FortiSandbox support for FortiClient (macOS)
FortiClient (macOS) endpoints can now submit high-risk files to FortiSandbox for analysis. If FortiSandbox detects the submitted file as malicious, then FortiClient quarantines the file. FortiClient (macOS) can submit files to on-premise FortiSandbox appliances only, and cannot submit files to FortiSandbox Cloud.
The FortiClient (macOS) endpoint must be registered to EMS 6.2.0. The FortiSandbox server that FortiClient uses for file submission must authorize EMS.
This feature currently has the following limitations:
- FortiClient (macOS) does not support real-time blocking the file being submitted to FortiSandbox. Therefore, the Wait for FortiSandbox Results before Allowing File Access option does not apply to FortiClient (macOS). Only if FortiSandbox detects the file as malicious does FortiClient (macOS) quarantine the file.
- FortiClient (macOS) does not automatically include files signed by Apple Inc. as files from trusted sources.
- FortiClient (macOS) does not submit Sandbox detection logs to FortiAnalyzer.
To configure FortiSandbox scanning for FortiClient (macOS):
- In EMS, select the desired endpoint profile.
- On the profile's Sandbox tab, enable Sandbox Detection.
- Configure Server options:
- Under FortiSandbox, select Appliance.
- In the IP address/Hostname field, enter the FortiSandbox IP address.
- Click Test Connection.
- In FortiSandbox, go to Scan Input > Devices. Search for and authorize the EMS serial number. You can find the EMS serial number in the System Information widget on the EMS dashboard.
- EMS displays that FortiSandbox has authorized EMS. You can now configure the inspection mode. For macOS, it is recommended to select All Supported Extensions.
- Under File Submission Options, select All Web Downloads and All Email Downloads. FortiClient (macOS) only supports submitting web and email downloads.
- Under Remediation Actions, select Quarantine or Alert & Notify. The user can access the file after FortiClient submits the file for analysis. FortiClient only quarantines the file if FortiSandbox analysis reports the file as malicious.
- Under Exceptions, exclude files from submission based on folder paths or filenames.
- Click Save. EMS applies the profile changes to the endpoint with the next Telemetry communication.
After FortiClient (macOS) receives the Sandbox configuration from EMS, it can submit files for analysis to FortiSandbox. In this example, FortiClient submits a clean file downloaded from a web browser to FortiSandbox. FortiClient displays that one file has been submitted in the SUBMITTED tile. FortiClient waits for the results from FortiSandbox. FortiClient receives the verdict from FortiSandbox that the file is not malicious, and displays that one file has been detected as CLEAN.

When FortiClient submits a malicious file to FortiSandbox and FortiSandbox detects it as malicious, FortiClient quarantines the file and displays the following dialog.

FortiClient also displays that FortiSandbox has detected a zero-day file.
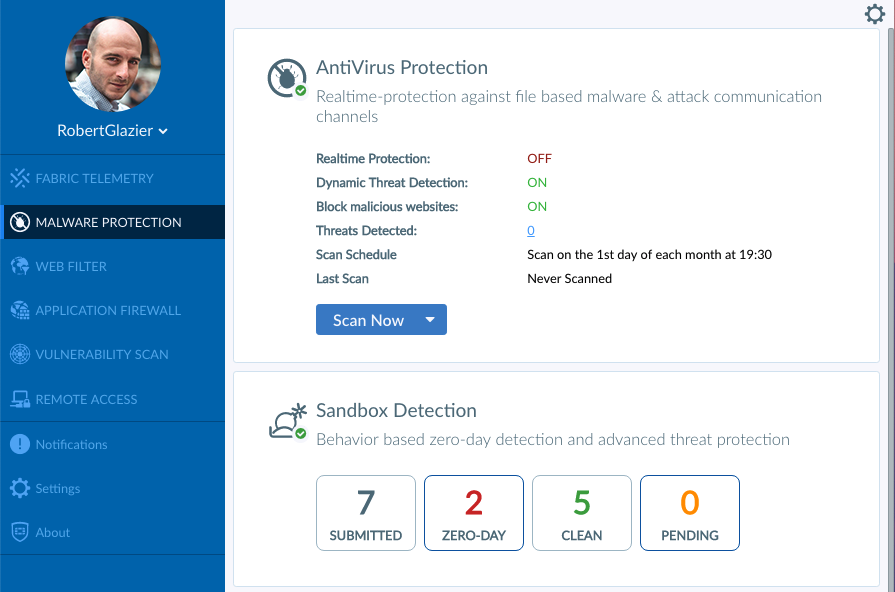
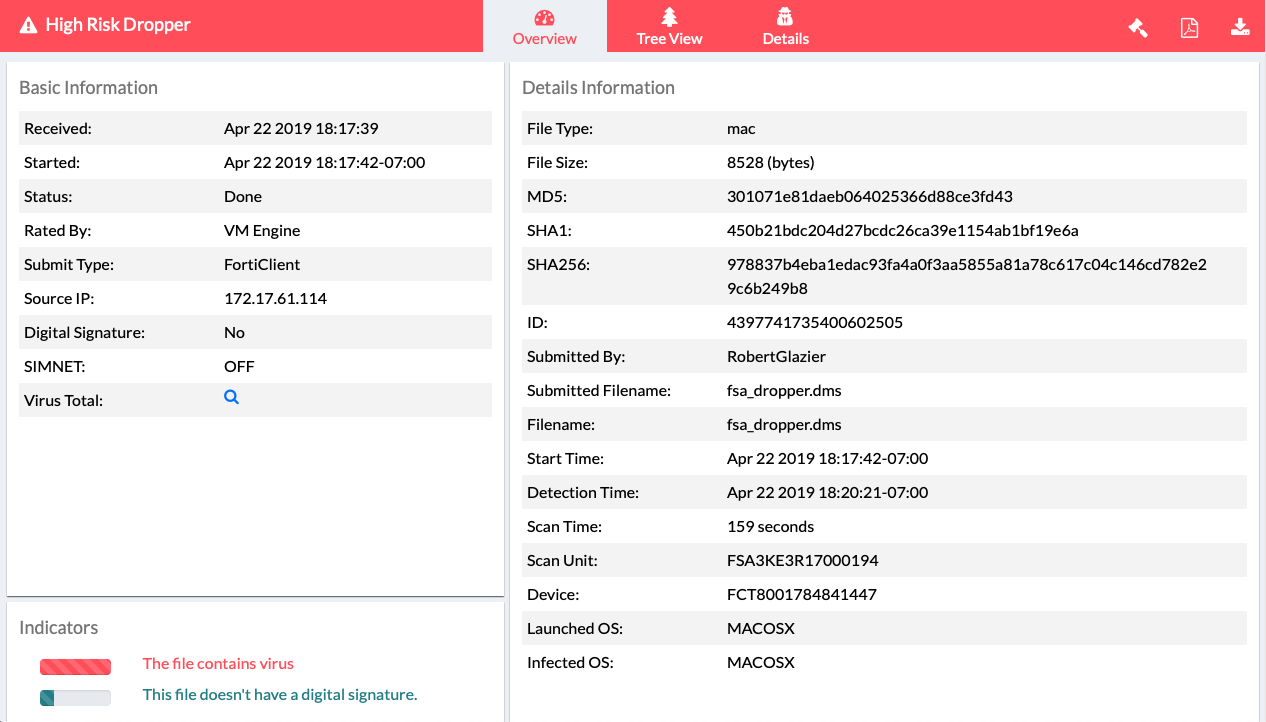
The FortiSandbox administrator can see the quarantined file's details.
The FortiClient user can see the file details in Malware Protection > Zero Day > Sandbox Quarantined Files.

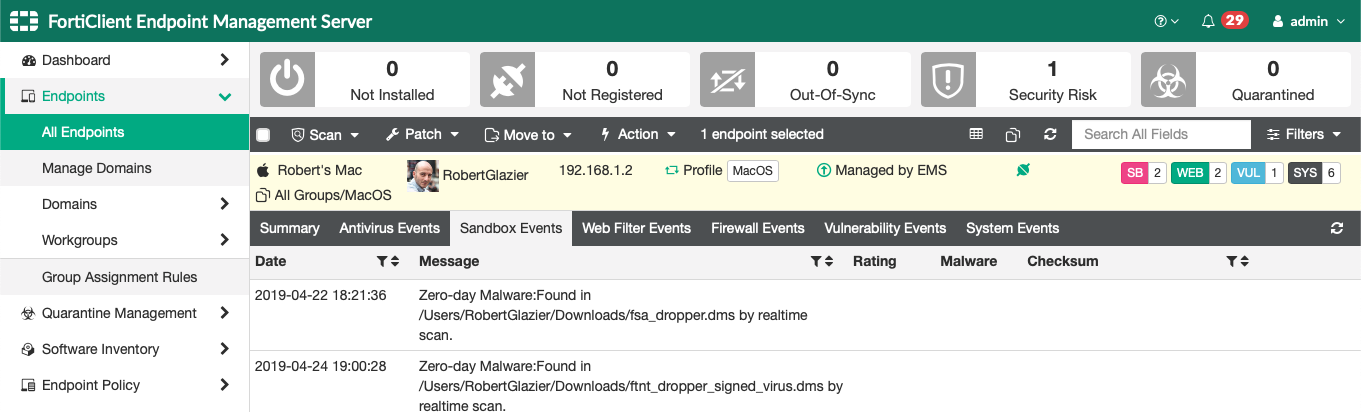
The EMS administrator can view the Sandbox event for the FortiClient endpoint.