Deception for FortiGuard Outbreak Alerts
FortiGuard Outbreak Alerts communicate important information about cybersecurity attacks and the Fortinet products that will break the attack sequence. When a cybersecurity incident/attack/event occurs that affects numerous organizations, the Outbreak Alerts page is updated with a link to an individual FortiGuard Outbreak Alert. For more information, visit the Outbreak Alerts page.
FortiDeceptor's outbreakv1 Deception OS contains Deception Decoys that are designed to target and mitigate vulnerabilities identified in the FortiGuard Outbreak Alerts page.
The following steps describe how to configure the outbreakv1 Deception OS for Log4j2 attacks.
To deploy deception decoys for Outbreak Alerts:
- Install the outbreakv1 deception OS.
- Go to Deception > Deception OS.
- In the Status column, click Synchronize next to outbreakv1. The status changes to Initialized.

- Go to Deception > Deployment Wizard and click Create a new decoy. The Configuration page opens.
- Configure the following deployment settings.
Available Deception OSes Select outbreakv1. Available Deception Decoys Select and outbreak deception decoy. For example, Log4j2. 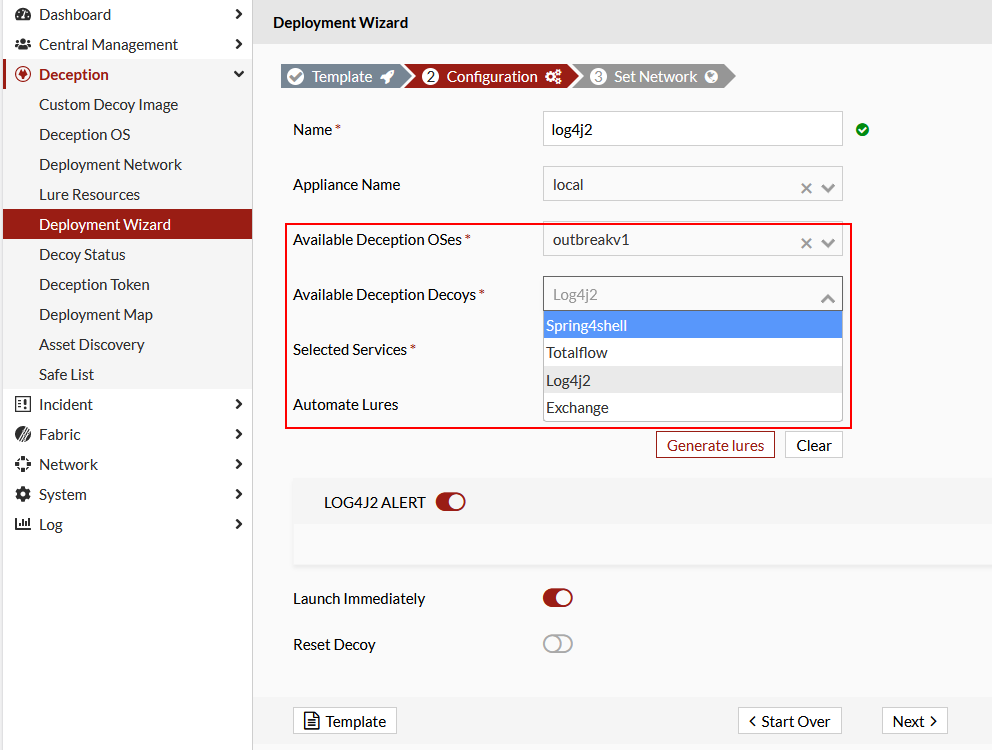
For more information about configuring deployment, see Deployment Wizard.
- Continue to follow the steps in the Deployment Wizard and then click Deploy.

- Go to Deception > Decoy Status to verify the decoy is running and configured correctly.

- Run a simulated attack with the Log4j2 traffic pattern
from an endpoint machine located within same deployment network as the outbreak decoy. For example,
curl -X POST http://10.10.1.124/login -F "test-f=\${jndi:ladp:test-f}" - Go to Incident > Analysis to verify the attack results.


