Integration with FortiSandbox
FortiSandbox is an anti-virus engine. When integrated, FortiDeceptor submits malware to FortiSandbox and retrieves the scanning result.
To integrate FortiDeceptor with FortiSandbox:
- Create a new user role in FortiSandbox.
- Integrate FortiDeceptor with FortiSandbox.
- Verify the scanning results in FortiDeceptor and FortiSandbox.
1. Create a new user role in FortiSandbox
Create a new user role whose with privileges to access JSON API.
- Create an Admin Profile with JSON API privileges. For information, see Admin Profiles in the FortiSandbox Administration Guide.
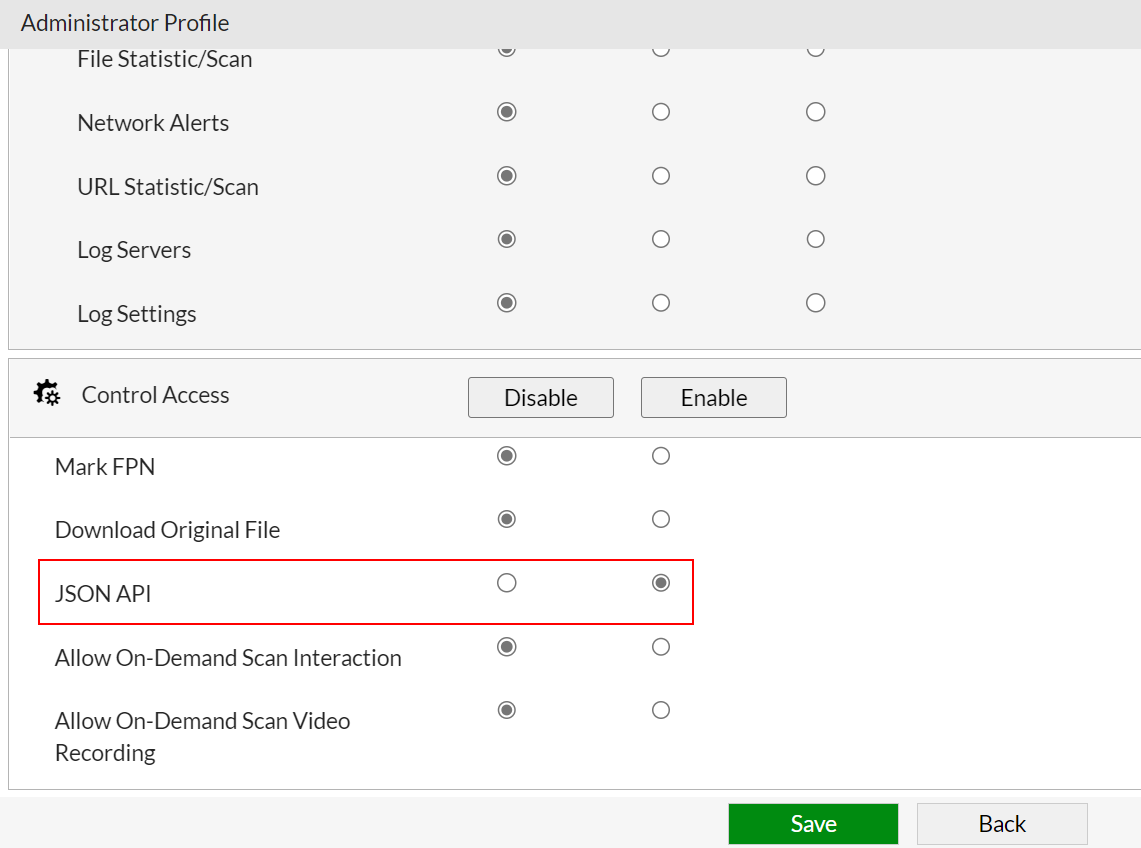
- Go to System > Admin Profiles and click Create New.
- Give the profile a descriptive Name such as
testApi. - Under Control Access, select JSON API. Configure the other settings as required and click Save.
- Create a new administrator with the profile you just created. For information see Administrators in the FortiSandbox Administration Guide.
- Go to System > Administrators, click Create New.
- Set administrator name and password.
- From the Admin Profile dropdown, select the profile you just created and click OK.

2. Integrate FortiDeceptor with FortiSandbox
- Configure a user on FortiSandbox to use for access from FortiDeceptor.
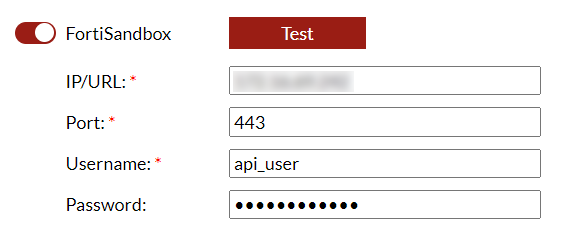
- In FortiDeceptor, go to Fabric > Detection Device. The Fabric Detection dialog opens.
- Enable FortiSandbox.
- Configure the device settings and click Save.
3. Verify the scanning results in FortiDeceptor and FortiSandbox
- Send a SMB/FTP put attack to the decoy from the endpoint.
- To verify the results in FortiDeceptor:
- Go to Incident > Analysis.
- Expand the incident and a make a note of the filename in the MD5 field and the FortiSandbox Result.

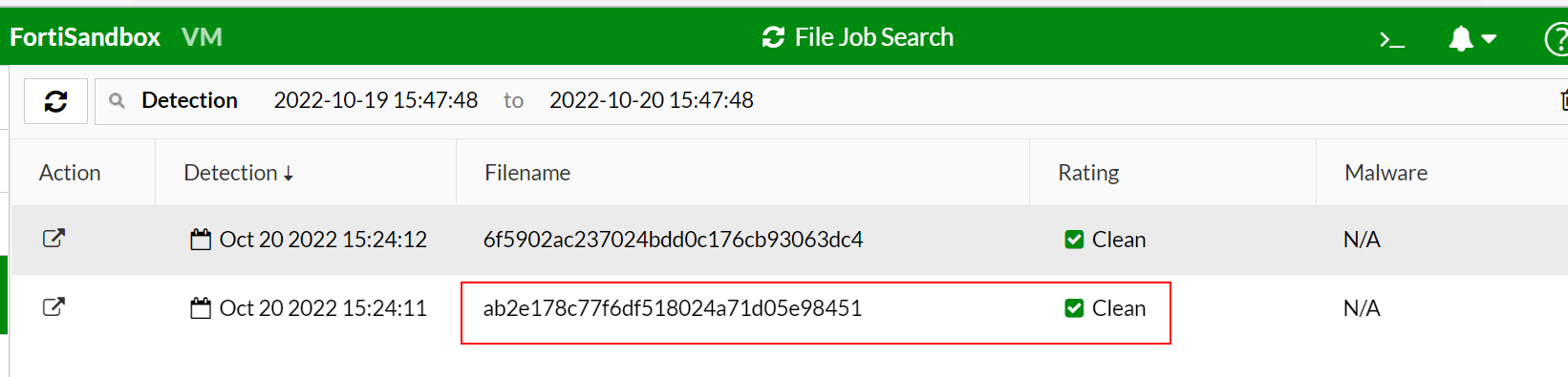
- To verify the results in FortiSandbox:
- Go to Scan Job > File Job Search.
- Search for the filename and verify the Rating is the same as the FortiSandbox Result in FortiDeceptor.