Tunnel interface configuration
You must assign a static IP address to the tunnel interface. This configuration is required to support BGP peering between the secure private access hub and the FortiSASE security points of presence.
|
|
The following settings are only examples. Do not consider them as recommended settings. |
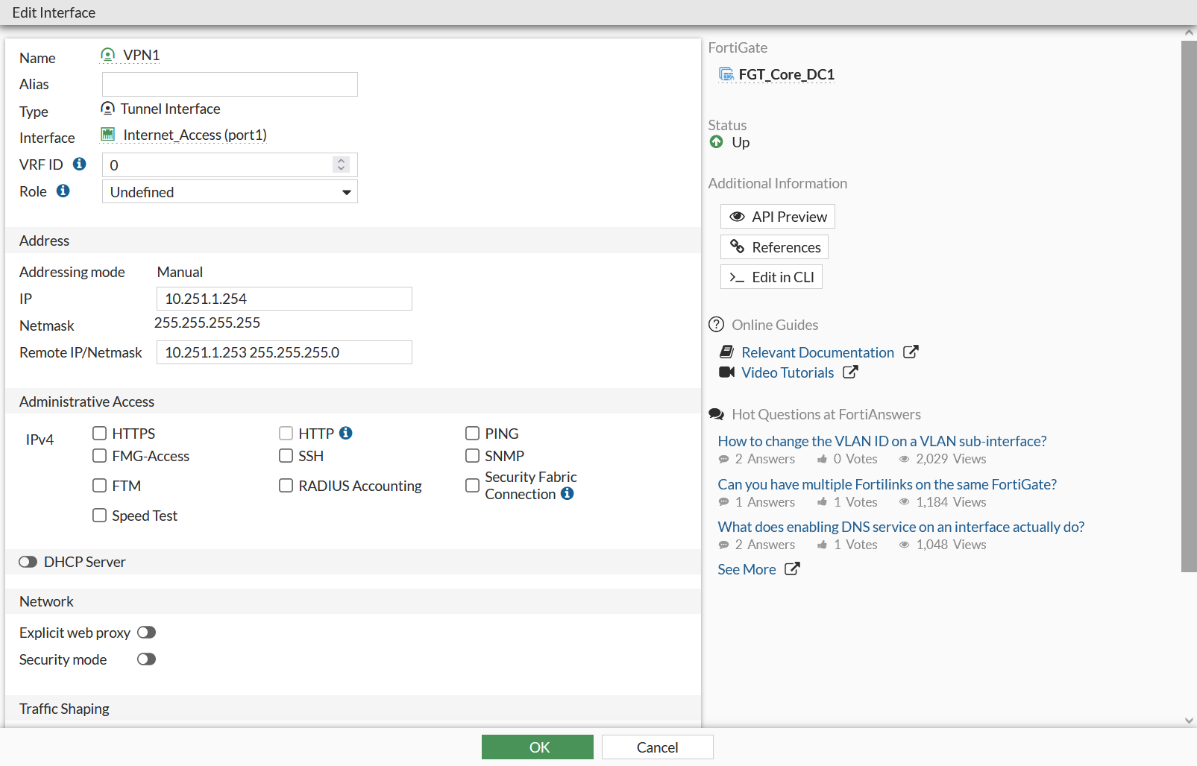
To create the tunnel interface using the GUI:
- Go to Network > Interfaces.
- Under Physical Interface, expand your WAN interface to display your IPsec VPN tunnel interface. Click the tunnel interface and click Edit.
- In the Edit Interface dialog, do the following:
- Set the IP and Remote IP/Netmask.
- For Administrative Access, select PING.
- Click OK to save the changes.
To create the tunnel interface using the CLI:
config system interface
edit "VPN1"
set vdom "root"
set ip 10.251.1.254 255.255.255.255
set allowaccess ping
set type tunnel
set remote-ip 10.251.1.253 255.255.255.0
set interface "port1"
next
end

