Offline token configuration
The instructions below describe how to configure FortiAuthenticator Agent offline token support. Offline tokens allow the Windows Agent to cache future tokens for users when they are offline or the FortiAuthenticator is unreachable
FortiAuthenticator configuration
To configure the FortiAuthenticator to enable offline token support:
- Go to Authentication > User Account Policies > Tokens.
- Under FAC Agent Offline FortiToken Support, select Enable offline support.
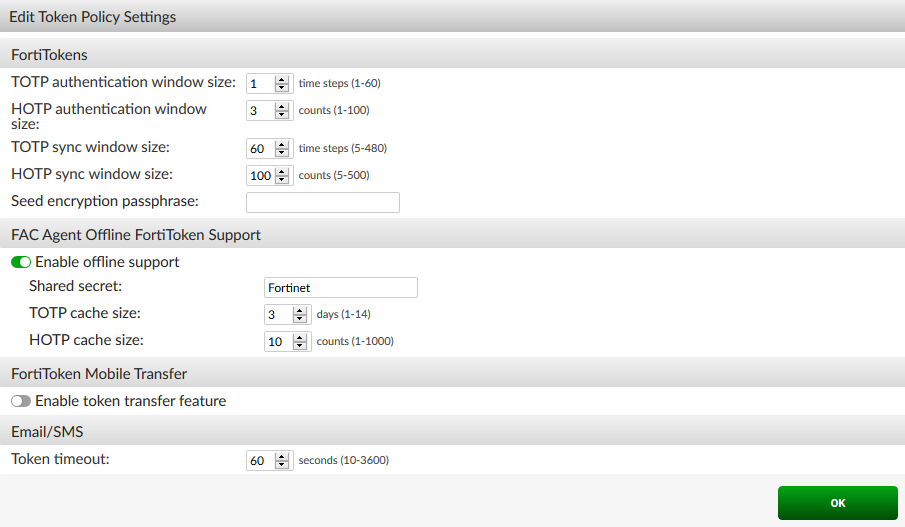
Now we need to generate the web service key for the Windows agent to talk to FortiAuthenticator with an associated administrative account. Once enabled on the account, the key will be emailed to the email address in the account details from FortiAuthenticator.
- Go to Authentication > User Management > Local Users and edit the admin account.
- Under User Role, enable Web service access and provide the appropriate email address under User Information.
- Go to Authentication > User Management > Remote Users and ensure that LDAP users are imported in FortiAuthenticator and Tokens are enabled.

- Go to Authentication > Self-service Portal > Access Control and set the Access Control realm to the LDAP server where we want the users to be authenticated.

FortiAuthenticator Agent for Windows configuration
To set up FortiAuthenticator Agent for Microsoft Windows:
- Log on to the host system where the Windows agent has been installed.
- Select the General tab and select the Configure button to load the configuration settings.
- Verify the IP address of the FortiAuthenticator server and the administrator account name.
- Copy the Web Service Key that was emailed to the administrator account into the Rest API Key box.

- Next, select the Offline tab and verify the following:
- Check the Enable offline token when available… box.
- Enter the Shared Secret that was set on the FortiAuthenticator (Authentication > User Account Policies > Tokens).
- Verify that the Domain is the correct AD Domain and the Realm is an exact match to the realm setup in FortiAuthenticator that points to the LDAP directory (Authentication > User Management > Realms).

- In the Domains tab, select a domain and move it into the Include in Two Factor Authentication column.

FortiAuthenticator Agent for Microsoft Windows contains the default domain "." which represents the local user. You can disable local user login by including the "." domain in the list of domains included in two factor authentication. When the "." domain is not included, login is enabled for local users.

This completes the configuration of the Windows agent.
You will need to log in to the host system in an online mode initially so that the agent can sync the offline tokens from FortiAuthenticator. Then the offline tokens will be cached.
|
|
Before the agent and FortiAuthenticator sync, make sure the host system time and the time on FortiAuthenticator are in sync. If the time is off by several minutes, the offline tokens will not work. |
Credential provider options
By un-checking the option for the default Permit Built-in Password Providers, you eliminate the ability for domain users to bypass the agent when logging in. It is enabled by default on the Agent for safety reasons. The Administrator has to un-check that option and save changes. Once completed, the default Windows credentials provider (e.g., "Other User" option) will no longer be available.

Offline token time/count size
The time/count remaining for offine token validation can be viewed when logging in. All tokens downloaded have enough offline tokens for the configured cache size plus the authentication window size. For example, if the HOTP cache size is 50, and the HOTP window is 10, you initially have 60 tokens. Note that when tokens are displayed but not submitted to the FortiAuthenticator, this can be fewer than 60 authentication attempts.


