Threat Protection Example - Suspicious Movement
Description
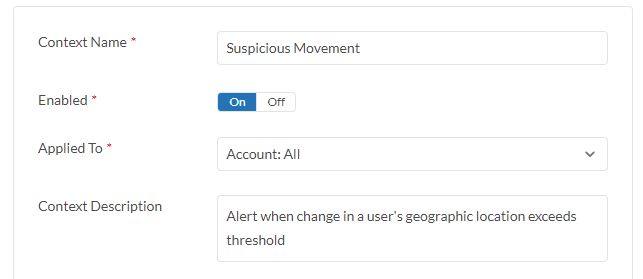
Suspicious Movement policy create finding when change in a user's geographic location exceeds preconfigured threshold.
Configuration Steps
- Go to Policy > Threat Protection > Suspicious Movement.
- Click on the right arrow key > next to the policy to display configuration setting.
- Click on Enabled toggle button to enable the policy.
- Click Applied To field to select target cloud account(s).
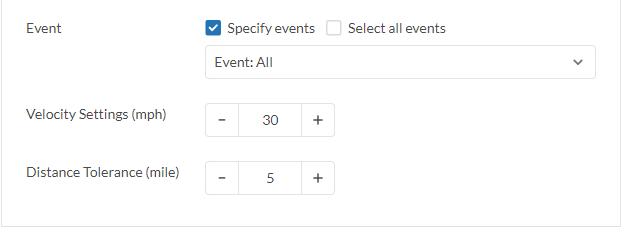
- In Velocity Settings field, enter a velocity greater than the maximum speed in international travel, e.g. commercial flight speed. The purpose is to monitor an unidentified login from another country.
- In Distance Tolerance field, enter the maximum distance for a user to travel in the vicinity before checking the velocity of the user. The purpose is to monitor for an unidentified login from another region within the country.
- Click Save Changes.
- Click the +Add Another to monitor Suspicious Movement on a different cloud account. (optional)
|
|
To setup a allow list for the Suspicious Movement Policy, please refer to Allowlist Configuration |

