Uses cases and topologies
Fortinet Secure SD-Branch can be defined as a natural extension of an existing Fortinet Secure SD-WAN architecture. As such, this guide will not provide details about SD-WAN configuration. For details about SD-WAN configuration, see the following guides:
Instead this guide will focus on the implementation of remote branches that leverage wireless and wired LAN by using FortiGate as a distributed controller and by using FortiManager/FortiAnalyzer as central management / reporting platforms. Because this guide does not provide details about some parts of the configuration related to routing, overlay, and SD-WAN, it is strongly recommended to read the SD-WAN Deployment for MSSPs document before reading this guide.
This guide aims to deliver best practice guidelines for deploying a Fortinet Secure SD-Branch architecture that is optimized for ZTP of an entire branch, including wired, wireless, and LTE connectivity. One key requirement of such a deployment is the capability to minimize the number of manual operations while still providing a high degree of flexibility.
The reference topology used in this deployment guide uses the following devices:
- FortiGates
Three FortiGates are used. One FortiGate is used at the headquarter (HQ) office, and the other two FortiGates represent the two branch offices named EDGE1 and EDGE2.
- FortiSwitch
- FortiAP
- FortiExtender
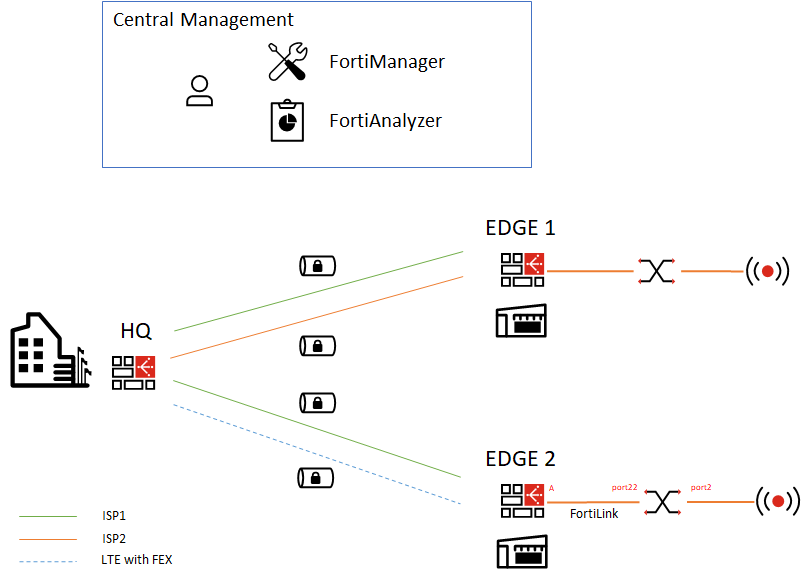
On the HQ and EDGE1 FortiGates, we connected two internet links. On EDGE2, a single internet link is enabled, and we will later add 4G connectivity with a FortiExtender.
|
|
The FortiExtender is an appliance that provides enterprise-class LTE/5G connectivity and can easily be integrated as an extension of the SD-WAN fabric. FortiExtender can be used as a standalone router, or FortiExtender can be managed by FortiGate or FortiCloud. In standalone mode, the FortiExtender must be configured directly from its management interface (GUI or CLI), which may not be ideal for mass deployments. You can also use FortiCloud, which is a SaaS platform that provides fleet management for FortiExtender. However, for the ZTP use case, it is best to use the FortiGate managed mode to have a single management platform for our SD-Branch approach. |
Two IPsec overlays are configured on the HQ and on EDGE1, and BGP is used to exchange routes. We will configure EDGE2 to build two IPsec overlays on top of ISP1 and a 4G link with the FortiExtender.
|
|
The FortiManager is reachable through the Hub and will be used to deploy, manage and monitor all the devices. |
Users and devices can then connect to the SD-WAN architecture by using either wired or wireless LAN access.
For wired LAN access, FortiSwitches are available in a variety of models to address needs from the access layer to the datacenter. All models can be managed and configured directly from FortiGate.
For wireless LAN access, FortiAPs are available in a variety of models, from 2x2 to 4x4 or with an internal or external antenna, to address specific use cases and price points.

