Configuring Layer 3 roaming
Roaming is client's ability to maintain its association while it roams from one AP to another with as little latency as possible. When a wireless client connects to an access point, the managed wireless controller maintains client's database or information like MAC and IP addresses, security context and associations, quality of service (QoS) , the WLAN. The controller uses this information to forward frames and manage traffic to and from the wireless client.
As a wireless client roams from one department or floor to another, the design could mean that they cross an L3 boundary and experience latency. This is especially noticeable when running VoIp, Video or streaming services. To support this, you can configure a wireless network to enable Layer 3 roaming between different VLANs and subnets on the same or different Wireless Controller. A client connected to the SSID on one FortiAP can roam to the same SSID on another FortiAP managed by the same or different FortiGate Wireless Controller, and continue to use the same IP. When the client idles longer than a configurable amount of time (client-idle-rehome-timeout), the client will rehome, receive an address on the new subnet from the new FortiAP, and move to its new L3 segement.
This feature supports two topologies:
-
L3 roaming intra-controller
In this example, there are two FortiAPs (FAP1 and FAP2) being managed by a controller. The FortiAPs are located on different floors of the same building. Each FortiAP is mapped to a different VLAN, but are on the same SSID. The client roams from FAP1 to FAP 2 and the L3 handoff is handled by the controller. The client maintains the same IP address.

-
L3 roaming inter-controller
In this example, there are two controllers (Controller1 and Controller2) each managing a FortiAP (FAP1 and FAP2) respectively. The L3 client roams from Controller1's FAP1 to Controller 2's FAP2. Both FortiAPs have the same SSID, and each FAP has the SSID tied to a different VLAN. The client roams between the two FAPs and the L3 handoff is handled by Controller1 and Controller2's mobility tunnel. The client maintains the same IP address.
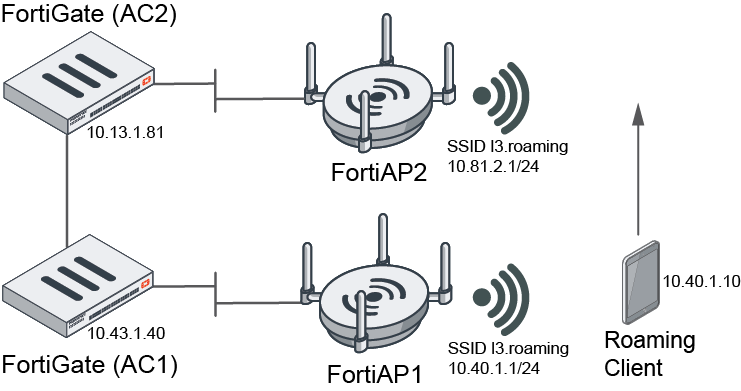
In addition, for the L3 roaming inter-controller topology, bridge mode SSIDs support two roaming modes:
-
Indirect Mode
In indirect mode, the L3 handoff is handled by the mobility tunnel between the FortiGate Wireless Controllers.

-
Direct Mode
In direct mode, the two FortiAPs must be able to reach each other with no NAT in the path and the L3 handoff occurs between the FortiAPs directly.

Note: Direct mode is preferred when feasible.
-

