Testing and verification
The following demonstrates connection via Web mode and Tunnel mode using SAML authentication. Review the authentication process at the beginning of this deployment scenario to understand how the process works.
For Web mode, import the CA certificate of the FortiAuthenticator Local CA into the trusted certificate store used by your browser. This will prevent warnings from appearing when accessing the SSL VPN web portal.
Web mode SSL VPN
To verify a Web mode SSL VPN connection with the Finance user Dan Parker (dparker):
-
Open a browser, and enter
https://10.0.3.254:10443. -
Click Single Sign-On to sign in.

Your sign-on request will be redirected by the FortiGate SAML SP to the FortiAuthenticator SAML IdP.
-
Enter the user credentials for the user and click Login.
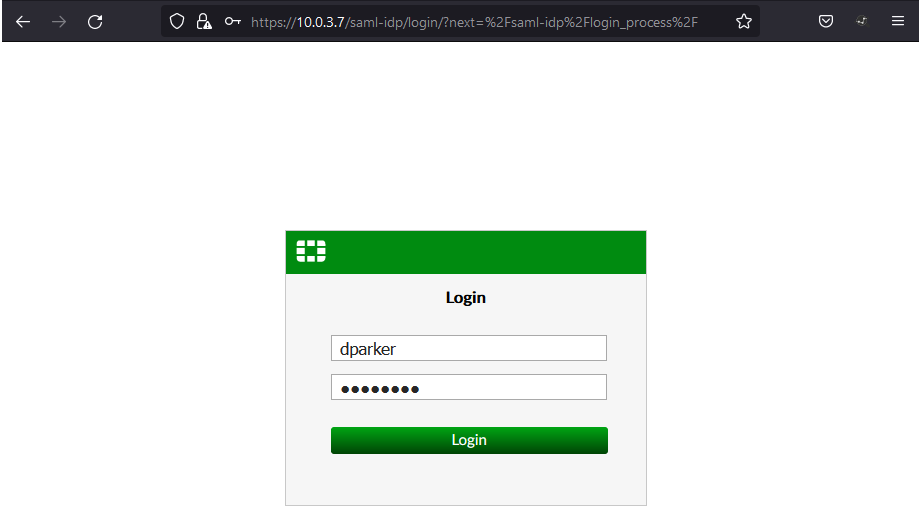
In the background, the FortiAuthenticator authenticates this user over the LDAP connection to the Windows AD. If the authentication succeeds and matches a user group on FortiAuthenticator, FortiAuthenticator sends a SAML assertion back to the browser containing the username and group information.
The browser redirects the SAML assertion to the FortiGate SAML SP, which matches the username and group information to a user group. Based on this user group, access is granted.
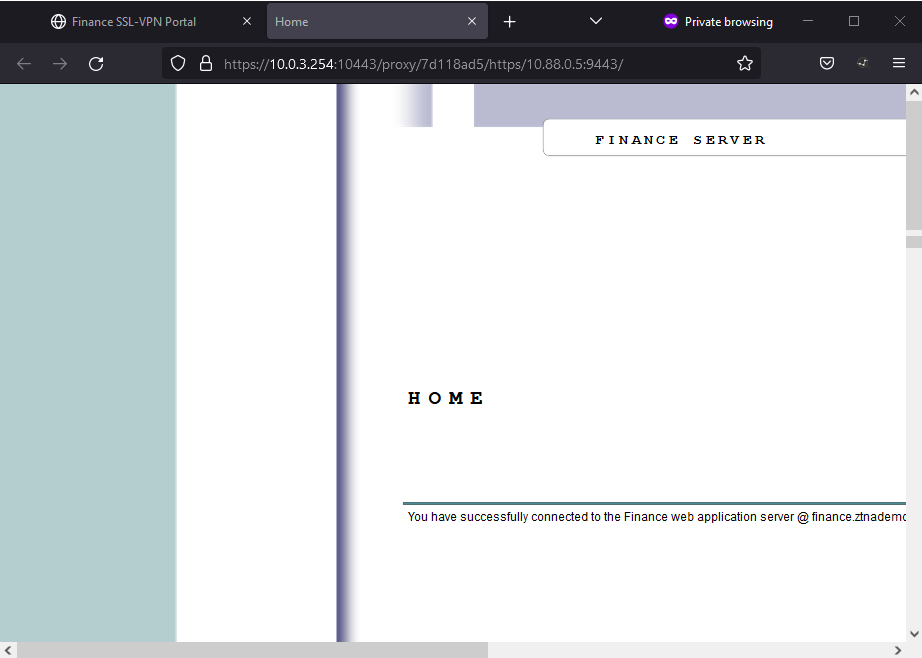
The Finance user can now see the Finance SSL-VPN Portal.

- Clicking on the Finance Server bookmark, the user can access the Finance server.
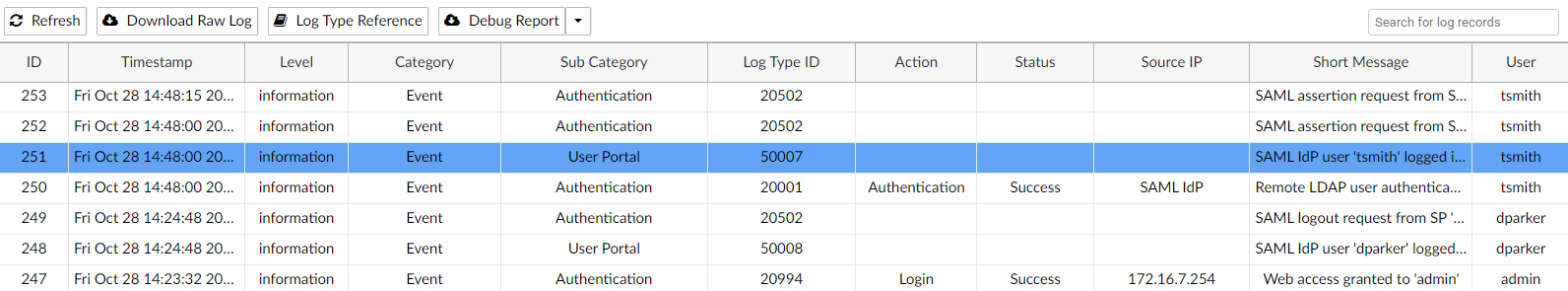
To verify the login status on the FortiGate and FortiAuthenticator:
-
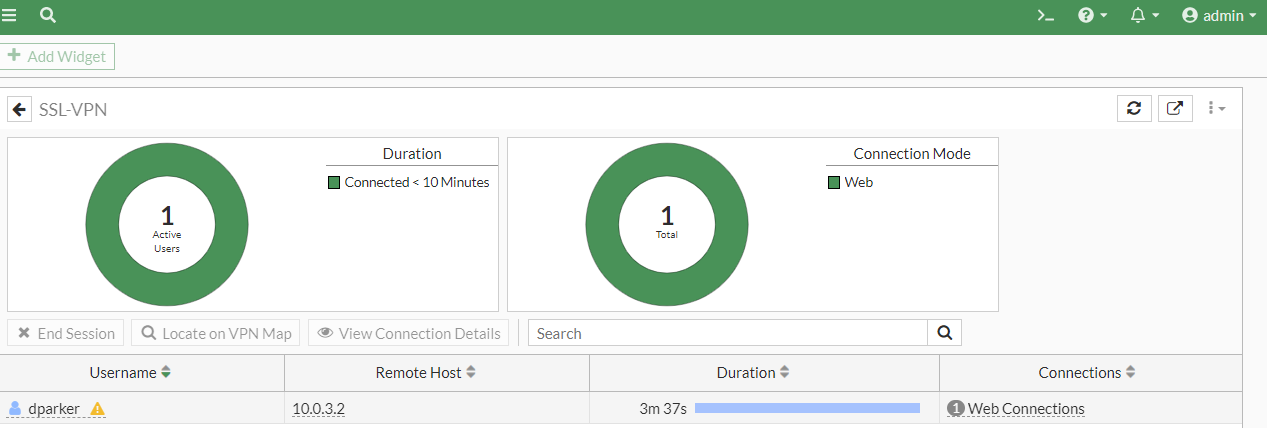
On FortiGate, go to Dashboard > Network and expand the SSL-VPN widget.
-
From Log & Report > System Events, switch to VPN Events log.
Alternatively, in the CLI console, enter the following commands:
execute log filter category 1
execute log filter field subtype vpn
execute log display
1974 logs found.10 logs returned.38: date=2022-10-28 time=14:20:00 eventtime=1666992000214198069 tz="-0700" logid="0101039938" type="event" subtype="vpn" level="warning" vd="root" logdesc="SSL VPN pass" action="ssl-web-pass" tunneltype="ssl-web" tunnelid=165774014 remip=10.0.3.2 user="dparker" group="Finance" dst_host="10.88.0.5" reason="https" msg="SSL web application activated - On FortiAuthenticator, go to Logging > Log Access > Logs.
The SAML IdP authentication for dparker will be displayed.

Tunnel mode SSL VPN
To verify a Tunnel mode SSL VPN connection with the Sales user Tom Smith (tsmith):
- On the client desktop, open FortiClient and go to the Remote Access tab.
- Select the VPN tunnel created earlier and click SAML Login.
- When prompted for the login credentials, enter the username and password and click Login.

Again, in the background, the SAML login request gets processed by FortiAuthenticator. Upon a successful match, it sends a SAML assertion back to the FortiClient. The FortiClient forwards this to the FortiGate which matches a corresponding user group.
- Once connected, the user can open a browser and browse to
https://10.88.0.3:9443to access the Sales webserver.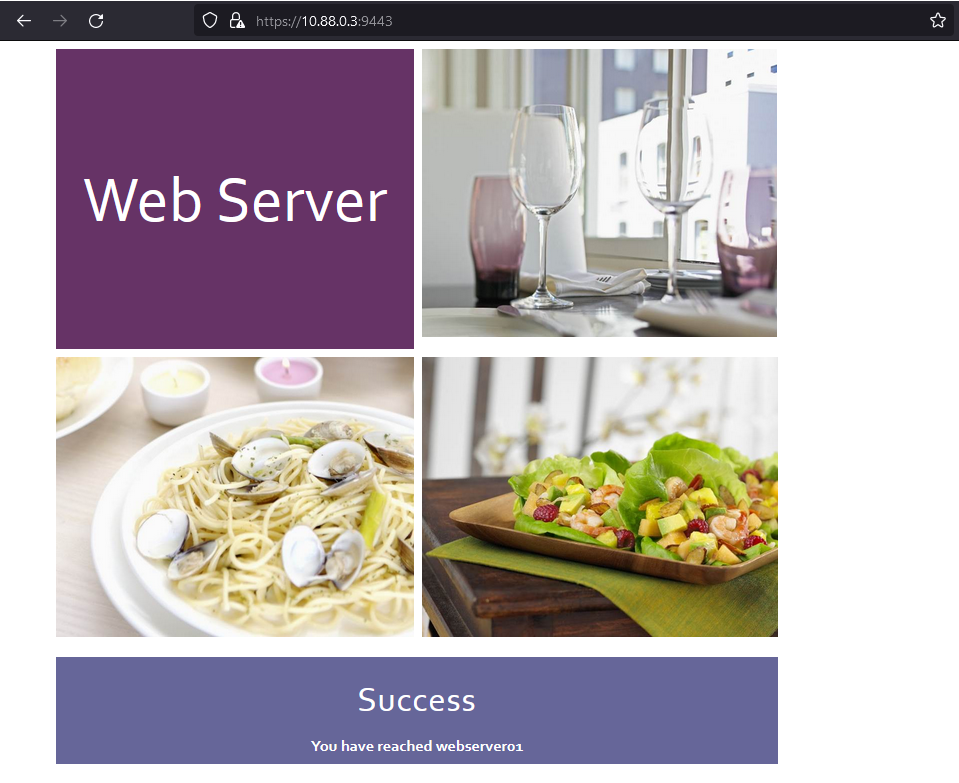
To verify the login status on the FortiGate and FortiAuthenticator:
- On FortiGate, go to Dashboard > Network and expand the SSL-VPN widget.

-
Go to Dashboard > User & Devices and expand the Firewall Users widget.

- From Log & Report > System Events, switch to VPN Events log.
Alternatively, in the CLI console, enter the following commands:
execute log filter category 1
execute log filter field subtype vpn
execute log display
2063 logs found.10 logs returned.10: date=2022-10-28 time=14:48:24 eventtime=1666993704610253079 tz="-0700" logid="0101039947" type="event" subtype="vpn" level="information" vd="root" logdesc="SSL VPN tunnel up" action="tunnel-up" tunneltype="ssl-tunnel" tunnelid=165774015 remip=10.0.3.2 tunnelip=10.212.134.200 user="tsmith" group="Sales" dst_host="N/A" reason="tunnel established" msg="SSL tunnel established" - On FortiAuthenticator, go to Logging > Log Access > Logs.
The SAML IdP authentication for tsmith will be displayed.