ZTNA access proxy with SAML and MFA using FortiAuthenticator example
ZTNA access proxy supports device verification using device certificates that are issued by EMS. To authenticate users, administrators can use either basic or SAML authentication. An advantage of SAML authentication is that multi-factor authentication (MFA) can be provided by the SAML Identity Provider (IdP).
In these examples, a FortiAuthenticator is used as the IdP, and MFA is applied to user authentication for remote users accessing the web, RDP, and SSH resources over the ZTNA access proxy. It is assumed that the FortiGate EMS fabric connector has already been successfully connected.
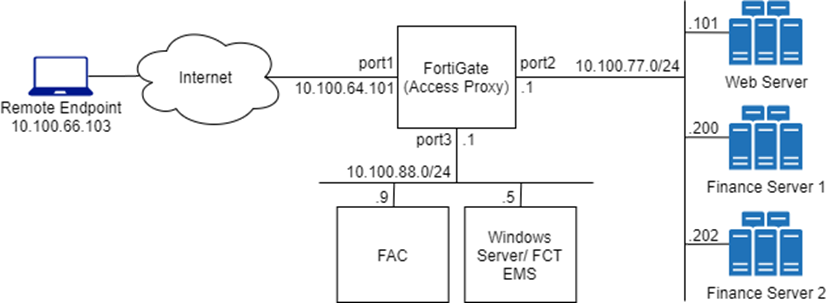
DNS resolutions:
-
ztna.fortidemo.fortinet.com:20443 -> 10.100.64.201:20443
-
entcore.fortidemo.fortinet.com:20443 -> 10.100.64.201:20443
-
fac.fortidemo.fortinet.com - > 10.100.64.103
The FortiAuthenticator (FAC) integrates with Active Directory (AD) on the Windows Domain Controller, which is also acting as the EMS server. Users are synchronized from the AD to the FAC, and remote users are configured with token-based authentication. SAML authentication is configured on the FortiGate, pointing to the FAC as the SAML IdP. The SAML server is applied to the ZTNA access proxy authentication scheme and rule, to provide the foundation for applying user authentication on individual ZTNA rules.
Configuring the FortiAuthenticator
First configure the FortiAuthenticator to synchronize users from AD using LDAP, apply MFA to individual remote users, and be the IdP.
To create a remote authentication server pointing to the Windows AD:
-
Go to Authentication > Remote Auth. Servers > LDAP and click Create New.
-
Configure the following:
Name
AD
Primary server name / IP
10.100.88.5
Port
389 (or another port if using LDAPS)
Based distinguished name
DC=FORTI-ARBUTUS,DC=LOCAL
Bind type
Regular
Username
<user account used for LDAP bind>
Password
<password of user>
User object class
person (default)
Username attribute
sAMAccountName (default)
Group object class
group (default)
Obtain group membership from
Group attribute
Group membership attribute
memberOf (default)
Secure connection
Enable if using LDAPS or STARTTLS
-
Click OK.
-
In the Remote LDAP Users section click Go.
-
Select the users to import then click OK.
-
Click OK.
For more details, see LDAP in the FortiAuthenticator Administration Guide.
To configure a remote LDAP user to use MFA:
-
Go to Authentication > User Management > Remote Users, and edit a user.
-
Enable Token-based authentication then select the method of token code delivery.
For this example, select FortiToken > Mobile, select the Token from the drop-down list, and set the Activation delivery method to email.
-
In the User Information section, add the email address that will be used for the FortiToken activation.
-
Click OK.
An activation email is sent to the user that they can use to install the token to their FortiToken Mobile app.
For more details, see Remote users in the FortiAuthenticator Administration Guide.
To configure SAML IdP:
-
Go to Authentication > SAML IdP > General and enable Enable SAML Identity Provider portal.
-
The Server address is the device FQDN or IP address (configured in the System Information widget at System > Dashboard > Status). In this example, it is fac.fortidemo.fortinet.com.
-
Set Username input format to username@realm.
-
Click Add a realm in the Realms table:
-
Set Realm to the just created LDAP realm (AD).
-
Optionally, enable Filter and select the required users groups. In this example, Customer Support and Marketing are configured.
-
-
Set Default IdP certificate to the certificate that will be used in the HTTPS connection to the IdP portal.
-
Click OK.
-
Go to Authentication > SAML IdP > Service Providers, and click Create New to create a service provider (SP) for the FortiGate SP.
-
Configure the following, which must match what will be configured on the FortiGate:
SP name
Enterprise Core
IdP prefix
ztna
Server certificate
Same certificate as the default IdP certificate used in SAML IdP > General
SP entity ID
https://entcore.fortidemo.fortinet.com:20443/ztna/saml/metadata/
SP ACS (login) URL
https://entcore.fortidemo.fortinet.com:20443/ztna/saml/login/
SP SLS (logout) URL
https://entcore.fortidemo.fortinet.com:20443/ztna/saml/logout/
Participate in single logout
Enable
Where the SP entity ID, SP ACS (login) URL, and SP SLS (logout) URL break down as follows:
-
entcore.fortidemo.fortinet.com - The FQDN that resolves to the FortiGate SP.
-
20443 - The port that is used to map to the FortiGate's SAML SP service.
-
/ztna/saml - The custom, user defined fields.
-
/metadata, /login, and /logout - The standard convention used to identify the SP entity, log in portal, and log out portal.
-
-
Click OK.
-
Edit the just created SP object and, under SAML Attribute, click Create New.
-
Set SAML attribute to the username and set User attribute to Username, then click OK.
-
Click OK.
Configuring the FortiGate SAML settings
On the FortiGate, a SAML user is used to define the SAML SP and IdP settings. This user is then applied to the ZTNA proxy using an authentication scheme, rule, and settings. A ZTNA server is then created to allow access to the SAML SP server so that end users can reach the FortiGate SP's captive portal. The SAML user must then be added to a ZTNA rule to trigger authentication when accessing the ZTNA access proxy.
To create a new SAML user/server:
-
Create the SAML user object:
config user saml edit "su-ztna" set cert "FortiDemo" set entity-id "https://entcore.fortidemo.fortinet.com:20443/ztna/saml/metadata/" set single-sign-on-url "https://entcore.fortidemo.fortinet.com:20443/ztna/saml/login/" set single-logout-url "https://entcore.fortidemo.fortinet.com:20443/ztna/saml/logout/" set idp-entity-id "http://fac.fortidemo.fortinet.com/saml-idp/ztna/metadata/" set idp-single-sign-on-url "https://fac.fortidemo.fortinet.com/saml-idp/ztna/login/" set idp-single-logout-url "https://fac.fortidemo.fortinet.com/saml-idp/ztna/logout/" set idp-cert "REMOTE_Cert_1" set user-name "username" set digest-method sha1 next endWhere:
-
The
FortiDemocertificate is a local certificate that is used to sign SAML messages that are exchanged between the client and the FortiGate SP. In this example, it is used to sign entcore.fortidemo.fortinet.com. -
The
REMOTE_Cert_1certificate is a remote certificate that is used to identify the IdP. In this example, fac.fortidemo.fortinet.com. -
The URLs used in the SAML user settings are the same as the ones defined on the FortiAuthenticator.
-
-
Add the SAML user object to a new user group:
config user group edit "ztna-users" set member "su-ztna" next end
To apply the SAML server to proxy authentication:
-
Apply the SAML server to an authentication scheme:
config authentication scheme edit "saml-scheme" set method saml set saml-server "su-ztna" next end -
Apply the authentication scheme to an authentication rule:
config authentication rule edit "saml-rule" set srcintf "any" set srcaddr "all" set ip-based disable set active-auth-method "saml-scheme" set web-auth-cookie enable next end -
Configure the active authentication scheme, and a captive portal to serve the log in page for the SAML requests:
config firewall address edit "entcore.fortidemo.fortinet.com" set type fqdn set fqdn "entcore.fortidemo.fortinet.com" next endconfig authentication setting set active-auth-scheme "saml-scheme" set captive-portal "entcore.fortidemo.fortinet.com" end
To configure a ZTNA access proxy to allow SAML authentication requests to the SP:
-
Configure the ZTNA server:
-
Go to Policy & Objects > ZTNA, select the ZTNA Servers tab, and click Create New.
-
Configure the following:
Name
ZTNA-access
External interface
Any
External IP
10.100.64.201
External port
20443
SAML
Enabled
SAML SSO Server
su-ztna
Default certificate
FortiDemo
-
Click OK.
-
-
Define the ZTNA rule to allow access to the ZTNA server:
-
Go to Policy & Objects > ZTNA, select the ZTNA Rules tab, and click Create New.
-
Configure the following:
Name
ZTNA-Rule
Source (Address)
all
Source (User)
ztna-users
ZTNA Server
ZTNA-access
Action
Accept
-
Click OK.
-
To configure a VIP and a firewall policy to forward IdP authentication traffic to the FortiAuthenticator:
Remote clients connect to the FortiAuthenticator IdP behind the FortiGate using a VIP. In this example, users connect to the FQDN fac.fortidemo.fortinet.com that resolves to the VIP's external IP address.
-
Configure the VIP to forward traffic to the FortiAuthenticator:
-
Go to Policy & Objects > Virtual IPs and click Create New > Virtual IP.
-
Configure the following:
Name
FortiAuthenticator
Interface
Any
External IP address
10.100.64.103
Map to > IPv4 address/range
10.100.88.9
Port Forwarding
Enabled
Protocol
TCP
External service port
443
Map to IPv4 port
443
-
Click OK.
-
-
Configure a firewall policy to allow VIP:
-
Go to Policy & Objects > Firewall Policy and click Create New.
-
Configure the following:
Name
WAN to FAC
ZTNA
Disabled
Incoming Interface
Any
Outgoing Interface
Any
Source
All
ZTNA Server
FortiAuthenticator
Schedule
always
Service
ALL
Action
Accept
NAT
disabled
-
Click OK.
-
Example 1 - Applying SAML and MFA to ZTNA HTTPS access proxy
In this HTTPS access proxy example, two real servers are implemented with round robin load balancing performed between them. The HTTPS access proxy is configured on the same ZTNA server as was configured in the authentication step. The same ZTNA rule and firewall policy also apply.
To configure the ZTNA server for HTTPS access proxy with load balancing:
-
Go to Policy & Objects > ZTNA and select the ZTNA Servers tab.
-
Edit the ZTNA-access server.
-
In the Service/server mapping table, click Create New:
-
Set Service to HTTPS.
-
Set Virtual Host to Any Host.
-
In the Servers table click Create New:
-
Set IP to 10.100.77.200
-
Set Port to 443.
-
Set Status to Active.
-
Click OK.
-
-
Create a second server with IP 10.100.77.202.
-
Click OK.
-
-
Enable Load balancing, and select the Round Robin algorithm.
-
Click OK.
Testing and verification:
From the remote endpoint, user John Locus attempts to connect to the Finance server over ZTNA:
-
On the remote Windows computer, open FortiClient and register to the EMS server.
-
Open a browser and attempt to connect to the web server at https://ztna.fortidemo.fortinet.com:20443.
-
Device authentication prompts the user for their device certificate. Select the certificate issued by EMS and click OK.
-
FortiGate receives the SAML request and redirects the user to the IdP login screen. Enter the username and password for John Locus and click Login.
-
A second prompt opens asking for the Token Code. Enter the code then click Verify.

-
The FortiAuthenticator IdP verifies the login, then sends the SAML assertion back to the user.
-
The browser redirects the assertion to the FortiGate SP, which decides if the user is allowed access.
-
On a successful log in, FortiGate redirects the user to the web page that they are trying to access.
Logs and debugs:
On the FortiGate, a successful connection can be seen in Log & Report > Forward Traffic log, or by using the CLI:
# execute log filter category 0 # execute log filter field srcip 10.100.66.103 # execute log display ... 1: date=2021-08-25 time=23:34:15 eventtime=1629959656098675227 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=51341 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.77.202 dstport=443 dstintf="root" dstintfrole="undefined" sessionid=3396047 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="HTTPS" proto=6 action="accept" policyid=1 policytype="proxy-policy" poluuid="256bb090-0518-51ec-f431-5dcc0baa725b" policyname="ZTNA-Rule" duration=16 user="johnlocus" group="ztna-users" wanin=2837 rcvdbyte=2837 wanout=1495 lanin=2581 sentbyte=2581 lanout=5505 appcat="unscanned" 2: date=2021-08-25 time=23:34:04 eventtime=1629959645171823879 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=62691 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.77.200 dstport=443 dstintf="root" dstintfrole="undefined" sessionid=3396036 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="HTTPS" proto=6 action="accept" policyid=1 policytype="proxy-policy" poluuid="256bb090-0518-51ec-f431-5dcc0baa725b" policyname="ZTNA-Rule" duration=5 user="johnlocus" group="ztna-users" wanin=2837 rcvdbyte=2837 wanout=1546 lanin=1576 sentbyte=1576 lanout=1033 appcat="unscanned" ... 4: date=2021-08-25 time=23:29:21 eventtime=1629959362319670887 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=62107 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.64.201 dstport=20443 dstintf="root" dstintfrole="undefined" sessionid=3388350 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="tcp/20443" proto=6 action="accept" policyid=41 policytype="policy" poluuid="256d6bd8-0518-51ec-7b6a-18df00b82da3" policyname="ZTNA Policy" duration=1 user="johnlocus" authserver="su-ztna" wanin=0 rcvdbyte=0 wanout=0 lanin=14246 sentbyte=14246 lanout=993 appcat="unscanned"
Log number four shows that the session was first allowed through the ZTNA firewall policy. Log numbers one and two show the traffic allowed through the ZTNA proxy-policy over two successive sessions. Note that they have different destination IP addresses (dstip), indicating that ZTNA was performing server load balancing.
Use the following command to show if the FortiGate's WAD process has an active record of the SAML user login:
# diagnose wad user list
ID: 6, VDOM: root, IPv4: 10.100.66.103
user name : johnlocus
worker : 0
duration : 611
auth_type : Session
auth_method : SAML
pol_id : 1
g_id : 3
user_based : 0
expire : 283
LAN:
bytes_in=38016 bytes_out=16166
WAN:
bytes_in=12422 bytes_out=7217
Example 2 - Applying SAML and MFA to a ZTNA TCP forwarding access proxy for RDP connections
In this TCP forwarding access proxy example, RDP connections are allowed to be forwarded to the Windows/EMS server. Traffic to TCP/3389 is allowed through the ZTNA proxy.
To configure the ZTNA server for TCP forwarding on TCP/3389:
-
Create a firewall address for the Windows/EMS server:
-
Go to Policy & Objects > Addresses and click Create New > Address.
-
Configure the following:
Name
EMS-Server
Type
Subnet
IP/Netmask
10.100.88.5/32
Interface
any
-
Click OK.
-
-
Go to Policy & Objects > ZTNA and select the ZTNA Servers tab.
-
Edit the ZTNA-access server.
-
In the Service/server mapping table, click Create New:
-
Set Service to TCP Forwarding.
-
In the Servers table click Create New:
-
Set Address to EMS-Server.
-
Set Ports to 3389.
-
Click OK.
-
-
Click OK.
-
-
Click OK.
Testing and verification:
On the remote endpoint, manually configure ZTNA connection rules to forward RDP traffic to the ZTNA access proxy. The rules can also be pushed from the EMS server; for details see Provisioning ZTNA TCP forwarding rules via EMS.
Configure the ZTNA connection rule:
-
On the remote Windows computer, open FortiClient.
-
Register to the EMS server.
-
On the ZTNA Connection Rules tab, click Add Rule to add a TCP forwarding rule.
-
Configure the following:
Rule Name
RDP-server
Destination Host
10.100.88.5:3389
Proxy Gateway
ztna.fortidemo.fortinet.com:20443
Mode
Transparent
Encryption
Disabled
Encryption can be enabled or disabled. When it is disabled, the client to access proxy connection is not encrypted in HTTPS. Because RDP is encrypted by default, disabling Encryption does not reduce security.
-
Click Create.
Connect over RDP:
-
On the remote PC, open a new RDP connection.
-
Enter the IP address 10.100.588.5. By default, RDP session use port 3389.
When the connection to the ZTNA access proxy is established, FortiGate will redirect the SAML login request to the FortiAuthenticator IdP.
A FortiClient prompt will open with the FortiAuthenticator login screen.
-
Enter the username and password then click Login.
-
A second prompt opens asking for the Token Code. Enter the code from your FortiToken app, then click Verify.
-
FortiAuthenticator verifies the token code, determines if the login is successful, then sends the SAML assertion back to the client.
-
The client redirects the response back to the FortiGate SP.
-
If the log in was successful, the user can now log on to the RDP session.
Logs and debugs:
On the FortiGate, a successful connection can be seen in Log & Report > Forward Traffic log, or by using the CLI:
# execute log filter category 0 # execute log filter field srcip 10.100.66.103 # execute log display ... 3: date=2021-08-25 time=23:05:52 eventtime=1629957952722272222 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=59980 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.88.5 dstport=3389 dstintf="root" dstintfrole="undefined" sessionid=3349083 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="RDP" proto=6 action="accept" policyid=1 policytype="proxy-policy" poluuid="256bb090-0518-51ec-f431-5dcc0baa725b" policyname="ZTNA-Rule" duration=8 user="johnlocus" group="ztna-users" wanin=0 rcvdbyte=0 wanout=0 lanin=1444 sentbyte=1444 lanout=665 appcat="unscanned" 4: date=2021-08-25 time=23:05:49 eventtime=1629957949064583213 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=59982 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.64.201 dstport=20443 dstintf="root" dstintfrole="undefined" sessionid=3349102 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="tcp/20443" proto=6 action="accept" policyid=41 policytype="policy" poluuid="256d6bd8-0518-51ec-7b6a-18df00b82da3" policyname="ZTNA Policy" duration=5 user="johnlocus" authserver="su-ztna" wanin=0 rcvdbyte=0 wanout=0 lanin=14237 sentbyte=14237 lanout=1032 appcat="unscanned"
Use the following command to show if the FortiGate's WAD process has an active record of the SAML user login:
# diagnose wad user list
ID: 6, VDOM: root, IPv4: 10.100.66.103
user name : johnlocus
worker : 0
duration : 611
auth_type : Session
auth_method : SAML
pol_id : 1
g_id : 3
user_based : 0
expire : no
LAN:
bytes_in=51471 bytes_out=233862
WAN:
bytes_in=211247 bytes_out=24410
Example 3 - Applying SAML and MFA to a ZTNA SSH access proxy
In this SSH access proxy example, SSH connections can be forwarded to the web server.
To configure the ZTNA server for SSH access proxy:
-
Create a firewall address for the web server:
-
Go to Policy & Objects > Addresses and click Create New > Address.
-
Configure the following:
Name
Web-Server1
Type
Subnet
IP/Netmask
10.100.77.101/32
Interface
any
-
Click OK.
-
-
Go to Policy & Objects > ZTNA and select the ZTNA Servers tab.
-
Edit the ZTNA-access server.
-
In the Service/server mapping table, edit the TCP Forwarding entry:
-
In the Servers table click Create New:
-
Set Address to Web-Server1.
-
Set Ports to 22.
-
Optionally, enable Additional SSH Options to configure other SSH options as needed.
-
Click OK.
-
-
Click OK.
-
-
Click OK.
Testing and verification:
On the remote endpoint, manually configure ZTNA connection rules to forward SSH traffic to the ZTNA access proxy. The rules can also be pushed from the EMS server; for details see Provisioning ZTNA TCP forwarding rules via EMS.
Configure the ZTNA connection rule:
-
On the remote Windows computer, open FortiClient.
-
Register to the EMS server.
-
On the ZTNA Connection Rules tab, click Add Rule to add a TCP forwarding rule.
-
Configure the following:
Rule Name
SSH-webserver
Destination Host
10.100.77.101:22
Proxy Gateway
ztna.fortidemo.fortinet.com:20443
Mode
Transparent
Encryption
Disabled
-
Click Create.
Connect over SSH:
-
On the remote PC, open a new SSH connection.
-
Enter the host root@10.100.77.101 on port 22.
When the connection to the ZTNA access proxy is established, FortiGate will redirect the SAML login request to the FortiAuthenticator IdP.
A FortiClient prompt will open with the FortiAuthenticator login screen.
-
Enter the username and password then click Login.
-
A second prompt opens asking for the Token Code. Enter the code from your FortiToken app, then click Verify.
-
FortiAuthenticator verifies the token code, determines if the login is successful, then sends the SAML assertion back to the client.
-
The client redirects the response back to the FortiGate SP.
-
If the log in was successful, the user can now log on to the SSH session.
Logs and debugs:
On the FortiGate, a successful connection can be seen in Log & Report > Forward Traffic log, or by using the CLI:
# execute log filter category 0 # execute log filter field srcip 10.100.66.103 # execute log display ... 2: date=2021-08-25 time=23:20:03 eventtime=1629958804111962686 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=60043 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.77.101 dstport=22 dstintf="root" dstintfrole="undefined" sessionid=3372964 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="SSH" proto=6 action="accept" policyid=1 policytype="proxy-policy" poluuid="256bb090-0518-51ec-f431-5dcc0baa725b" policyname="ZTNA-Rule" duration=1 user="johnlocus" group="ztna-users" wanin=39 rcvdbyte=39 wanout=0 lanin=1444 sentbyte=1444 lanout=726 appcat="unscanned" 3: date=2021-08-25 time=23:20:03 eventtime=1629958803100280597 tz="-0700" logid="0000000024" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.66.103 srcport=60042 srcintf="port1" srcintfrole="wan" dstcountry="Reserved" srccountry="Reserved" dstip=10.100.64.201 dstport=20443 dstintf="root" dstintfrole="undefined" sessionid=3372934 srcuuid="d8dd134a-0517-51ec-2ff0-3032b84564e7" service="tcp/20443" proto=6 action="accept" policyid=41 policytype="policy" poluuid="256d6bd8-0518-51ec-7b6a-18df00b82da3" policyname="ZTNA Policy" duration=0 user="johnlocus" authserver="su-ztna" wanin=0 rcvdbyte=0 wanout=0 lanin=14237 sentbyte=14237 lanout=1032 appcat="unscanned"
Use the following command to show if the FortiGate's WAD process has an active record of the SAML user login:
# diagnose wad user list
ID: 6, VDOM: root, IPv4: 10.100.66.103
user name : johnlocus
worker : 0
duration : 192
auth_type : Session
auth_method : SAML
pol_id : 1
g_id : 3
user_based : 0
expire : 475
LAN:
bytes_in=19647 bytes_out=10063
WAN:
bytes_in=2886 bytes_out=1860

