SSL VPN for users with passwords that expire
In this recipe, you will learn how to configure an SSL VPN portal for users with passwords that expire after two days. Users will be warned after one day about the password expiring and will have one day to renew it.
If the users also have access to an IPsec VPN, the expiration time applies to that tunnel’s access as well, since the passwords expire and not the tunnel itself.
The example uses local users but the password policy can be applied to any user. The password policy cannot be applied to a user group.
This recipe involves some minor configuration in the CLI Console.

1. Creating the SSL VPN user and user group
- Go to User & Device > User Definition > Create New and create a new user via the Users/Groups Creation wizard.
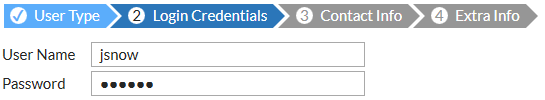
- Enter a User Name and Password.
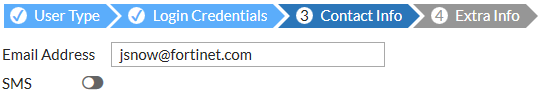
- Enter contact information via Email Address. SMS information should be provided if required.
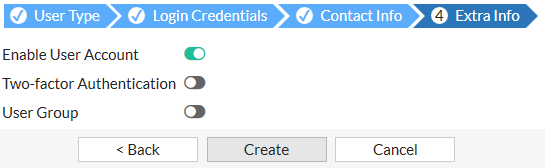
- Enable the user account and apply Two-factor Authentication if required.
- Click Create.
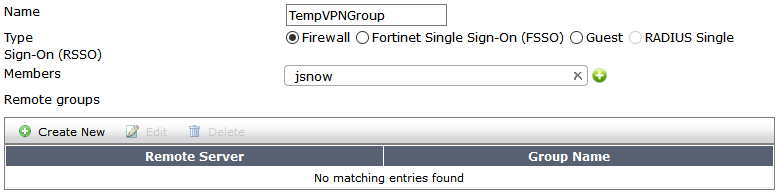
- Go to User & Device > User Groups and create a user group that includes the newly created user.
2. Configuring and assigning the password policy
- Enter the CLI Console and configure a password policy using the following commands:
config user password-policy edit "pwpolicy1" set expire-days 2 set warn-days 1 next endThe password policy includes an expiration time and a warning time.
- Assign the password policy to the newly created user using the following commands.
config user local edit "jsnow" set type password set passwd-policy "pwpolicy1" next endBy default, the start time for the password is set to the time the user was created.
3. Configuring the SSL VPN web portal and settings
- Go to VPN > SSL-VPN Portals and select full-access.
- Disable Enable Split Tunneling. and select the Source IP Pools. In the example, the default SSLVPN_TUNNEL_ADDR1 pool will suffice.
- Enable Tunnel Mode Client Options as required, ensure that you Enable Web Mode and click OK.

- Go to VPN > SSL-VPN Settings.
- Under Connection Settings, set Listen on Interface(s) to the Internet-facing interface and set Listen on Port to 10443. This will avoid an administrative HTTPS port conflict. You can also change the administration HTTPS port in System > Settings.

- Under Tunnel Mode Client Settings, set Address Range to Automatically assign addresses. You can Specify custom IP ranges.
- Under Authentication/Portal Mapping, assign the newly created user group (“TempVPNGroup“) to the full-access portal and Apply your changes.

4. Adding security policies for access to the internal network and the Internet
- Go to Policy & Objects > IPv4 Policy and add a security policy allowing access to the internal network through the VPN tunnel interface.
- Include the newly created user group and enable NAT.
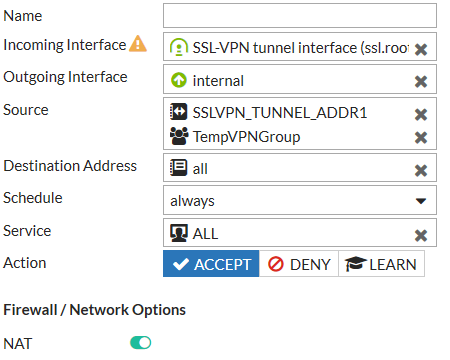
- Add a second security policy allowing access to the Internet through the VPN tunnel interface.
- Include the newly created user group an enable NAT.

5. Results
When jsnow browses to the SSL VPN web portal, they are prompted to enter their username and password.

When the warning time is reached (see 2. Configuring and assigning the password policy), the user is prompted to enter a new password. There is no warning that the user will expire for IPsec VPN, as there is no protocol for that in IPsec Xauth.
However, when the expiration time is reached, the user will not be able to enter a new password and must contact the administrator for assistance.

Go to Log & Report > VPN Events to see the SSL VPN alert labeled ssl-alert.
Highlight the alert message and click Details to see the log in greater detail, specifically under Action.


