id from a Flow Collector:
grep id= /lancope/var/sw/today/config/groups.xml | awk ' {print $2, $3, $4}' | sed s/\"//g| sed s/id=//g |awk '$1<60000'|sort -k1,1n |less
To get the Domain ID for an SMC, type the following command:
ls /lancope/var/smc/config/ | grep domain
Actions supported by the connector
The following automated operations can be included in playbooks:
- Get Domain Details: Retrieves information for all the domains.
- Get Application Traffic by Domain: Retrieves inbound and outbound traffic information for a specified Domain ID and datetime range. If you do not specify the datetime range then inbound and outbound traffic information is retrieved for the last 24 hours.
- Get Application Traffic by Host Group ID: Retrieves inbound and outbound traffic information for a specified Domain ID and datetime range. If you do not specify the datetime range then inbound and outbound traffic information is retrieved for the last 24 hours.
- Get Application Traffic by Exporter IP: Retrieves inbound and outbound traffic information for a specified Exporter IP and datetime range. If you do not specify the datetime range then inbound and outbound traffic information is retrieved for the last 24 hours.
operation: Get Domain Details
Input parameters
None.
Output
A customized JSON output that is formatted for easy reference is the output for all the operations.
The JSON contains information for all the domains.
Following image displays a sample output:

operation: Get Application Traffic by Domain
Input parameters
| Parameter |
Description |
| Domain ID |
ID of the domain for which you want to retrieve inbound and outbound traffic information. |
| Start Date/Time (optional) |
Start datetime in the 8601 format, from when you want to retrieve inbound and outbound traffic information. |
| End Date/Time (optional) |
End datetime in the 8601 format, till when you want to retrieve inbound and outbound traffic information. |
Note: If you do not specify the datetime range, then the inbound and outbound traffic information is retrieved for the last 24 hours.
Output
The JSON output contains the inbound and outbound traffic information for the datetime range and domain that you have specified.
Following image displays a sample output:

operation: Get Application Traffic by Host Group ID
Input parameters
| Parameter |
Description |
| Domain ID |
ID of the domain for which you want to retrieve inbound and outbound traffic information. |
| Host Group ID |
ID of the Host Group for which you want to retrieve inbound and outbound traffic information. |
| Start Date/Time (optional) |
Start datetime in the 8601 format, from when you want to retrieve inbound and outbound traffic information. |
| End Date/Time (optional) |
End datetime in the 8601 format, till when you want to retrieve inbound and outbound traffic information. |
Note: If you do not specify the datetime range, then the inbound and outbound traffic information is retrieved for the last 24 hours.
Output
The JSON output contains the inbound and outbound traffic information for the datetime range and Host Group IP that you have specified.
Following image displays a sample output:

operation: Get Application Traffic by Exporter IP
Input parameters
| Parameter |
Description |
| Domain ID |
ID of the domain for which you want to retrieve inbound and outbound traffic information. |
| Flow Collector Device ID |
ID of the Flow Collector Device generated by Stealthwatch. |
| Exporter IP Address |
IP of the Exporter, such as router or switch, for which you want to retrieve inbound and outbound traffic information. |
| Interface |
ID of the Interface created in Stealthwatch. |
| Start Date/Time (optional) |
Start datetime in the 8601 format, from when you want to retrieve inbound and outbound traffic information. |
| End Date/Time (optional) |
End datetime in the 8601 format, till when you want to retrieve inbound and outbound traffic information. |
Note: If you do not specify the datetime range, then the inbound and outbound traffic information is retrieved for the last 24 hours.
Output
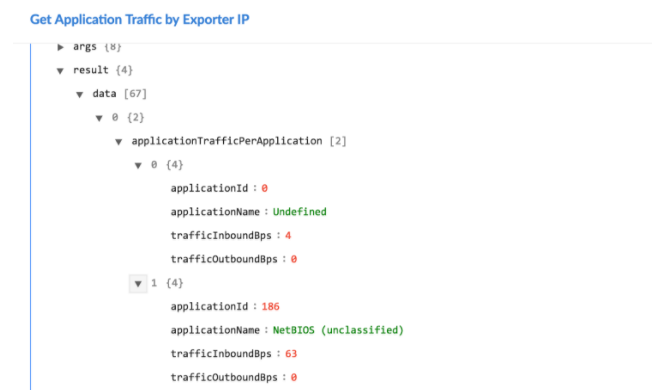
The JSON output contains the inbound and outbound traffic information for the datetime range and Exporter IP address that you have specified.
Following image displays a sample output:
Included playbooks
The Sample - Cisco Stealthwatch - 1.0.0 playbook collection comes bundled with the Cisco Stealthwatch connector. This playbook contains steps using which you can perform all supported actions. You can see the bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the Cisco Stealthwatch connector.
- Get Domain Details
- Get Application Traffic by Domain ID
- Get Application Traffic by Host Group ID
- Get Application Traffic by Exporter IP
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection, since the sample playbook collection gets deleted during connector upgrade and delete.











