Supplicant configurations
Supplicant Configurations define an SSID and security parameters required to configure the native supplicant available on a connecting host as part of its operating system.
When a host connects to the network and requires the use of a supplicant, the host and user data are compared to each Supplicant Policy starting with the first policy in the list. When a policy is found where the host and user data match the User/Host Profile in the policy, that policy is applied. The Supplicant Configuration contained within that policy configures the supplicant on the host.
See Navigation and Filters for information on common navigation tools and data filters.
Settings
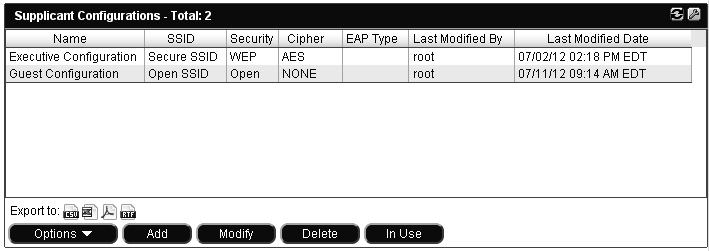
An empty field in a column indicates that the option has not been set.
|
Field |
Definition |
||
|---|---|---|---|
|
Name |
User defined name for the Configuration. |
||
|
SSID |
Name of the SSID being configured. This is not necessarily the SSID to which the host is connected. However, the agent will attempt to move the host to this SSID when the configuration is applied.
|
||
|
Security |
Indicates the type of encryption that will be used for connections to this SSID. Options include:
|
||
|
Cipher |
Encryption/decryption method used in conjunction with the information in the Security field to secure this connection. Options include:
|
||
|
EAP Type |
Currently only PEAP is supported. |
||
|
Note |
User specified note field. |
||
|
Last Modified By |
User name of the last user to modify the record. |
||
|
Last Modified Date |
Date and time of the last modification to this configuration. |
||
|
Right click options |
|||
|
Delete |
Deletes the selected Supplicant Configuration. |
||
|
In Use |
Indicates whether or not the selected configuration is currently being used by any other FortiNAC element. See Configurations in use. |
||
|
Modify |
Opens the Modify Supplicant Configuration window for the selected configuration. |
||
|
Show Audit Log |
Opens the Admin Auditing Log showing all changes made to the selected item. For information about the Admin Auditing Log, see Admin auditing.
|
||
|
Buttons |
|||
|
Export |
Exports the data displayed to a file in the default downloads location. File types include CSV, Excel, PDF or RTF. See Export data. |
||

