Manage FortiSwitch units on VXLAN interfaces
You can use Virtual Extensible LAN (VXLAN) interfaces to create a layer-2 overlay network when managing a FortiSwitch unit over a layer-3 network. After a VXLAN tunnel is set up between a FortiGate device and a FortiSwitch unit, the FortiGate device can use the VXLAN interface to manage the FortiSwitch unit. Only the management traffic uses the VXLAN tunnel; the FortiSwitch data traffic does not go through the VXLAN tunnel to the FortiGate device.
In the following configuration example, the FG-500E device is connected with a VXLAN tunnel to the FS-524D unit. After FortiLink is enabled on the VXLAN interface, the FortiGate device can managed the FortiSwitch unit.
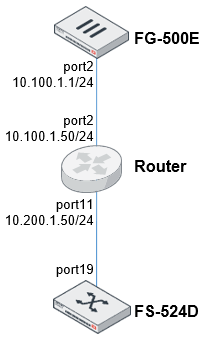
To manage the FortiSwitch unit with the VXLAN interface:
-
Configure the FortiSwitch unit.
-
Configure the FortiGate device.
Configure the FortiSwitch unit
-
Configure a VLAN to use as the VXLAN interface.
config system interface
edit "vlan-1000"
set ip 10.200.1.2 255.255.255.0
set vlanid 1000
set interface "internal"
next
end
-
Configure the VXLAN interface with the remote IP address of the FortiGate device.
config system vxlan
edit "vx-4094"
set vni 123456
set vlanid 4094
set interface "vlan-1000"
set remote-ip "10.100.1.1"
next
end
-
Configure a static route with the VXLAN remote IP address as the destination.
config router static
edit 1
set device "vlan-1000"
set dst 10.100.1.1 255.255.255.255
set gateway 10.200.1.50
next
end
-
Set up the switch port that physically connects to the router and enable FortiLink mode over layer-3 network.
config switch interface
edit port19
set fortilink-l3-mode enable
end
-
Configure the switch trunk to make it static and disable the automatic VLAN provisioning.
config switch trunk
edit "__FoRtILnk0L3__"
set auto-isl 1
set static-isl enable
set static-isl-auto-vlan disable
set members "port19"
next
end
-
Configure the FortiLink interface to set the native VLAN to match the VLAN used for the VXLAN defined in step 1.
config switch interface
edit "__FoRtILnk0L3__"
set native-vlan 1000
set allowed-vlans 1,1000,4088-4094
set dhcp-snooping trusted
....
next
end
-
Enable DHCP discovery.
config switch-controller global
set ac-discovery-type dhcp
end
Configure the FortiGate device
-
Configure the system interface.
config system interface
edit "port2"
set vdom "root"
set ip 10.100.1.1 255.255.255.0
set allowaccess ping https http
set type physical
set snmp-index 4
next
end
-
Configure the VXLAN interface.
config system vxlan
edit "flk-vxlan"
set interface "port2"
set vni 123456
set remote-ip "10.200.1.2"
next
end
-
Configure the FortiLink interface as the VXLAN type and set the IP address.
config system interface
edit "flk-vxlan"
set vdom "root"
set fortilink enable
set ip 10.255.2.1 255.255.255.0
set allowaccess ping fabric
set type vxlan
set lldp-reception enable
set lldp-transmission enable
set snmp-index 26
set interface "port2"
next
end
-
Configure a static route.
config router static
edit 2
set dst 10.200.1.0 255.255.255.0
set gateway 10.100.1.50
set distance 5
set device "port2"
next
end
-
Configure the DHCP server with option 138 to provide the switch-controller IP address to the FortiSwitch unit. DNS and NTP services are provided by the FortiGate device.
config system dhcp server
edit 6
set dns-service local
set ntp-service local
set default-gateway 10.255.2.1
set netmask 255.255.255.0
set interface "flk-vxlan"
config ip-range
edit 1
set start-ip 10.255.2.2
set end-ip 10.255.2.254
next
end
config options
edit 1
set code 138
set type ip
set ip "10.255.2.1"
next
end
set vci-match enable
set vci-string "FortiSwitch"
next
end

