Design overview
In this architecture, these are the goals for remote users that connect to FortiSASE:
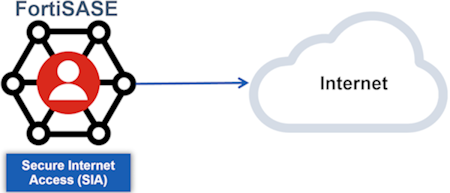
- Enforce secure internet access (SIA) when users access internet and web-based applications
- Allow secure private access (SPA) when users access private company-hosted applications that a FortiGate next-generation firewall (NGFW) protects
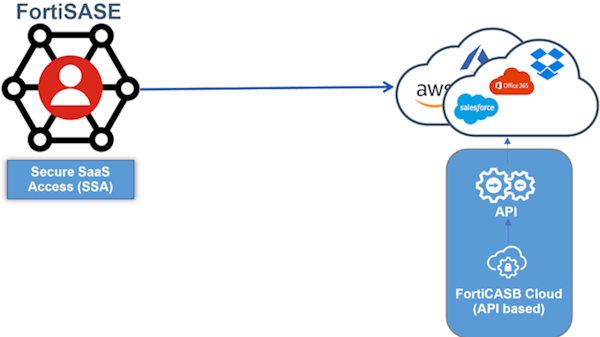
- Enforce secure SaaS access (SSA) when users access SaaS applications
SIA extends an organization’s security perimeter that an NGFW typically achieves to remote users by enforcing common security policy for Intrusion Prevention Systems and Application Control, Web and DNS filtering, and Anti-Malware, Sandboxing, and Anti-Botnet/Command and Control (C&C).
SPA using zero trust network access (ZTNA) secures private TCP-based applications, namely, leveraging FortiSASE integration with the FortiGate ZTNA access proxy. For a design overview specific to FortiGate ZTNA architecture, see the ZTNA Architecture Guide.

For securing private TCP-based and UDP-based applications, FortiSASE supports SPA using SD-WAN or SPA using an NGFW converted to a standalone FortiSASE SPA hub.

SSA uses FortiCASB for advanced API-based deep inspection of cloud activity to provide monitoring, analysis, and reporting features that alert network administrators of any suspicious user activity, threats, or security policy violations. Insights that FortiCASB determines can then be acted upon by network administrators to enhance FortiSASE security features and settings to block and mitigate such detected activity.
SSA can also use FortiSASE Inline-CASB functionality, which enforces security policies inline with the traffic used to access cloud applications. Therefore, unlike API-based CASB solutions, which rely on out-of-band traffic, using inline-CASB functionality, FortiSASE can block remote user access to cloud-based applications.


