Accessing a cloud server using a Fabric connector via VPN
This guide provides a sample configuration that allows a local client PC to access an FTP server deployed inside the AWS cloud by using an AWS Fabric connector via SSL VPN.
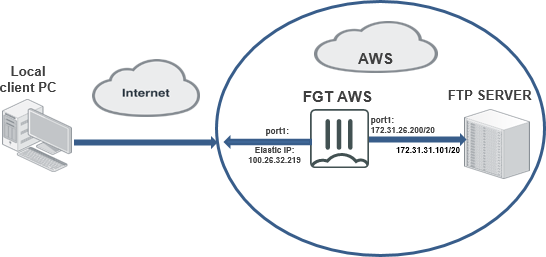
In this topology, a FortiGate-VM for AWS is deployed inside the AWS cloud. The FortiGate-VM can dynamically resolve the FTP server's private IP address in the AWS cloud through an AWS Fabric connector. A local client PC with FortiClient installed can establish an SSL VPN tunnel to the FortiGate-VM inside the AWS cloud, then access the FTP server through the SSL VPN tunnel.
To configure the FortiGate-VM:
- Configure the AWS Fabric connector:
- In FortiOS, go to Security Fabric > Fabric Connectors.
- Click Create New.
- Select Amazon Web Services (AWS).
- In the AWS region name field, enter us-east-1.
- Leave the AWS VPC ID field blank if no VPC ID is specified.
- Configure other fields as required. Click OK.
- Go toSecurity Fabric > Fabric Connectors. Click the refresh icon for the configured connector. The green arrow means that the connector is connected.

- Create a Fabric connector firewall address to associate the configured Fabric connector:
- Go to Policy & Objects > Addresses.
- Click Create New, then select Address.
- From the Type dropdown list, select Fabric Connector Address.
- From the SDN Connector dropdown list, select the connector created in step 1.
- For SDN address type, select Private.
- In the Filter field, enter Tag.Name=publicftp. This is the name of the FTP server in the AWS cloud.
- From the Interface dropdown list, select any.
- Click OK. The following shows the FTP server as seen in the AWS management console.

- After the update interval (60 seconds by default), check the resolved firewall address:
- Go to Policy & Objects > Addresses.
- Hover over the address created in step 2. In this example, it shows the firewall address (172.31.31.101) that the configured Fabric connector resolves to.

- Configure SSL VPN to access the FTP server:
- Configure the user and user group:
- Go to User & Device > User Definition.
- Create a new local user.
- Go to User & Device > User Groups.
- Create a group that includes the new local user.
- Configure SSL VPN settings:
- Go to VPN > SSL-VPN Settings.
- In the Listen on Interface field, select the proper interface. This example selects port1.
- In the Listen on Port field, enter 10443.
- From the Server Certificate dropdown list, select the desired certificate.

Self-signed certificates are provided by default to simplify initial installation and testing. It is HIGHLY recommended that you acquire a signed certificate for your installation.
Continuing to use these certificates can result in your connection being compromised, allowing attackers to steal your information, such as credit card details.
For more information, please review Use a non-factory SSL certificate for the SSL VPN portal and learn how to Purchase and import a signed SSL certificate.
- Under Authentication/Port Mapping, set the default full-access portal for All Other Users/Groups.
- Create a new authentication/portal mapping for the group created in step a, mapping to the full-access portal.
- Configure the SSL VPN firewall policy:
- Go to Policy & Objects > IPv4 Policy.
- From the Incoming Interface dropdown list, select the SSL VPN tunnel interface (ssl.root).
- From the Outgoing Interface dropdown list, select port1.
- In the Source field, select all and the group configured in step a.
- In the Destination field, select the address created in step 2.
- From the Schedule dropdown list, select always.
- In the Service field, select ALL.
- For Action, select Accept.
- Click OK.
- Configure the user and user group:
To establish an SSL VPN connection from the local client PC:
This example assumes that you are not using EMS to manage endpoints. If you are using EMS, use a licensed FortiClient endpoint for the configuration below, skipping the installation step.
- Download VPN-only FortiClient from FortiClient.com. Install onto the local client PC.
- In FortiClient, on the Remote Access tab, add a new connection.
- For VPN, select SSL-VPN.
- In the Remote Gateway field, enter the IP address of the listening FortiGate interface. In this example, it is 100.26.32.219, the FortiGate-VM port1 public IP address.
- Select Customize port, then enter 10443.
- Save the configuration.
- Use the credentials configured in step 4a above to connect to the SSL VPN tunnel. After connection, traffic to the Fabric connector resolved IP address (172.31.31.101) goes through the tunnel. Other traffic goes through the local gateway. The client PC side shows the routing entry for the SSL VPN tunnel:
Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 172.16.200.1 0.0.0.0 UG 0 0 0 eth1 172.31.31.101 10.212.134.200 255.255.255.255 UGH 0 0 0 ppp0
The FortiGate-VM shows the logged in user and the assigned SSL VPN tunnel virtual IP address.

execute vpn sslvpn list SSL VPN Login Users: Index User Auth Type Timeout From HTTP in/out HTTPS in/out 0 usera 1(1) 284 208.91.115.10 0/0 0/0 SSL VPN sessions: Index User Source IP Duration I/O Bytes Tunnel/Dest IP 0 usera 208.91.115.10 76 1883/1728 10.212.134.200
To run diagnose commands:
- To show Fabric connector status, run the
diagnose sys sdn statuscommand. The output should be as follows:SDN Connector Type Status ------------------------------------------------------------- aws1 aws connected
- To debug the AWS Fabric connector to resolve the firewall address, run the
diagnose debug application awsd -1command. The output should be as follows:... awsd checking firewall address object dynamic-aws, vd 0 address change, new ip list: 172.31.31.101 awsd sdn connector aws1 finish updating IP addresses ...
- To restart the AWS Fabric connector daemon, run the
diagnose test application awsd 99 command.

