FortiLink Network Sniffer Extension
In 6.0, the switch controller introduced traffic mirroring with a single switch. This provides a general capability, but can result in large volumes of traffic being mirrored. In 6.2, the new switch controller option of traffic-sniffer provides a targeted approach: mirrored traffic is always directed towards the FortiGate on a dedicated VLAN. This allows for easy sniffing by using the CLI or GUI. Additionally, the traffic can also be routed through the FortiGate using Encapsulated Remote Switched Port Analyzer (ERSPAN) for external analysis and storage.
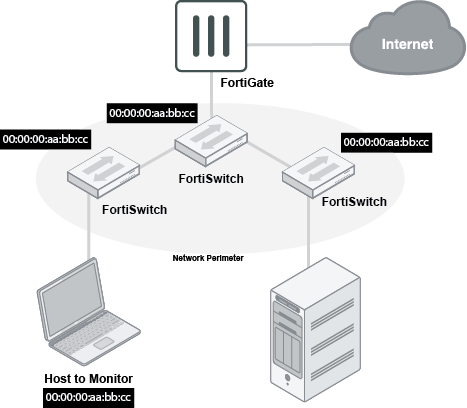
With the new option, you can define targeted sniffers by IP or MAC address. Traffic matching is replicated to the FortiGate, which is helpful when you know what device you are looking for, but you don't know where it is located.
FortiLink networks can have multiple switches, and traffic typically traverses several switches. If each switch mirrors any match, the sniffer would see multiple copies of traffic. To reduce this, the targets are applied at the perimeter of the FortiSwitch network. Traffic entering by a user port or traffic from FortiGate is considered eligible for mirroring.
You can also enable traditional port-based sniffers in the ingress or egress direction.
All sniffer traffic arrives at the FortiGate using ERSPAN and the traffic is encapsulated in generic routing encapsulation (GRE).
You can only configure this feature using the CLI:
- Use pre-defined sniffer-used switch VLAN interface:
config system interface
edit "snf.aggr1" ---> Newly added pre-defined switch vlan interface. Created automatically after the first FortiSwitch is discovered and authorized.
set vdom "root"
set ip 10.254.253.254 255.255.254.0
set allowaccess ping
set description "Sniffer VLAN"
set snmp-index 33
set switch-controller-traffic-policy "sniffer"
set color 6
set interface "aggr1"
set vlanid 4092
next
end
- Enable traffic sniffer based on target IP or MAC addresses on target ports of managed FortiSwitch units:
config switch-controller traffic-sniffer ---> newly added>
set erspan-ip 2.2.2.2 ---> Designated ERSPAN collector
config target-mac
edit 11:11:11:11:11:11
next
end
config target-ip
edit 4.4.4.4
next
end
config target-port
edit "S524DN4K1500XXXX"
set in-ports "port2" "port4" "port6"
set out-ports "port3" "port5" "port7"
next
end
end
- Use troubleshooting tools:
FortiGate-500E (root) # diag switch-controller switch-info mirror status S524DN4K1500XXXX
Managed Switch : S524DN4K1500XXXX
flink.sniffer
Mode : ERSPAN-auto
Status : Active
Source-Ports:
Ingress: port2, port4, port6
Egress : port3, port5, port7
Used-by-ACLs : True
Auto-config-state : Resolved/Running
Last-update : 1464 seconds ago
Issues : None
Collector-IP : 2.2.2.2
Source-IP : 10.254.252.208
Source-MAC : 08:5b:0e:ff:40:27
Next-Hop :
IP : 10.254.253.254
MAC : 00:09:0f:09:00:0c
Via-System-Interface : sniffer
VLAN : 4092(tagged)
Via-Switch-Interface : G5H0E391790XXXX

