MAC access control with a WiFi network
This recipe demonstrates how to add device definitions to your FortiGate using Media Access Control (MAC) addresses. These definitions are then used to identify which devices can access the WiFi network.
By using a MAC address for identification, you can also assign a reserved IP for exclusive use by the device when it connects to the WiFi network.
Warning: Since MAC addresses can be easily spoofed, using MAC to control access should not be considered a security measure.

1. Finding the MAC address of a device
For Windows devices:
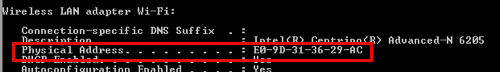
Open the command prompt and type ipconfig /all to display configuration information for all network connections.
The MAC address of your Windows device is the Physical Address, under information about the wireless adapter.
For Mac OS X devices:
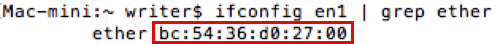
Open Terminal and type ifconfig en1 | grep ether.
Take note of the displayed MAC address.
For iOS devices:
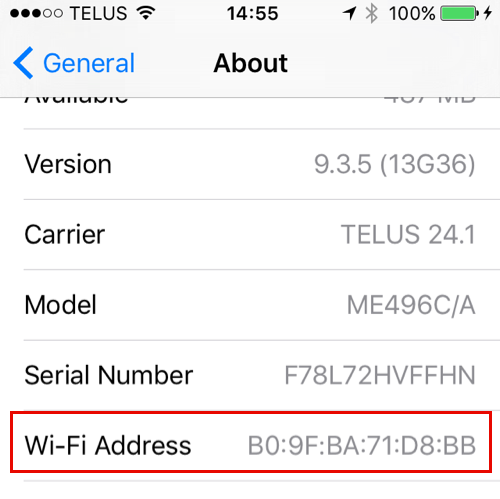
Open Settings > General> About.
The Wi-Fi Address is the MAC address of your iOS device.
For Android devices:
Open Settings > General > About Phone > Hardware Info.
Take note of the Wi-Fi MAC address of your Android device.

2. Defining a device using its MAC address
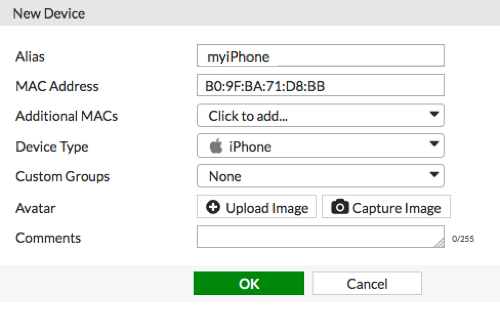
Go to User & Device > Custom Devices & Groups and create a new device definition.
Set MAC Address to the device's address and set the other fields as required. In the example, a device definition is created for an iPhone with the MAC Address B0:9F:BA:71:D8:BB.
Go to User & Device > Device Inventory. The new definition now appears in your device list. If you have enabled device identification on the wireless interface, device definitions will be created automatically. You can then use MAC addresses to identify which device a definition refers to.

3. Creating a device group
Go to User & Device > Custom Devices & Groups and create a new group.
Add the new device to the Members list.

4. Reserving an IP address for the device
Go to Network > Interfaces and edit the wireless interface. If the FortiAP is in bridge mode, you will need to edit the internal interface.
Under DHCP Server, expand Advanced. Create a new entry in the MAC Reservation + Access Control list that reserves an IP address within the DHCP range for the device's MAC address.

5. Creating a security policy for wireless traffic
Go to Policy & Objects > IPv4Policy and create a new policy.
Set Incoming Interface to your wireless interface, Source Device Type to the device group, and Outgoing Interface to the Internet-facing interface.
Ensure that NAT is turned on.

6. Results
Connect to the wireless network with a device that is a member of the device group. The device should be able to connect and allow Internet access.
Connection attempts from a device that is not a group member will fail.
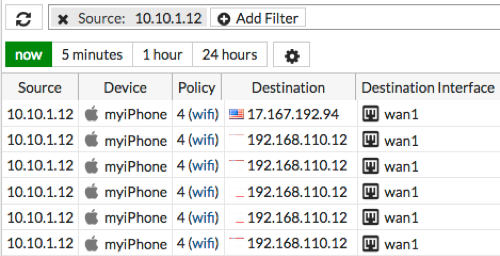
Go to FortiView > All Sessions and view the results for now. Filter the results using the reserved Source IP (in the example, 10.10.1.12), to verify that it is being used exclusively by the wireless device.
For further reading, check out Managing “bring your own device” in the FortiOS 5.4 Handbook.


