Enable Microsoft Azure Integration
FortiCNP provides Azure cloud integration where it integrates Azure cloud security integration data and provide real time cloud security monitoring. FortiCNP will receive security findings from Azure security integration and informs users of probe findings.
Prerequisite
An active Microsoft Azure AD account with security policy setup is required for Microsoft Azure to provide cloud integration data to FortiCNP.
Steps to Enable Azure Cloud Integration
Data Collection will be setup first. After Data Collection is activated, enable integration to allow security center to integrate with other Microsoft security services by allowing other services to access cloud data.
- Log in to Azure portal with you Azure AD account: https://portal.azure.com/.
- Search and click on Microsoft Defender for Cloud.
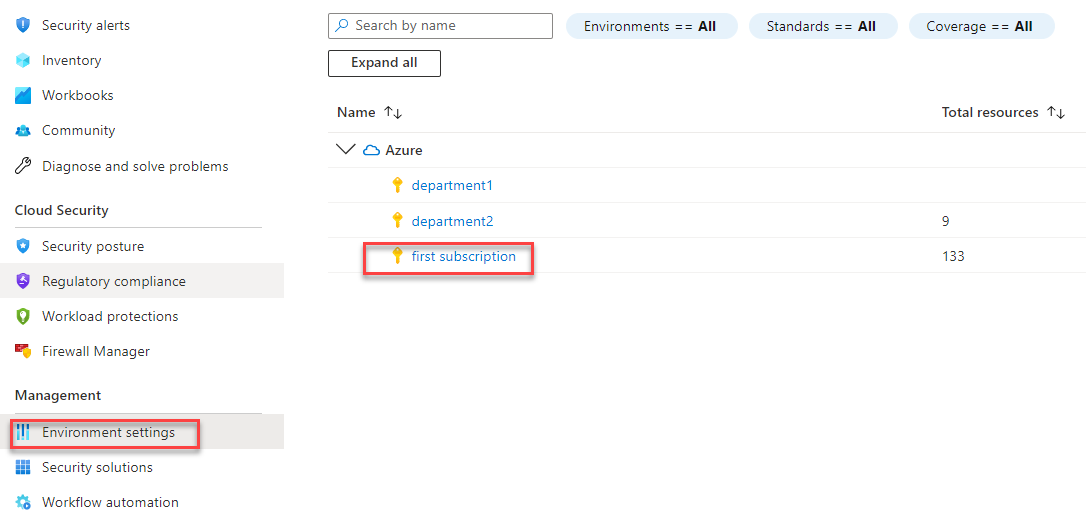
- Go to Management > Environment settings, and click on your current Azure Subscription.
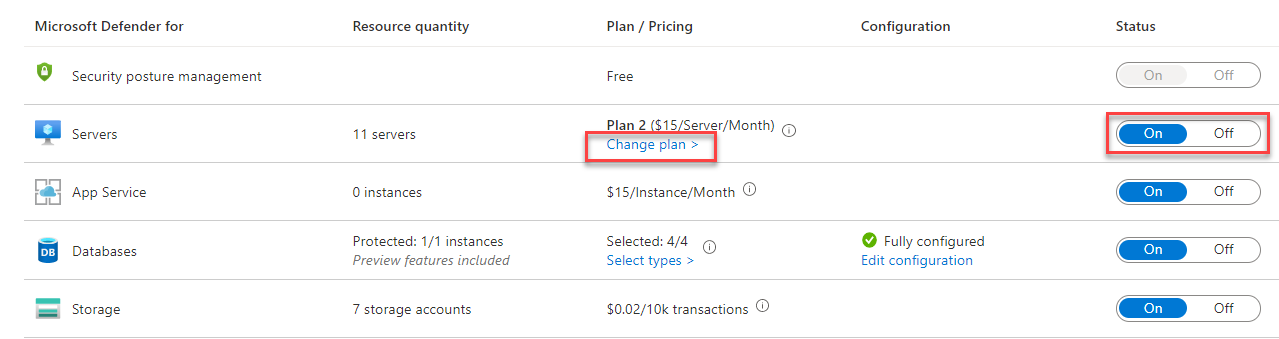
- In Servers resource type, turn on the toggle switch button to activate it, and click Change plan >.
- Select Microsoft Defender for Servers Plan 2 and click Confirm.
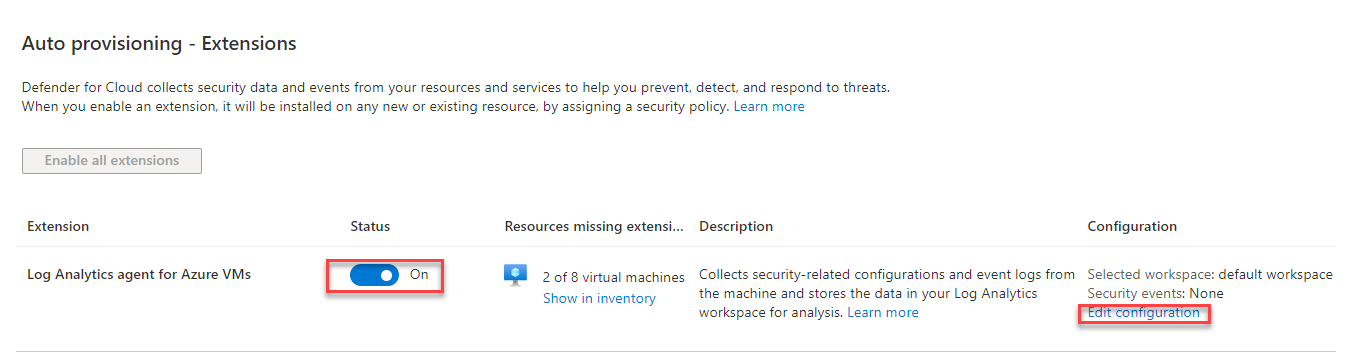
- Go back to Settings menu and click Auto provisioning
- Turn on the Extension: Log Analytics agent for Azure VMs and click Edit Configuration.
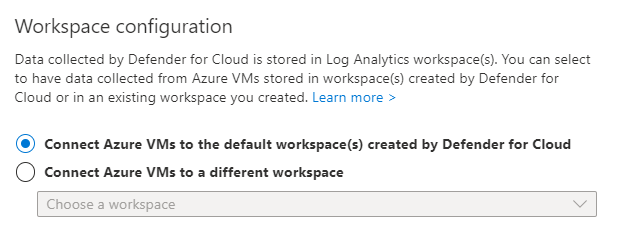
- In Workspace configuration, select Connect Azure VMs to the default workspace(s) created by Defender for Cloud.
- In Store additional raw data - Windows security events, select Common, and click Apply.
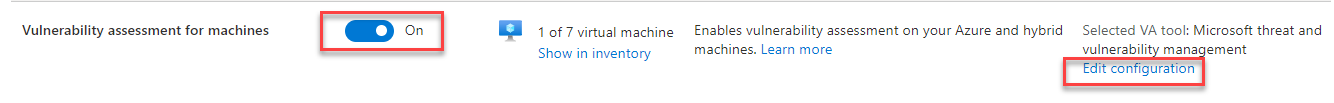
- Turn on another Extension: Vulnerability assessment for machines and click Edit configuration.
- Select Microsoft threat and vulnerability management and click Apply.
- Go back to Settings > Integrations.
- In Enable integrations, enable both integrations:
- Allow Microsoft Defender for Cloud Apps to access my data
- Allow Microsoft Defender for Endpoint to access my data.
Note: Other Defender plans are recommended, but not required.

Note: other extensions are recommended to be turn on, but not required.

Steps to setup Azure Security Policy (Optional)
If you have Azure Pay as you go subscription, having Data Collection and Threat detection setup is sufficient for Azure Integration. For Azure full subscription users, you may setup security policy.
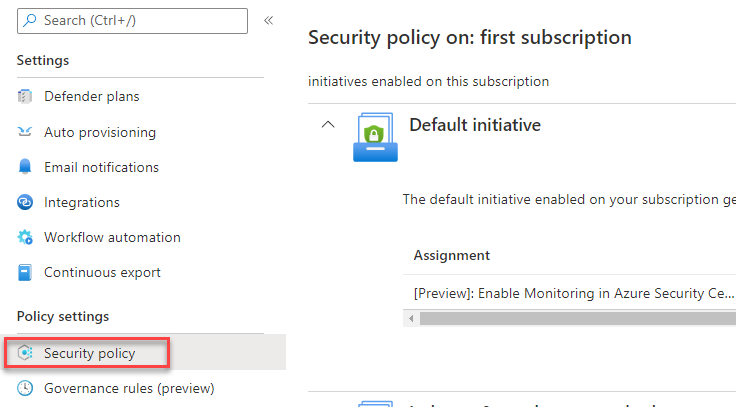
- Continue from the steps above in the same subscription setting, go to Security Policy.
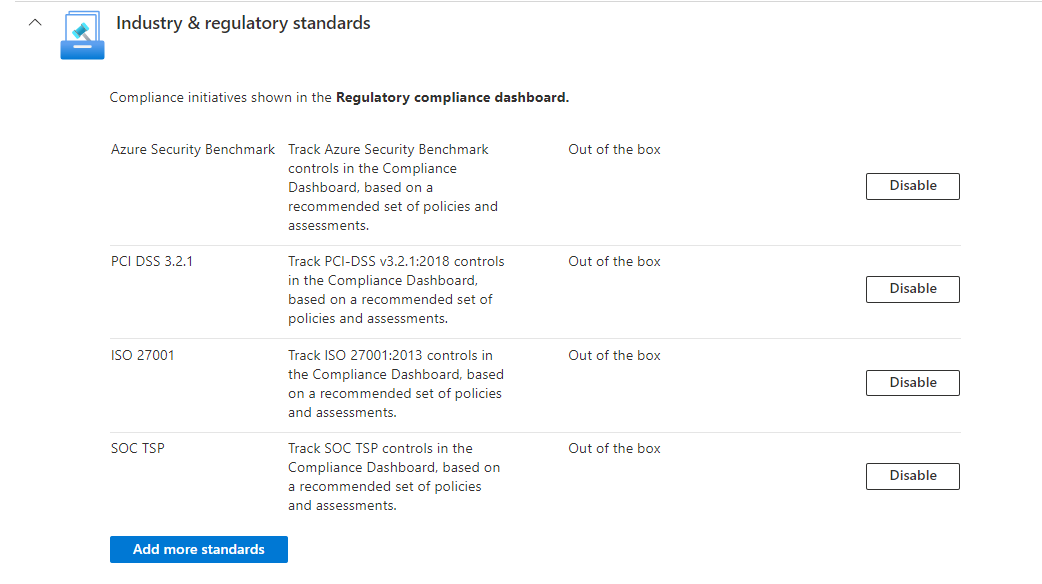
- Enable the security policies required by your organizations.
After Azure data collection and integration is enabled, FortiCNP is able extract cloud integration data from Azure and provide real time cloud security monitoring.

