Organization restrictions
FortiGate-VM on GCP supports the organization restrictions feature. This guide is a walkthrough of how to configure FortiGate as a proxy and create the header insertion to use this GCP feature.
This guide assumes that your GCP environment has existing networks and resources.
The following provides an overview of using this feature with FortiGate-VM:
-
Customer GCP organization ID is required. For information about finding your organization ID from a project ID, see gcloud projects get-ancestors.
-
You must set the FortiGate public IP address as the proxy server on the client web browser.
-
The FortiGate-VM on GCP (proxy and header insertion) receives and processes the HTTP request.
-
The FortiGate proxy firewall policy allows or denies GCP resource access based on header X-Goog-Allowed-Resources content of your organization ID in Base64 encoding.
For information about GCP organization restriction, see Introduction to organization restrictions.
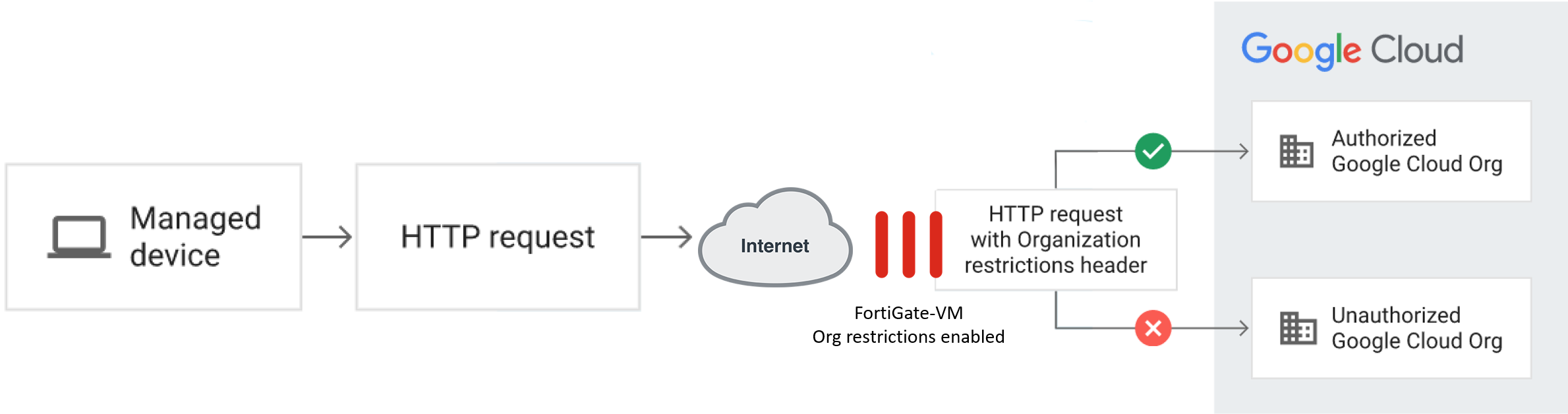
To configure the FortiGate-VM with organization restrictions:
- On the FortiGate, enable web proxy:
- Go to Network > Explicit Proxy.
- Enable Explicit Web Proxy.
- Configure the proxy HTTP and HTTPS ports as desired. This example sets them to 8080.

- Create address objects specifying allowed GCP endpoints. You will use the address objects in the web proxy profile header and the proxy policy configuration:
config firewall address
edit allow_gcp_api_addr_obj
set type fqdn
set fqdn *.googleapis.com
next
end
config firewall address
edit allow_gcp_com_addr_obj
set type fqdn
set fqdn *.google.com
next
end
config firewall address
edit allow_gstatic_addr_obj
set type fqdn
set fqdn www.gstatic.com
next
end

You may need more address objects for other Google services. You must add these address objects to the proxy header configuration and the proxy policy as destination addresses:
- *.gcr.io
- *.pkg.dev
- *.cloudfunctions.net
- *.run.app
- *.tunnel.cloudproxy.app
- *.datafusion.googleusercontent.com
- Configure the web proxy profile:
config web-proxy profile
edit gcp-org-restrict-profile
config headers
edit 1
set name X-Goog-Allowed-Resources
set dstaddr allow_gcp_api_addr_obj allow_gcp_com_addr_obj allow_gstatic_addr_obj
set action add-to-request
set content "{"resources": ["organizations/<Customer Org ID>"],"options": "strict"}"
set base64-encoding enable
set add-option new
set protocol http https
end
end
- Configure the proxy policy:

This is an example policy. Do not use it in a production environment.
config firewall proxy-policy edit 1 set name "gcp_restriction_policy" set proxy explicit-web set dstintf "port1" set srcaddr "all" set dstaddr "allow_gcp_api_addr_obj" "allow_gcp_com_addr_obj" “allow_gstatic_addr_obj” set service "webproxy" set srcaddr-negate disable set dstaddr-negate disable set service-negate disable set action accept set status enable set schedule "always" set logtraffic utm set webproxy-forward-server '' set webproxy-profile gcp-org-restrict-profile set transparent disable set disclaimer disable set utm-status disable set profile-protocol-options "default" set ssl-ssh-profile "no-inspection" set replacemsg-override-group '' set logtraffic-start disable set comments '' next endWhile a workstation is configured to use the FortiGate as a proxy, the web browser is allowed access to resources in the organization:


The policy on the FortiGate proxy stops access to any other resources outside of the GCP organization:


