Installing Accounting and Marketing
- To edit wan1 on Accounting, go to Network > Interfaces.
- Set an IP/Network Mask for the interface that is on the same subnet as port 10 on Edge (in the example, 192.168.10.10/255.255.255.0).
-
Under Administrative Access, select HTTPS and SSH to allow Edge to use this interface to manage the FortiGate.

-
Edit the lan interface.
-
Set Addressing mode to Manual and set the IP/Network Mask to a private IP address (in the example, 10.10.10.1/255.255.255.0).
- Set Administrative Access to allow FortiTelemetry.
-
If you require the FortiGate to provide IP addresses using DHCP to devices that connect to this interface, enable DHCP Server.
-
Under Networked Devices, enable Device Detection.

It's a best practice to enable Device Detection on all interfaces classified as LAN or DMZ.

-
To add a static route, go to Network > Static Routes. Set Gateway to the IP address of port 10 on Edge.

-
To create a policy to allow users on the Accounting network to access Edge, go to Policy & Objects > IPv4 Policy.

-
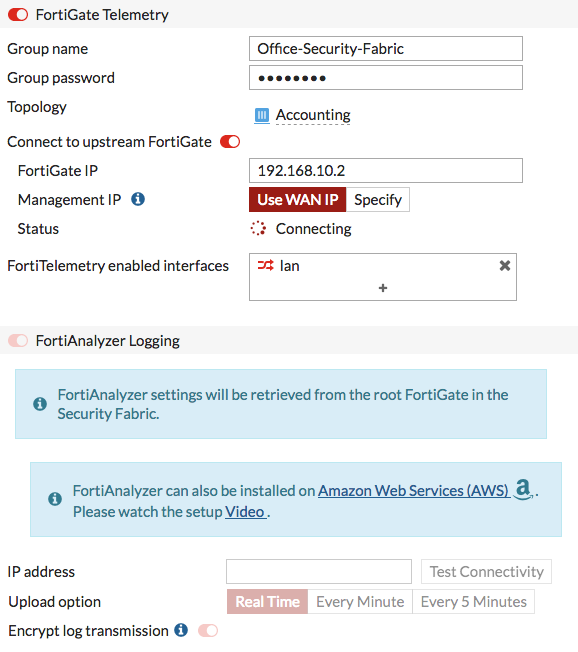
To add Accounting to the Security Fabric, go to Security Fabric > Settings. Enable FortiGate Telemetry, then enter the same Group name and Group password that you set previously on Edge (the Group password option isn’t available isn’t available in FortiOS 6.0.3 and later).
-
Enable Connect to upstream FortiGate and enter the IP address of port 10 on Edge.
-
FortiAnalyzer Logging is enabled by default. Settings for the FortiAnalyzer are retrieved when Accounting connects to Edge.
-
Connect WAN 1 on Accounting to port 10 on Edge.
-
Connect and configure Marketing, using the same method that you used to configure Accounting. Make sure you complete the following steps:
-
Configure WAN 1 to connect to Edge (IP address: 192.168.200.10/255.255.255.0) and allow HTTPS and SSH access.
-
Configure the LAN interface for the Marketing network (IP address: 10.10.200.2/255.255.255.0).
-
Create a static route pointing traffic to port 11 on Edge.
-
Create a policy to allow users on the Marketing network to access Edge.
-
Add Marketing to the Security Fabric.
-
-
If you’re using FortiOS 6.0.3 and later, connect to Edge and go to Security Fabric > Settings. Authorize both Accounting and Marketing to join the Security Fabric.