Creating unique service account credentials
Creating a unique set of service account credentials provides more security. Unique service account credentials include the following:
- Client ID (a long number)
- Service account ID (email address)
- Service account certificate (a certificate in
.pemformat)
To create a unique service account:
- Go to https://console.developers.google.com.
- Log in with your G Suite account credentials.
- Create a new project:
- Click the toolbar list. The browser displays the following dialog.

- Select your organization, if you see an organization dropdown list.
- Click the + button.
- In the Project name field, enter your project name, then click Create.
- Click the toolbar list. The browser displays the following dialog.
- Enable the Admin SDK:
- Select your project from the toolbar list, then go to the Library tab.
- Under G Suite APIs, click Admin SDK.
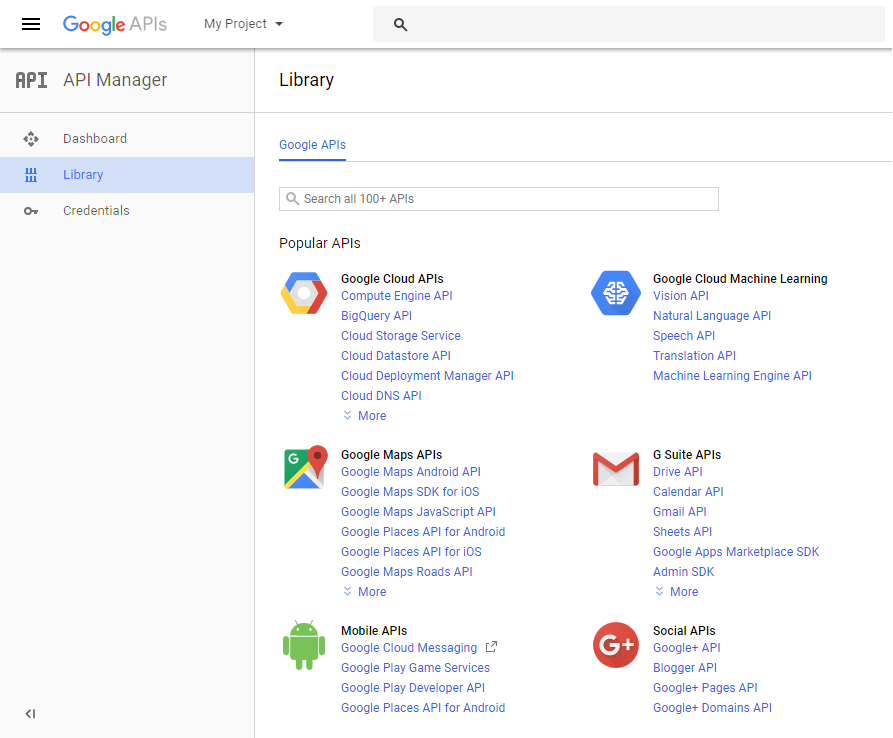
- Click ENABLE.

- Create a service account:
- Go to the Credentials tab and select Create Credentials > Service account key.
- From the Service account list, select New Service Account. Enter a service account name.
- From the Role list, select Project > Viewer.
- Select P12 as the Key type and click Create.

After you create the service account, a private key with the
P12extension is saved on your computer.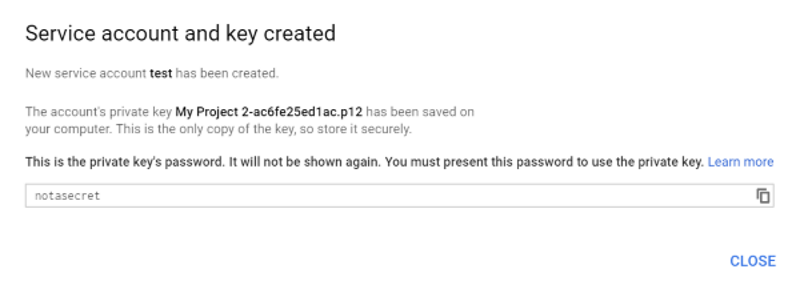
- Go to the Credentials page > Manage service accounts.
-
Edit the service account you just created and select the Enable Google Apps Domain-Wide Delegation checkbox. Enter a Product name for the consent screen if this field appears.
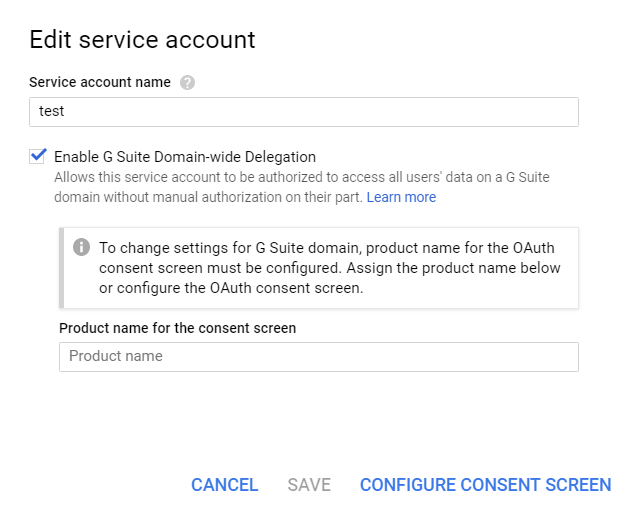
- Click Save.
- Click View Client ID to see your service account information. Record the client ID, service account, and the associated private key (downloaded in step 5d).
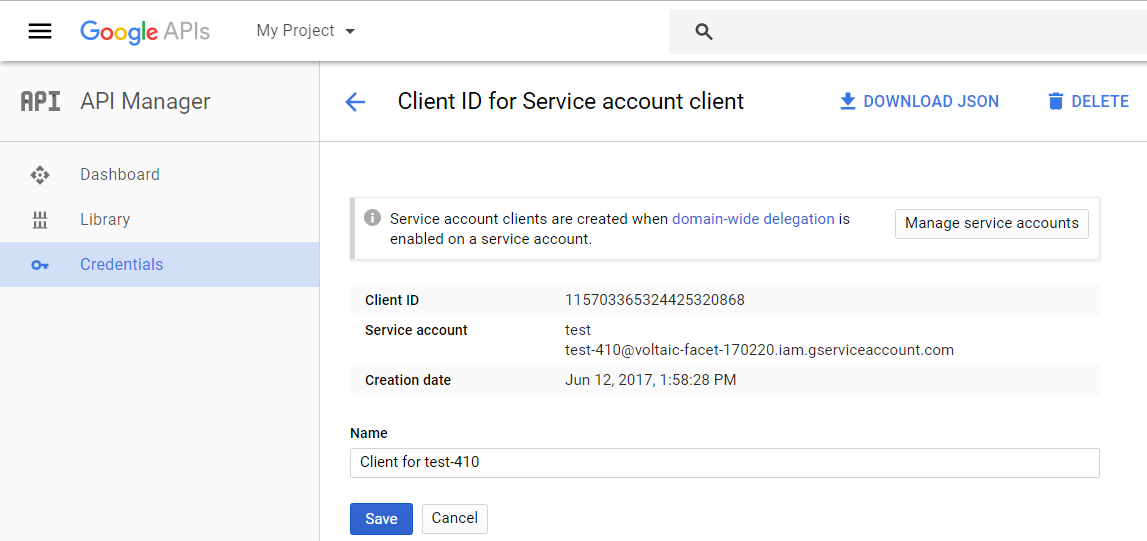
|
|
To use the private key in EMS, it needs to be converted to C:\OpenSSL-Win64\bin>openssl pkcs12 -in demo-976b9d6e9328.p12 -out serviceAccount-demo.pem -nodes -nocerts Enter Import Password: |

