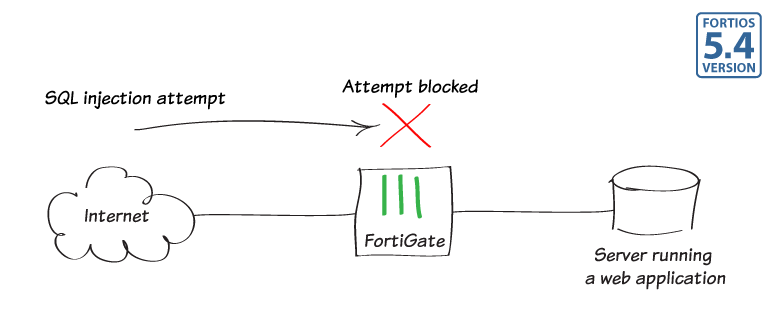
Protecting a server running web applications
In this recipe, you will use a Web Application Firewall profile to protect a server that is running a web application, such as web mail. In this example, the default profile will be targeted to block SQL injection attempts, as well as generic attacks.
Web Application Firewall is only available when Inspection Mode is Proxy-based.
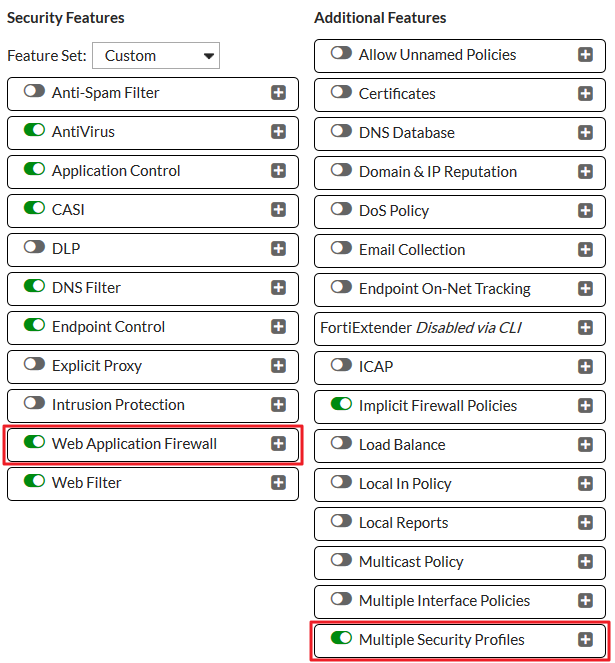
1. Enabling Web Application Firewall
Go to System > Feature Select and enable Web Application Firewall. Select Show More and enable Multiple Security Profiles.
Apply your changes.
2. Editing the default Web Application Firewall profile
Web Application Firewall profiles are created with a variety of options, called Signatures and Constraints. Once these options are enabled, Action can be set to Allow, Monitor, or Block, and Severity can be set to High, Medium, or Low.
You can also use a Web Application Firewall profile to enforce an HTTP method policy, which controls the HTTP method allowed when accessing websites that match the specified pattern.
Go to Security Profiles > Web Application Firewall and edit the default profile.
In this example, the signatures for SQL Injection (Extended) and Generic Attacks (Extended) have been enabled, with the Action set to Block and Severity set to High.
Trojans and Known Exploits are also blocked by default.

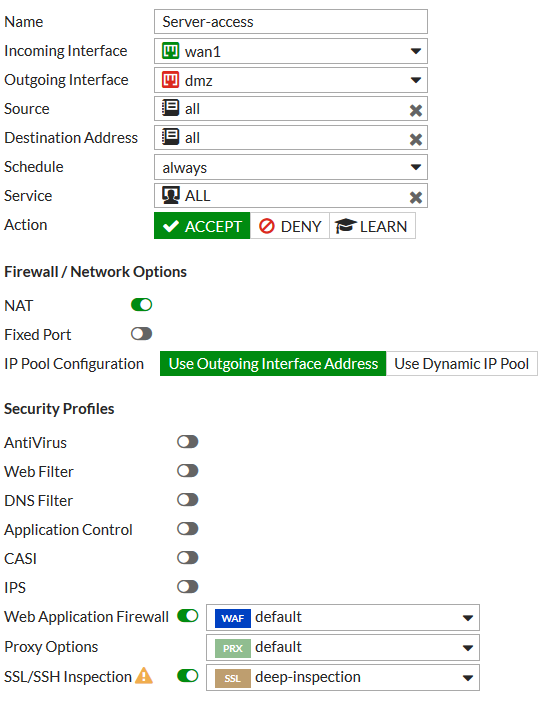
3. Applying the profile to a security policy
Go to Policy & Objects > IPv4 Policy and edit the policy that allows access to the web server.
Under Security Profiles, enable Web Application Firewall and set it to use the default profile. Set the appropriate Proxy Option and set SSH Inspection to use the deep-inspection profile.
4. Results
Use the following URL to simulate an attack on your web server, substituting the IP address of your server:
http:///<server IP>/index.php?username=1'%20or%20'1'%20=%20'1&password=1'%20or%20'1'%20=%20'1
An error message appears, stating that the web application firewall has blocked the traffic.

5. Offloading to a FortiWeb
If you have a FortiWeb, you may be able to offload the functions of the Web Application Control to your FortiWeb. To find out if this option is available, refer to the FortiOS or FortiWeb Release Notes for information about device compatibility.
Go to System > External Security Devices and enable HTTP Service. Enter your FortiWeb’s IP address.
If necessary, enable Authentication and enter the FortiWeb’s password.


