Details pane
You can click anywhere in a row in any of the Activity Events tables to display more details about the specific activity event in a Details pane on the right. The selected row is marked by a green border on its left.

The Details pane for an activity event contains a Summary tab and one or two other tabs, as follows:

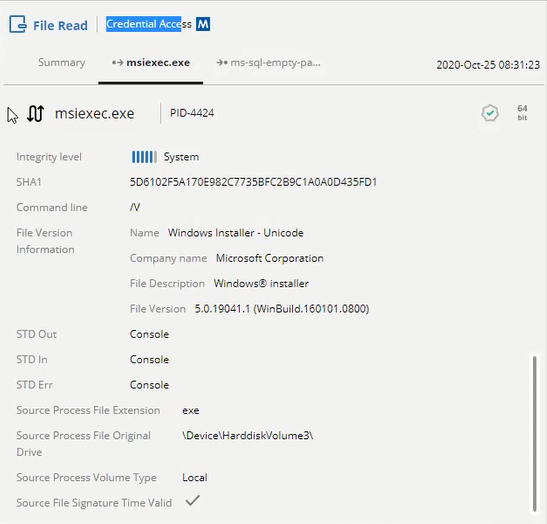
- Summary tab: This tab specifies a summary of the activity event. At the top of the tab, it shows details about the endpoint, including the endpoint and its IP, path, operating system, and so on. The area below the endpoint section shows the source process and its detail. The area below the source graphically shows the action again, which is the activity event type, as well as some additional data regarding the action, if any. The area at the bottom of the pane shows the target and its details. You can click the Expand (
 ) or Collapse (
) or Collapse ( ) arrows in an area of this pane to show or hide additional relevant details, respectively.
) arrows in an area of this pane to show or hide additional relevant details, respectively. - Process tab: This tab shows additional details about the source process.
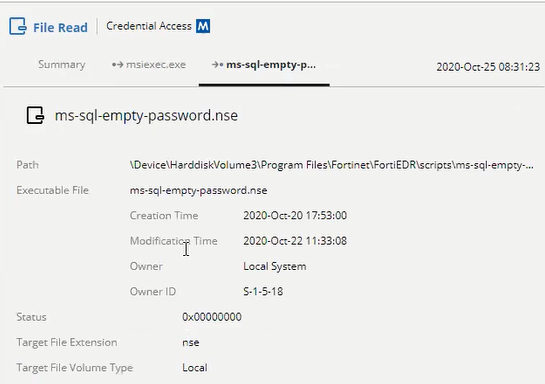
- Target tab: This tab only displays if the target is of type Process or File, and details additional data regarding such.
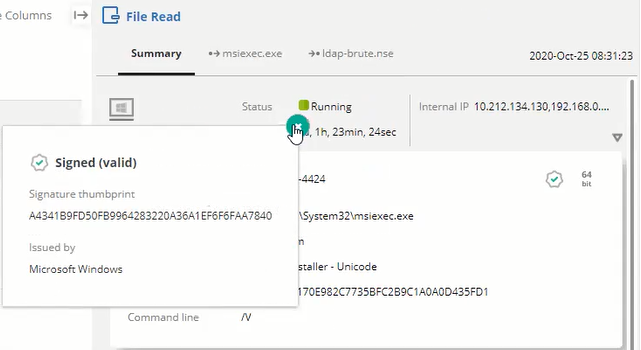
You can click an icon in the Details pane to display additional details, as shown below:
Event Log Details pane
The Details pane for an activity event of type Event Log Created appears somewhat differently, as shown below. In this case, the action is always Log Entry Created and the target is always the event ID.

You can scroll down in the Target area to view the actual log entry.

Retrieving a file / Remediating devices upon malware detection
You can remediate any file that is a target of an activity event. You can also download a copy of any file (Retrieve action) that is a target of an activity event.
To retrieve a file or remediate the process:
- Select the relevant activity event and open its Details Pane.
- When hovering over the filename, you can select either of the following options:
In the Summary pane, select the three dot dropdown menu and then select Retrieve of Remediate the file, as shown below:

– OR –
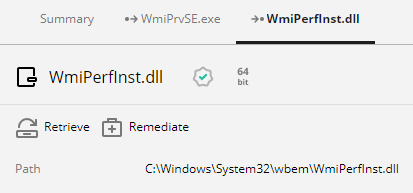
In the Details pane, click the Retrieve or Remediate button, as shown below:
Adding an application to the Application Control policy blocklist
You can add any process that is either the source or the target of an activity event to the Application Control Policy blocklist such that this process won’t launch on the devices that are assigned to that Application Control policy.
To add a process to an Application Control policy:
- Select the relevant activity event and open its Details Pane.
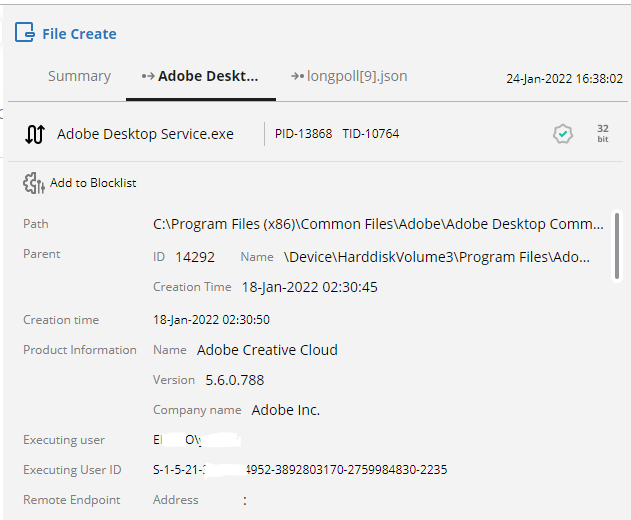
- In the Summary page, click the More (
 ) option next to the process name and select Add to Blocklist, as shown below:
) option next to the process name and select Add to Blocklist, as shown below:
OR
Go to either the Source or the Target tab of type process and click the Add to Blocklist button, as shown below:
GDPR and activity event data
The FortiEDR system fully complies with the General Data Protection Regulation (GDPR) standard, as described in Personal data handling. When you use the Personal Data Handling feature to delete data, it also deletes activity event data. However, the Personal Data Handling Search option does not search for and display the activity data that it will delete. Just for your own knowledge, in order to see a list of the activity data that will be deleted you can view it here before you delete it. To do so, simply enter a query here that includes the chosen record from the Activity Report (that can be accessed by selecting Administration >Tools > Personal Data Handling) in order to find the data to be removed. For example, if you have provided the string 149 in Personal Data Handling for Search by Device name, then in the displayed Activity Report, select the record containing the device name to be deleted. In this example, it is US-Dev149. Then, in order to display all the activity events that are related to this device, enter the query Device.Name: US-Dev149, as shown below in order to display the relevant records.

To find all activity related to a user chosen from a Personal Data Handling Activity Report, enter the following query, and select the required time range:
"Source.File.Owner:<username> OR Source.User:<username> OR Process.File.Owner:<username> OR Process.User:<username> OR Target.File.Owner:<username>"
Similarly, to find all activity related to an IP chosen from a Personal Data Handling Activity Report, enter the following query:
"Device.IPInternal:<IP> OR LocalIP:< IP > OR RemoteIP:< IP > OR Target.Network.AdditionalData.RemoteIp:<IP>"

