CrowdStrike Endpoint Security
Support Added: FortiSIEM 5.2.1
Last Modification: FortiSIEM 6.2.0
Vendor Version Tested: Not Provided
Vendor: CrowdStrike
Product: Endpoint Security
Product Information: https://www.crowdstrike.com/endpoint-security-products/
Configuration
CrowdStrike Server Configuration
To configure the CrowdStrike server, take the following steps:
-
Sign in to the Falcon console.
-
Navigate to Support > API Clients and Keys > OAuth2 API Clients.
-
Click Add new API client.
-
In the Client name field, enter a descriptive client name.
-
For API SCOPES, select Event streams.
-
Click Add.
Keep a record of your API client secret. For security purposes, it is only shown when you create or reset the API client. If you lose your secret, you must reset it, which cuts off access for any integrations that still use the previous secret.
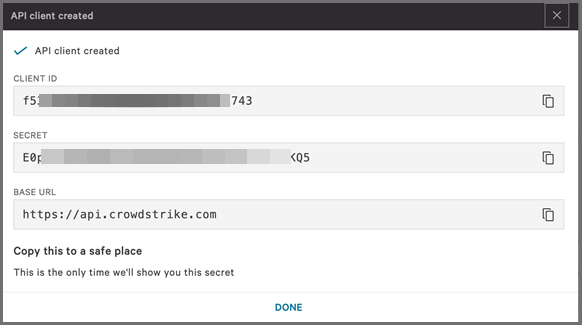
FortiSIEM Configuration
- Go to the ADMIN > Setup > Credentials tab.
- In Step 1: Enter Credentials, click New to create a CrowdStrike Falcon Credential:
- Follow the instructions in “Setting Credentials“ in the User's Guide to create a new credential.
- Enter these settings in the Access Method Definition dialog box and click Save:
Settings Description Name Enter a name for the credential Device Type CrowdStrike Falcon Access Protocol Falcon Streaming API UUID Enter the Client ID from the CrowdStrike Server Configuration for the UUID. API Secret Key Enter the Secret from the CrowdStrike Server Configuration for the API Secret Key. Organization Choose the organization if it is an MSP deployment and the same credential is to be used for multiple customers. Description Description of the device.
- In Step 2: Enter IP Range to Credential Associations, click New to create a mapping.
- Enter the host name in base URL from the CrowdStrike Server Configuration in the IP/Host Name field. For example,
https://api.crowdstrike.com. - Select the name of the credential created in step 2 from the Credentials drop-down list.
- Click Save.
- Enter the host name in base URL from the CrowdStrike Server Configuration in the IP/Host Name field. For example,
- Select the entry just created and click the Test drop-down list and select Test Connectivity without Ping. A pop up will appear and show the Test Connectivity results. Proceed to step 5 when connectivity succeeds.
- An entry is created in ADMIN > Setup > Pull Events corresponding to the event pull job. FortiSIEM will start to pull events from the CrowdStrike Cloud service using the Falcon Streaming API.
To test for events received via CrowdStrike:
- Go to ADMIN > Setup > Pull Events.
- Select the CrowdStrike entry and click Report.
The system will take you to the ANALYTICS tab and run a query to display the events received from CrowdStrike Cloud Service in the last 15 minutes. You can modify the time interval to get more events.
| Protocol | Information Discovered | Used For |
|---|---|---|
| Falcon Streaming API | Detection Summary, Authentication Log, Detection Status Update, Indicators of Compromise, Containment Audit Events, IP White-listing events, Sensor Grouping Events. | Security and Compliance |
| Falcon Data Replicator | Detection Summary, User Activity, Authentication Activity. | Security and Compliance |

