What's new
FortiADC 6.1.1 offers the following new features:
System
Automation
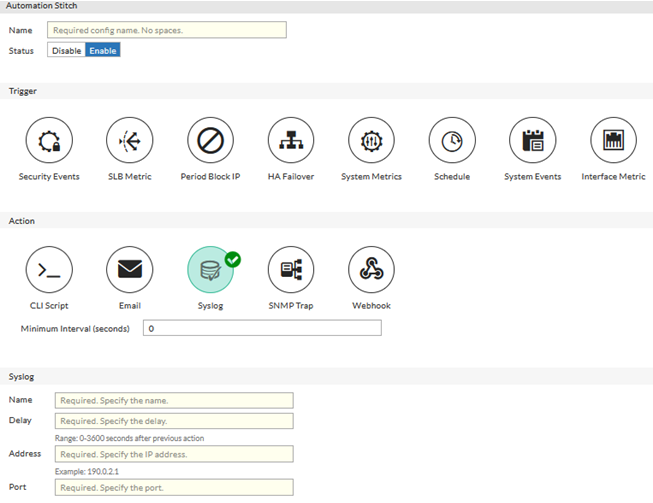
Automation Stitches can be used to automate certain actions in response to certain triggers. This includes sending alert emails in response to specific events, and allows for far more granular log-based alerting that Alert Emails configured under Log & Report.
Each Automation pairs an event trigger and one or more actions, which allows you to monitor your network and take appropriate action when the Security Fabric detects a threat. You can use Automation stitches to detect events from any source in the Security Fabric and apply actions to any destination.
For example, you can create the following Automation stitches:
-
Ban a compromised host’s IP address on FortiGate
-
Increase Server Capacity due to High Latency/Load
-
Increase Server Security during Web Attack
There are CLI changes relating to Automation. See "What's New" in FortiADC CLI Reference.
Matched part displayed in WAF logs
A matched part is added to WAF logs to indicate which part of the HTTP request/response has triggered the WAF event. This is helpful to identify the details for the attacks.

New hardware platforms
FortiADC1200F, 2200F, and 4200F are introduced in 6.1.1.
For more infomation, see FortiADC datasheets.
Server Load Balance
Next-hop routing for health check on L4 VS Direct Route mode
In L4 VS Direct Route deployment, you can set the VS IP on the loopback interface of real servers and publish the service on this IP.
In this mode, the service state on the real server (loopback interface IP) can't be detected. It is supported to forward the health check request to the real server as next hop, with the destination IP of VS IP. The real server will reply the request via routing just as it responses to the client's request.
Persisting new sessions to real servers in maintain mode
Normally when the real server is set to maintain mode, all new sessions will be routed to other active real servers, which may cause re-authentication in some deployment.
To solve this issue, an option is added to source address persistence. It allows new sessions to be persisted to the real server even when it is set to maintain mode.
L7 TCP/UDP VS Lua script
Lua script now supports for other L7 VS than HTTP VS, so that the actions that are not currently supported by built-in features can be performed. For example, you can use this script to manipulate request/response for Radius, ISO8583, etc.

For more information, see FortiADC Script Reference Guide.
GUI enhancement
The following enhancements are made in GUI:
-
SSL proxy statistics graphs are moved from Dashboard to FortiView (SSL proxy mode)
-
Password policy is displayed when admin password is created or edited.
-
New design for interface page to show interface status/avail.

