Rename FortiAI to FortiNDR
FortiAI has been renamed FortiNDR in the GUI and CLI to align with the FortiNDR rebranding. Previous CLI-only settings for sending files to FortiNDR for inspection can be configured from the AntiVirus profile Page in the GUI.
|
|
FortiNDR is still referred to as |
Summary of GUI changes
The Fabric connector Type has been updated to FortiNDR, which is visible in the connector tooltip. In this example, the connector is running version 1.5.3, so the connector name still begins with FAI.

In this example, the connector is running version 7.0.0, so the connector name has changed to FortiNDR-VM.

When creating or editing an antivirus profile, there is an option in the ATP Protection Options section to Send files to FortiNDR for inspection. FortiNDR must be configured and inspecting at least one protocol to enable this option.
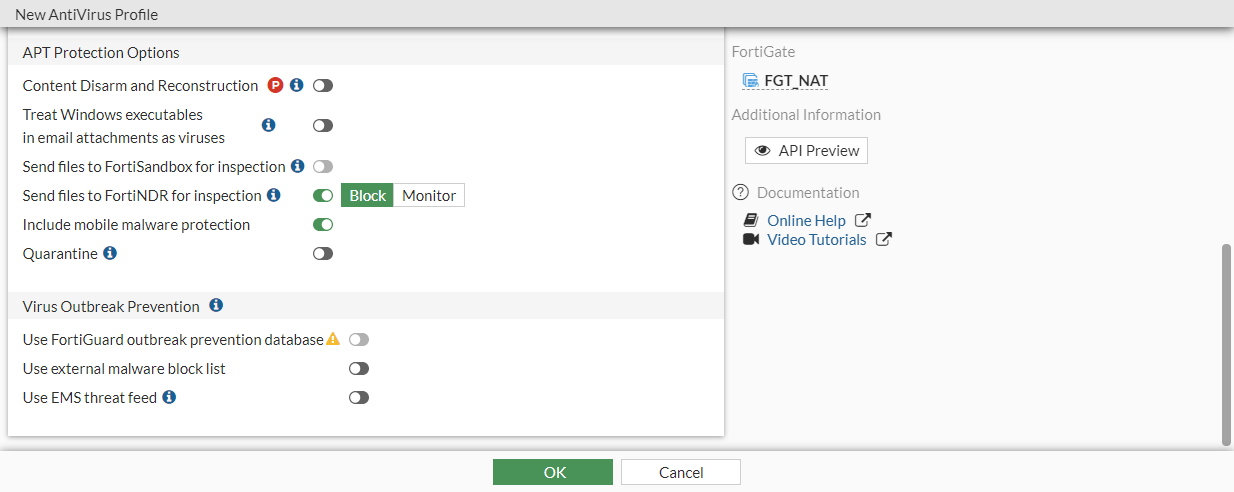
The replacement message for blocked files by FortiNDR follows the Virus Block Page format (antivirus scan).
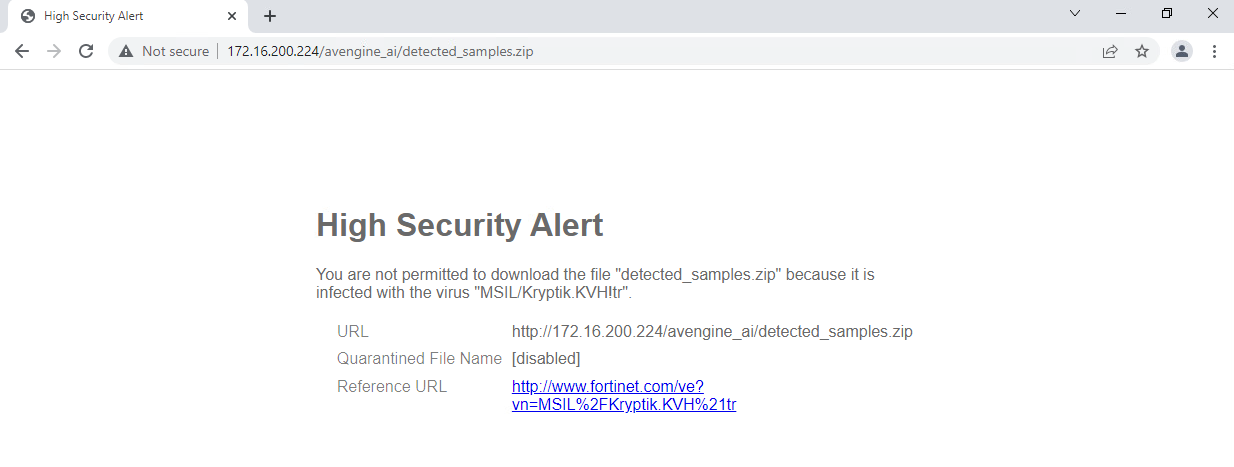
Summary of CLI changes
To enable FortiNDR:
config system fortindr
set status {enable | disable}
end
To configure FortiNDR settings in an antivirus profile:
config antivirus profile
edit <name>
set feature-set proxy
config {http | ftp | imap | pop3 | smtp | mapi | nntp | cifs | ssh}
set fortindr {disable | block | monitor}
end
set fortindr-error-action {ignore | log-only | block}
set fortindr-timeout-action {ignore | log-only | block}
next
end
Summary of log changes
The eventtype, msg, dtype, faiaction, faiseverity, faiconfidence, faifileid, and faifiletype fields have been updated to reference FortiNDR.
Sample log
1: date=2022-03-14 time=11:22:43 eventtime=1647282163586828798 tz="-0700" logid="0209008220" type="utm" subtype="virus" eventtype="fortindr" level="warning" vd="vdom1" policyid=1 poluuid="d2dc90d4-a011-51ec-2248-f6a8174bc745" policytype="policy" msg="Blocked by FortiNDR." action="blocked" service="HTTP" sessionid=115020 srcip=10.1.100.221 dstip=172.16.200.224 srcport=57396 dstport=80 srccountry="Reserved" dstcountry="Reserved" srcintf="port2" srcintfrole="undefined" dstintf="port1" dstintfrole="undefined" srcuuid="9a84ed44-a011-51ec-2550-75ae29f786ce" dstuuid="9a84ed44-a011-51ec-2550-75ae29f786ce" proto=6 direction="incoming" filename="detected_samples.zip" quarskip="Quarantine-disabled" virus="MSIL/Kryptik.KVH!tr" viruscat="Trojan" dtype="fortindr" ref="http://www.fortinet.com/ve?vn=MSIL%2FKryptik.KVH%21tr" virusid=0 url="http://172.16.200.224/avengine_ai/detected_samples.zip" profile="av" agent="curl/7.68.0" httpmethod="GET" analyticssubmit="false" fndraction="deny" fndrseverity="high" fndrconfidence="high" fndrfileid=155804 fndrfiletype="ZIP" crscore=50 craction=2 crlevel="critical"

