Add Microsoft Azure Account
Follow each section below to help you setup the Azure Subscription, Roles, and configure the Blob Storage in preparation to add the Azure Subscription to FortiCNP.
- Prerequisites
- Setup Subscription
- Setup Blob Storage
- Enable Blob Log Monitoring
- Add Role to the Subscription
- Add User Access Administrator role to multiple subscriptions (optional)
- Setup Storage Blob Data Reader
- Add Azure Account to FortiCNP
Prerequisites
Account Requirement
You may use an existing Azure AD (Azure Active Directory) account or create a new one. Other types of Azure account will not be able to add to FortiCNP.

If you create a new account, wait for at least 24 hours for the new account to take effect before granting access to FortiCNP.
Role Requirement
Make sure the user account that will be added on FortiCNP has one of the following role(s) before adding the account to FortiCNP:
- Global Administrator role
- Cloud Application Administrator and Global Reader roles
FortiCNP supports all types of Azure AD licenses. However, depending on the features supported by the Azure AD license, FortiCNP will only integrate features available to that license. For example, a free Azure AD license does not include sign-in activity report, thus FortiCNP cannot provide sign-in activities from the free Azure AD account.
Setup Subscription
Once you have your Azure license ready, you will need a subscription ID to use FortiCNP. If you do not have a subscription yet, please follow these steps:
- Log into the Azure portal using your Azure account.
- Search and click on Subscriptions.
- Click on +Add button to add a subscription.
- Select the subscription desired and complete the rest of the billing steps.
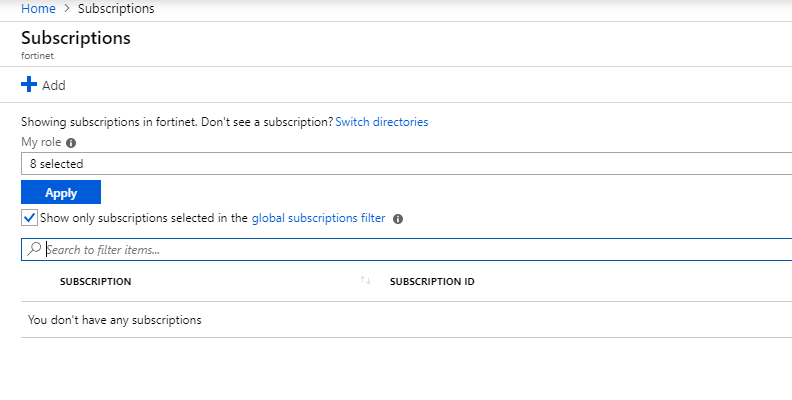

Note: You will need a minimum of "Pay-As-You-Go" subscription to use FortiCNP.
Setup Blob Storage
An Azure Storage account with blob log monitoring enabled is required to install FortiCNP. If you do not have a storage account yet, please follow the steps below to create a storage account:
- From the portal page, search and click on storage account.
- Click +Create to create a storage account.
- Under Basics > Subscription field. Make sure you select the subscription that is linked to your subscription ID.
- In Resource group field, select a resource group based on your preference or create a new one.
- In Storage account name filed , enter an account name based on your preference.
- Click Review + create. Once validation passed, click Create.

Enable Blob Log Monitoring
Once storage account is created, to enable blob log monitoring, follow the steps below:
- Select the storage account of interest.
- From the left menu, select Monitoring (classic) > Diagnostic settings.
- Turn On diagnostic logs. Under the Blob properties, enable Read/Write/Delete under Logging.

Add Role to the Subscription
Add Reader, Owner, or User Access Administrator role to the Subscription that is going to be added FortiCNP. (Only one role is required) The purpose is to provide FortiCNP with read access to the resources under the Subscription.
- Search and click on Subscriptions.
- Click on the Subscription that is going to be used on FortiCNP.
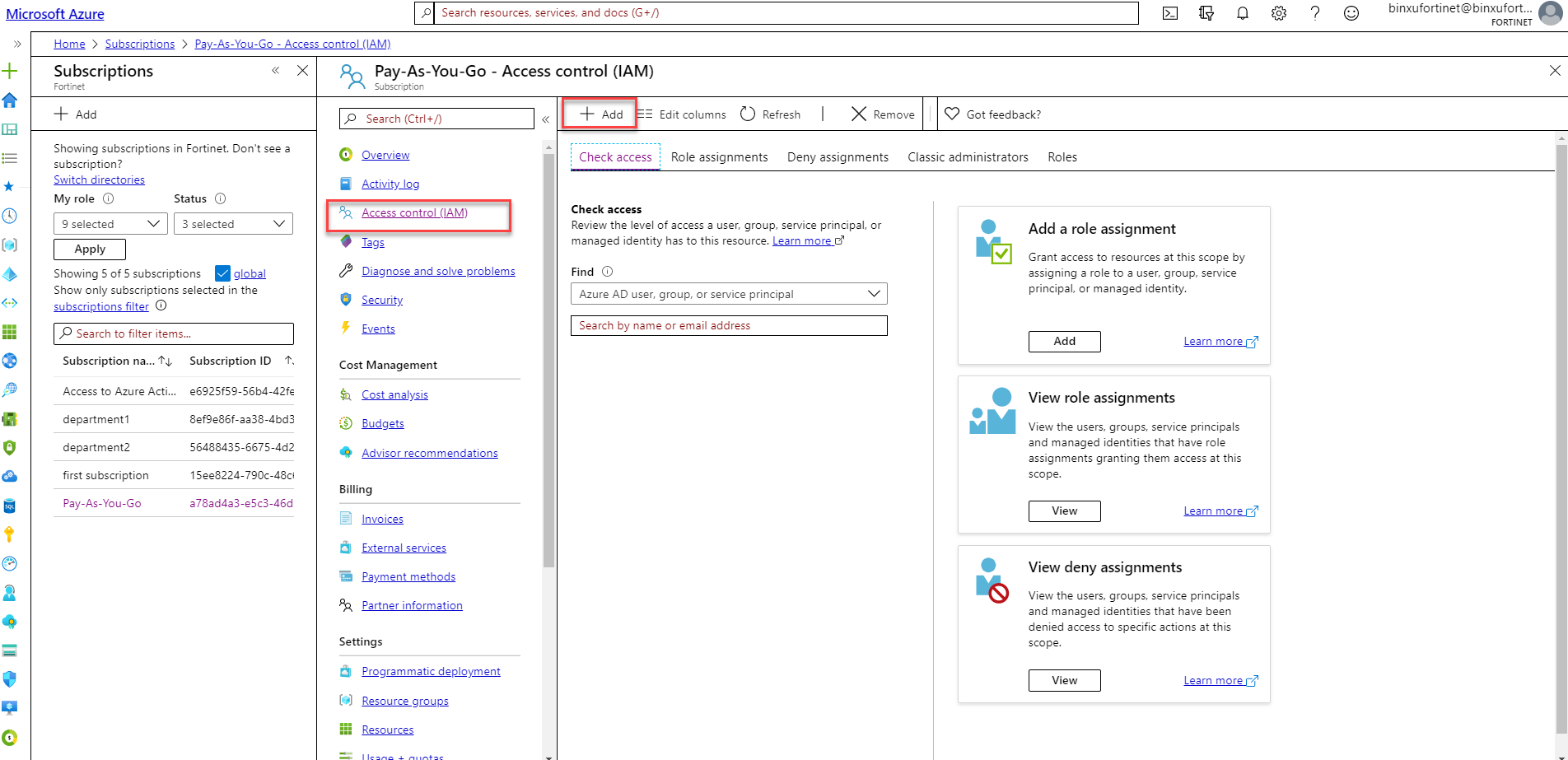
- In the Subscription menu, click on Access control (IAM).
- Click on + Add and select "Add role assignment".
- In Add role assignment drop down menu, click on Select a role and select Reader, Owner, or User Access Administrator.
- Leave Assign access to as "User, group, or service principal".
- In Select field, search and select a member (user account) that will be associated with the role.
- Click Save to finish creating the role.
 '
'
Note: If you want to select User Access Administrator, please complete Add User Access Administrator role to multiple subscriptions (optional) to make User Access Administrator as an available option in Add role assignment.

|
|
The user account should have a Global Administrator role or Cloud Application Administrator + Global Reader roles as stated in Role Requirement. |
Add User Access Administrator role to multiple subscriptions (optional)
To add multiple subscriptions to FortiCNP with one user account simultaneously, follow these steps to configure the subscriptions with read access. If the user account has Global Administrator role, only do step 6-9.
- Log in to Azure portal as the master account user.
- In the search field, search and click on "users".
- Click on the user that will be used when adding the Subscriptions to FortiCNP.
- In the middle Profile navigation menu, click on Assigned roles.
- Click +Add assignments to add Global Administrator role to the user.
- Log out of the master account user, and log back in as the user whom the new roles are assigned to.
- Search and click on "Azure Active Directory".
- In the Azure Active Directory navigation menu, click on Properties.
- Click Yes under Access management for Azure resources, and click save. This step allows the user to manage access to all Subscriptions under the Azure account.
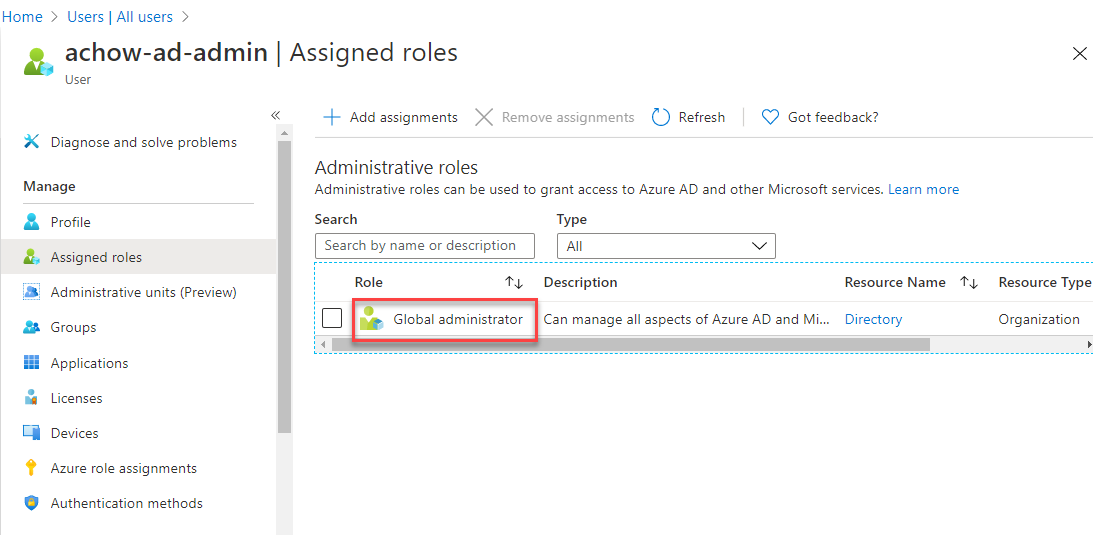

Now all the Subscriptions under the user account have User Access Administrator role, and you can add multiple Azure Subscriptions at the same time.
Setup Storage Blob Data Reader
Another role to be added to the Azure AD user is Storage Blob Data Reader. This is a necessary step for FortiCNP DLP and virus scan to read and analyze the data stored in the Storage Blob account as well as integrating Azure cloud traffic in FortiCNP.
- From the Azure portal page, search and click Subscriptions.
- Select your subscription.
- Select Access Control (IAM), and click +Add, then Add role assignment pane will pop-up.
- In Role field, type and select Storage Blob Data Reader.
- In Assign access to field, leave it as Azure AD user, group, or service principal.
- In Select field, type and select the name or e-mail address of the Azure AD user.
- Click Save to complete granting the role to the Azure AD user.

At the end of this step, please confirm that your Azure AD account subscription has one of the following roles combinations as the table below:
|
Roles Combinations |
|---|
| Reader and Blob Storage Reader |
| User Access Administrator and Blob Storage Reader |
| Owner and Blob Storage Reader |
Add Azure Account to FortiCNP
After all the Azure configurations are completed from previous sections, follow these steps to add your Azure account on FortiCNP.
- Log into FortiCNP with your account, and select Cloud Protection.
- From the navigation menu, go to ADMIN > Account, and select +Add New.
- Select Azure, and click Next. Review the key configuration summary and click Next.
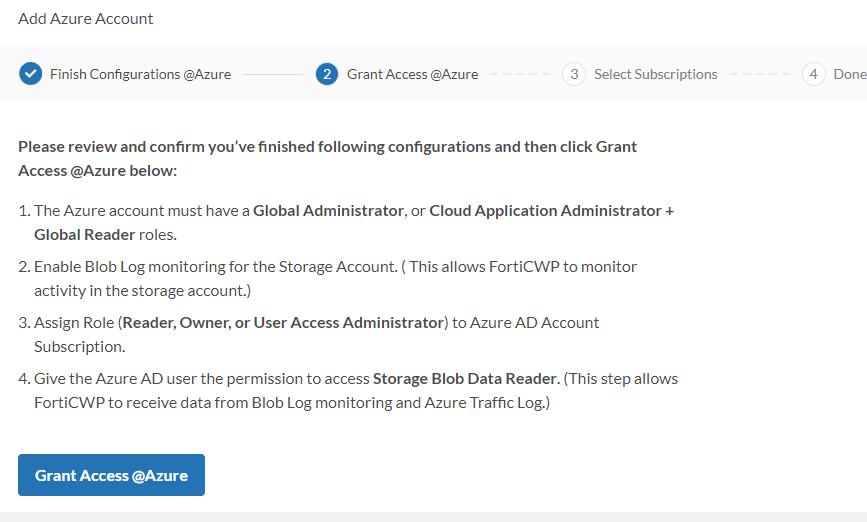
- Click Grant Access @Azure to be re-directed to Azure portal.
- Log in with your Azure account, and a permission request page will pop-up.
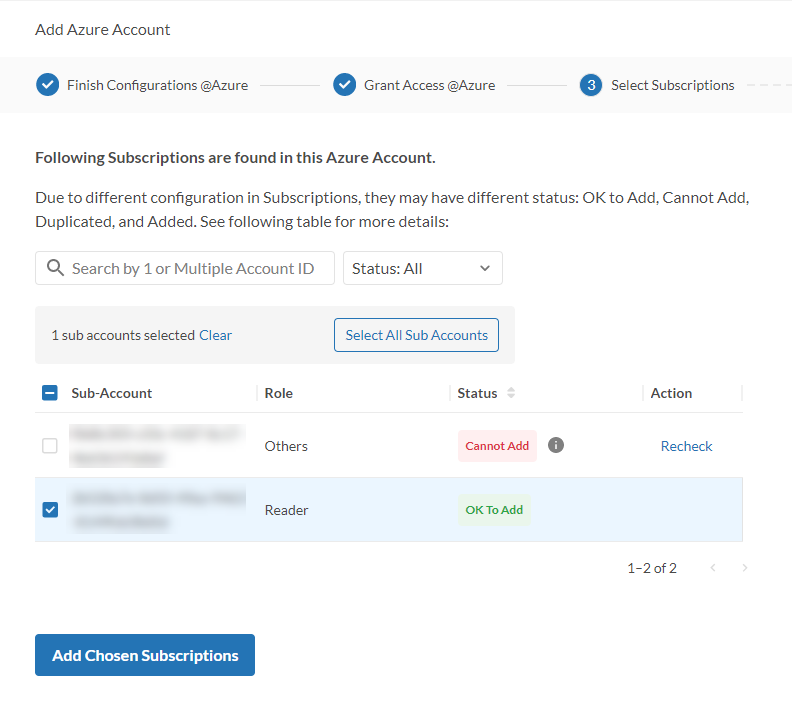
- Click Accept to grant FortiCNP with the permissions requested.
- Azure will be prompt you to grant the same permissions 3 times, then you will be re-directed back to FortiCNP.
- Select the subscription that is Ok to Add to FortiCNP, and click Add Chosen Subscription.
|
|
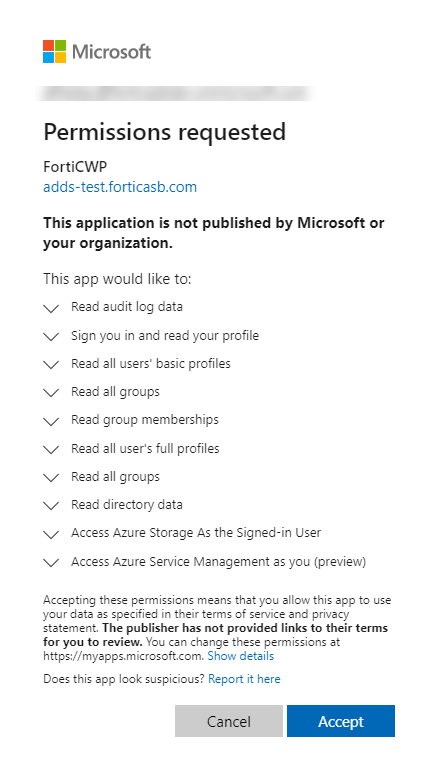
FortiCNP does not request all but only partial permissions from the global administrator user. Below is a list of permissions requested by FortiCNP. |
|
Permissions requested by FortiCNP |
| Read audit log data | |
| Sign you in and read your profile | |
| Read all users' basic profiles | |
| Read all groups | |
| Read group memberships | |
| Read all user's full profiles | |
| Read all groups | |
| Read directory data | |
| Access Azure Storage As the Signed-in User | |
| Access Azure Service Management as you (preview) | |