Allow IPsec DPD in FGSP members to support failovers 7.2.1
In conjunction with support for FGSP per-tunnel failover for IPsec 7.2.1, configuring DPD (dead peer detection) on an FGSP member is permitted. This allows a failed FGSP member to send out DPD probes during failover to detect unreachable remote peers and to flush the corresponding tunnels.
Example
In this example, using the same configuration as in FGSP per-tunnel failover for IPsec 7.2.1, a tunnel can be established from one of the remote IPsec clients to one of the FGSP members (DC1_VM1). DPD can be set to on-idle, with a configured dpd-retryinterval of 60 seconds. When a client disappears, whether it is due to remote client failures or server-side routing failures, the FGSP member or gateway (DC1_VM1) will send out DPD probes for detection. Once the three iterations are complete and no responses are detected, the FGSP member will flush the tunnel and remove any routing to that peer.
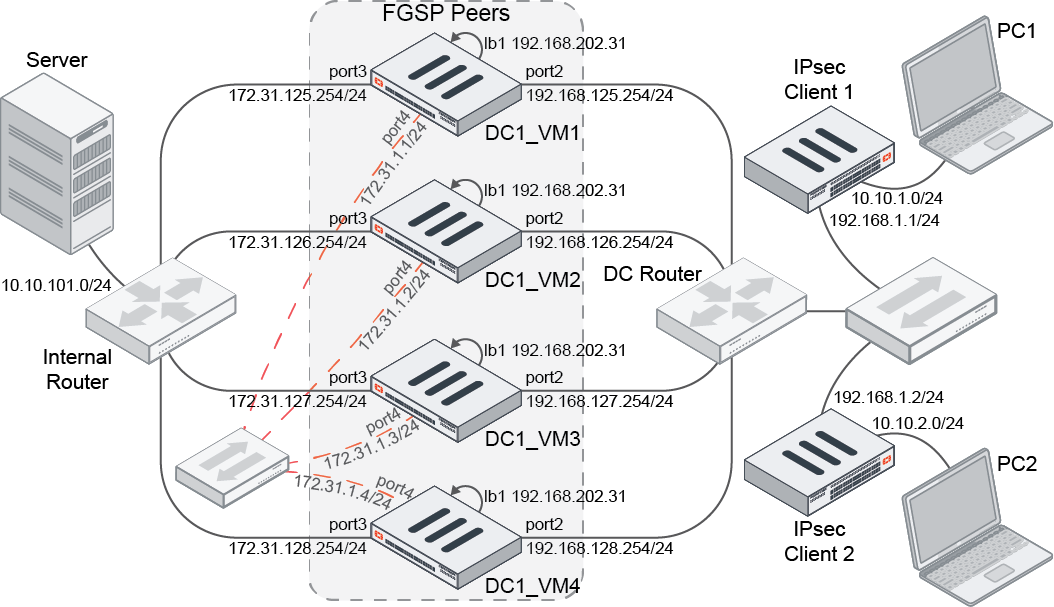
|
Interface/setting |
DC1_VM1 |
DC1_VM2 |
DC1_VM3 |
DC1_VM4 |
|---|---|---|---|---|
|
port2 |
192.168.125.254/24 |
192.168.126.254/24 |
192.168.127.254/24 |
192.168.128.254/24 |
|
port3 |
172.31.125.254/24 |
172.31.126.254/24 |
172.31.127.254/24 |
172.31.128.254/24 |
|
port4 |
172.31.1.1/24 |
172.31.1.2/24 |
172.31.1.3/24 |
172.31.1.4/24 |
|
lb1 |
192.168.202.31/32 |
192.168.202.31/32 |
192.168.202.31/32 |
192.168.202.31/32 |
|
|
Enabled |
Enabled |
Enabled |
Disabled |
To configure the FGSP peers (DC1_VM1):
|
|
The following steps are to configure DC1_VM1. The other peers have similar configurations based on the preceding table. In the |
-
Configure the FGSP settings:
config system standalone-cluster set standalone-group-id 1 set group-member-id 1 config cluster-peer edit 1 set peerip 172.31.1.2 next edit 2 set peerip 172.31.1.3 next edit 3 set peerip 172.31.1.4 next end end -
Configure the VPN tunnel phase 1 settings:
config vpn ipsec phase1-interface edit "vpn1" set type dynamic set interface "port2" set ike-version 2 set local-gw 192.168.202.31 set keylife 90000 set peertype one set net-device disable set proposal aes128-sha1 set dpd on-idle set dhgrp 2 set fgsp-sync enable set nattraversal disable set peerid "Nokia_Peer" set psksecret xxxxx set dpd-retryinterval 60 next end -
Configure the VPN tunnel phase 2 settings:
config vpn ipsec phase2-interface edit "vpn1" set phase1name "vpn1" set proposal aes128-sha1 set keylifeseconds 10800 next end
To verify the configuration:
-
Once the FGSP members establish peering with each other, verify the standalone peers on DC1_VM1:
DC1_VM1 # diagnose sys ha standalone-peers Group=1, ID=1 Detected-peers=3 Kernel standalone-peers: num=3. peer0: vfid=0, peerip:port = 172.31.1.2:708, standalone_id=2 session-type: send=0, recv=0 packet-type: send=0, recv=0 peer1: vfid=0, peerip:port = 172.31.1.3:708, standalone_id=3 session-type: send=0, recv=0 packet-type: send=0, recv=0 peer2: vfid=0, peerip:port = 172.31.1.4:708, standalone_id=4 session-type: send=0, recv=0 packet-type: send=0, recv=0 Kernel standalone dev_base: standalone_id=0: standalone_id=1: phyindex=0: mac=00:0c:29:22:00:6b, linkfail=1 phyindex=1: mac=00:0c:29:22:00:75, linkfail=1 phyindex=2: mac=00:0c:29:22:00:7f, linkfail=1 phyindex=3: mac=00:0c:29:22:00:89, linkfail=1 phyindex=4: mac=00:0c:29:22:00:93, linkfail=1 phyindex=5: mac=00:0c:29:22:00:9d, linkfail=1 phyindex=6: mac=00:0c:29:22:00:a7, linkfail=1 phyindex=7: mac=00:0c:29:22:00:b1, linkfail=1 phyindex=8: mac=00:0c:29:22:00:bb, linkfail=1 phyindex=9: mac=00:0c:29:22:00:c5, linkfail=1 standalone_id=2: phyindex=0: mac=00:0c:29:06:4e:d6, linkfail=1 phyindex=1: mac=00:0c:29:06:4e:e0, linkfail=1 phyindex=2: mac=00:0c:29:06:4e:ea, linkfail=1 phyindex=3: mac=00:0c:29:06:4e:f4, linkfail=1 phyindex=4: mac=00:0c:29:06:4e:fe, linkfail=1 phyindex=5: mac=00:0c:29:06:4e:08, linkfail=1 phyindex=6: mac=00:0c:29:06:4e:12, linkfail=1 phyindex=7: mac=00:0c:29:06:4e:1c, linkfail=1 phyindex=8: mac=00:0c:29:06:4e:26, linkfail=1 phyindex=9: mac=00:0c:29:06:4e:30, linkfail=1 standalone_id=3: phyindex=0: mac=00:0c:29:70:b9:6c, linkfail=1 phyindex=1: mac=00:0c:29:70:b9:76, linkfail=1 phyindex=2: mac=00:0c:29:70:b9:80, linkfail=1 phyindex=3: mac=00:0c:29:70:b9:8a, linkfail=1 phyindex=4: mac=00:0c:29:70:b9:94, linkfail=1 phyindex=5: mac=00:0c:29:70:b9:9e, linkfail=1 phyindex=6: mac=00:0c:29:70:b9:a8, linkfail=1 phyindex=7: mac=00:0c:29:70:b9:b2, linkfail=1 phyindex=8: mac=00:0c:29:70:b9:bc, linkfail=1 phyindex=9: mac=00:0c:29:70:b9:c6, linkfail=1 standalone_id=4: phyindex=0: mac=00:0c:29:5c:d3:23, linkfail=1 phyindex=1: mac=00:0c:29:5c:d3:2d, linkfail=1 phyindex=2: mac=00:0c:29:5c:d3:37, linkfail=1 phyindex=3: mac=00:0c:29:5c:d3:41, linkfail=1 phyindex=4: mac=00:0c:29:5c:d3:4b, linkfail=1 phyindex=5: mac=00:0c:29:5c:d3:55, linkfail=1 phyindex=6: mac=00:0c:29:5c:d3:5f, linkfail=1 phyindex=7: mac=00:0c:29:5c:d3:69, linkfail=1 phyindex=8: mac=00:0c:29:5c:d3:73, linkfail=1 phyindex=9: mac=00:0c:29:5c:d3:7d, linkfail=1 standalone_id=5: ... standalone_id=15: -
Initiate a dialup tunnel connection from the IPsec Client 2 FortiGate (192.168.1.2).
-
Verify the tunnel list for vpn1_1 on each peer.
-
DC1_VM1:
DC1_VM1 # diagnose vpn tunnel list name vpn1_1 list ipsec tunnel by names in vd 0 ------------------------------------------------------ name=vpn1_1 ver=2 serial=a4 192.168.202.31:0->192.168.1.2:0 tun_id=192.168.1.2 tun_id6=::10.0.0.15 dst_mtu=1500 dpd-link=on weight=1 bound_if=6 lgwy=static/1 tun=intf/0 mode=dial_inst/3 encap=none/8840 options[2288]=npu rgwy-chg frag-rfc run_state=0 role=sync-primary accept_traffic=1 overlay_id=0 parent=vpn1 index=1 proxyid_num=1 child_num=0 refcnt=6 ilast=6 olast=6 ad=/0 stat: rxp=0 txp=0 rxb=0 txb=0 dpd: mode=on-idle on=1 idle=60000ms retry=3 count=0 seqno=20 natt: mode=none draft=0 interval=0 remote_port=0 fec: egress=0 ingress=0 proxyid=vpn1 proto=0 sa=1 ref=2 serial=3 add-route src: 0:0.0.0.0-255.255.255.255:0 dst: 0:10.10.1.0-10.10.1.255:0 SA: ref=3 options=682 type=00 soft=0 mtu=1438 expire=10480/0B replaywin=2048 seqno=1 esn=0 replaywin_lastseq=00000000 qat=0 rekey=0 hash_search_len=1 life: type=01 bytes=0/0 timeout=10788/10800 dec: spi=a575b631 esp=aes key=16 5de449f75c7d70258f4972506dd164e2 ah=sha1 key=20 7e65d641be6bc52655619ff542c67c61713de523 enc: spi=10aa45b0 esp=aes key=16 65ad3b4849386deb4f3028079a657257 ah=sha1 key=20 b5f1e1c6786f69482b5d271347a69a0cbb83ed58 dec:pkts/bytes=0/0, enc:pkts/bytes=0/0 npu_flag=00 npu_rgwy=192.168.1.2 npu_lgwy=192.168.202.31 npu_selid=b2 dec_npuid=0 enc_npuid=0 -
DC1_VM2:
DC1_VM2 # diagnose vpn tunnel list name vpn1_1 list ipsec tunnel by names in vd 0 ------------------------------------------------------ name=vpn1_1 ver=2 serial=a3 192.168.202.31:0->192.168.1.2:0 tun_id=192.168.1.2 tun_id6=::10.0.0.15 dst_mtu=0 dpd-link=on weight=1 bound_if=6 lgwy=static/1 tun=intf/0 mode=dial_inst/3 encap=none/8712 options[2208]=npu frag-rfc run_state=0 role=standby accept_traffic=1 overlay_id=0 parent=vpn1 index=1 proxyid_num=1 child_num=0 refcnt=6 ilast=43063501 olast=43063501 ad=/0 stat: rxp=0 txp=0 rxb=0 txb=0 dpd: mode=on-idle on=1 idle=60000ms retry=3 count=0 seqno=0 natt: mode=none draft=0 interval=0 remote_port=0 fec: egress=0 ingress=0 proxyid=vpn1 proto=0 sa=1 ref=2 serial=3 add-route src: 0:0.0.0.0-255.255.255.255:0 dst: 0:10.10.1.0-10.10.1.255:0 SA: ref=3 options=682 type=00 soft=0 mtu=1280 expire=10466/0B replaywin=2048 seqno=10000001 esn=0 replaywin_lastseq=00000000 qat=0 rekey=0 hash_search_len=1 life: type=01 bytes=0/0 timeout=10788/10800 dec: spi=a575b631 esp=aes key=16 5de449f75c7d70258f4972506dd164e2 ah=sha1 key=20 7e65d641be6bc52655619ff542c67c61713de523 enc: spi=10aa45b0 esp=aes key=16 65ad3b4849386deb4f3028079a657257 ah=sha1 key=20 b5f1e1c6786f69482b5d271347a69a0cbb83ed58 dec:pkts/bytes=0/0, enc:pkts/bytes=0/0 npu_flag=00 npu_rgwy=192.168.1.2 npu_lgwy=192.168.202.31 npu_selid=ab dec_npuid=0 enc_npuid=0 -
DC1_VM3:
DC1_VM3 # diagnose vpn tunnel list name vpn1_1 list ipsec tunnel by names in vd 0 ------------------------------------------------------ name=vpn1_1 ver=2 serial=ac 192.168.202.31:0->192.168.1.2:0 tun_id=192.168.1.2 tun_id6=::10.0.0.15 dst_mtu=0 dpd-link=on weight=1 bound_if=6 lgwy=static/1 tun=intf/0 mode=dial_inst/3 encap=none/8712 options[2208]=npu frag-rfc run_state=0 role=standby accept_traffic=1 overlay_id=0 parent=vpn1 index=1 proxyid_num=1 child_num=0 refcnt=6 ilast=43063499 olast=43063499 ad=/0 stat: rxp=0 txp=0 rxb=0 txb=0 dpd: mode=on-idle on=1 idle=60000ms retry=3 count=0 seqno=0 natt: mode=none draft=0 interval=0 remote_port=0 fec: egress=0 ingress=0 proxyid=vpn1 proto=0 sa=1 ref=2 serial=2 add-route src: 0:0.0.0.0-255.255.255.255:0 dst: 0:10.10.1.0-10.10.1.255:0 SA: ref=3 options=682 type=00 soft=0 mtu=1280 expire=10462/0B replaywin=2048 seqno=10000001 esn=0 replaywin_lastseq=00000000 qat=0 rekey=0 hash_search_len=1 life: type=01 bytes=0/0 timeout=10788/10800 dec: spi=a575b631 esp=aes key=16 5de449f75c7d70258f4972506dd164e2 ah=sha1 key=20 7e65d641be6bc52655619ff542c67c61713de523 enc: spi=10aa45b0 esp=aes key=16 65ad3b4849386deb4f3028079a657257 ah=sha1 key=20 b5f1e1c6786f69482b5d271347a69a0cbb83ed58 dec:pkts/bytes=0/0, enc:pkts/bytes=0/0 npu_flag=00 npu_rgwy=192.168.1.2 npu_lgwy=192.168.202.31 npu_selid=b4 dec_npuid=0 enc_npuid=0
-
-
When a shut down occurs on the VPN client to vpn1_2, verify the IKE debug messages on DC1_VM2. There are three iterations of DPD probes:
DC1_VM2 # diagnose debug enable DC1_VM2 # diagnose debug application ike -1 ... ike 0:vpn1_2: link is idle 6 192.168.202.31->192.168.4.2:0 dpd=1 seqno=72 rr=0 ike 0:vpn1_2:171: send IKEv2 DPD probe, seqno 114 ike 0:vpn1_2:158: sending NOTIFY msg ike 0:vpn1_2:171:158: send informational ike 0:vpn1_2:171: sent IKE msg (INFORMATIONAL): 192.168.202.31:500->192.168.4.2:500, len=76, vrf=0, id=87458c81a3be17f9/c8db7d3f2c70e638:00000004 ike 0: comes 192.168.1.2:500->192.168.202.31:500,ifindex=6,vrf=0... ike 0:vpn1_2: link is idle 6 192.168.202.31->192.168.4.2:0 dpd=1 seqno=72 rr=0 ike 0:vpn1_2:171: send IKEv2 DPD probe, seqno 114 ike 0:vpn1_2:158: sending NOTIFY msg ike 0:vpn1_2:171:158: send informational ike 0:vpn1_2:171: sent IKE msg (INFORMATIONAL): 192.168.202.31:500->192.168.4.2:500, len=76, vrf=0, id=87458c81a3be17f9/c8db7d3f2c70e638:00000004 ike 0: comes 192.168.1.2:500->192.168.202.31:500,ifindex=6,vrf=0.... ike 0:vpn1_2: link is idle 6 192.168.202.31->192.168.4.2:0 dpd=1 seqno=72 rr=0 ike 0:vpn1_2:171: send IKEv2 DPD probe, seqno 114 ike 0: comes 192.168.1.2:500->192.168.202.31:500,ifindex=6,vrf=0.... ike 0:vpn1_2:171: 87458c81a3be17f9/c8db7d3f2c70e638 negotiation of IKE SA failed due to retry timeout ike 0:vpn1_2:171: expiring IKE SA 87458c81a3be17f9/c8db7d3f2c70e638 ike 0:vpn1_2: deleting ike 0:vpn1_2: flushing ike 0:vpn1_2: deleting IPsec SA with SPI 85700354 ike 0:vpn1_2:vpn1: deleted IPsec SA with SPI 85700354, SA count: 0 ike 0:vpn1_2: sending SNMP tunnel DOWN trap for vpn1 ike 0:vpn1_2: sending tunnel down event for addr 10.10.4.0 ike 0:vpn1_2:vpn1: delete ike 0:vpn1:152: del route 10.10.4.0/255.255.255.0 tunnel 192.168.4.2 oif vpn1(21) metric 15 priority 1 ike 0:vpn1_2: flushed ike 0:vpn1_2:171: HA send IKE SA del 87458c81a3be17f9/c8db7d3f2c70e638 ike 0:vpn1_2:171:159: send informational ike 0:vpn1_2:171: sent IKE msg (INFORMATIONAL): 192.168.202.31:500->192.168.4.2:500, len=76, vrf=0, id=87458c81a3be17f9/c8db7d3f2c70e638:00000005 ike 0:vpn1_2: delete dynamic ike 0:vpn1_2: deleted

